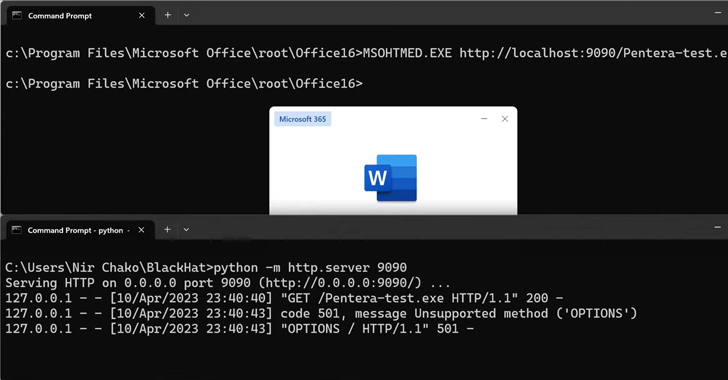
Cybersecurity researchers have found a set of 11 living-off-the-land binaries-and-scripts (LOLBAS) that might be maliciously abused by risk actors to conduct post-exploitation actions.
“LOLBAS is an assault technique that makes use of binaries and scripts which might be already a part of the system for malicious functions,” Pentera safety researcher Nir Chako mentioned. “This makes it exhausting for safety groups to tell apart between reputable and malicious actions, since they’re all carried out by trusted system utilities.”
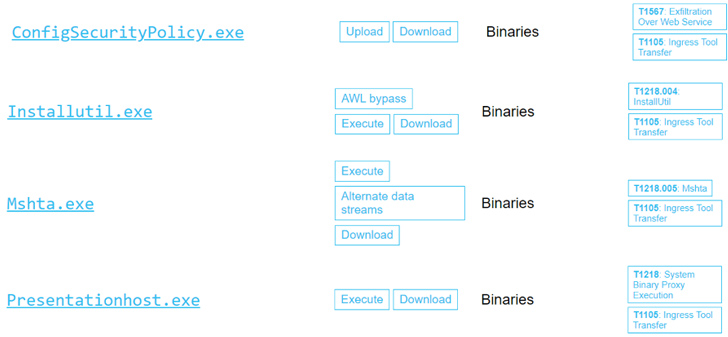
To that finish, the Israeli cybersecurity firm mentioned it uncovered 9 LOLBAS downloaders and three executors that would allow adversaries to obtain and execute “extra sturdy malware” on contaminated hosts.
This contains: MsoHtmEd.exe, Mspub.exe, ProtocolHandler.exe, ConfigSecurityPolicy.exe, InstallUtil.exe, Mshta.exe, Presentationhost.exe, Outlook.exe, MSAccess.exe, scp.exe, and sftp.exe.

“In a whole assault chain, a hacker will use a LOLBAS downloader to obtain extra sturdy malware,” Chako mentioned. “Then, they are going to attempt to execute it in a stealthy manner. LOLBAS executors permit attackers to execute their malicious instruments as a part of a reputable wanting course of tree on the system.”
That mentioned, Pentera famous that attackers might additionally use different executables from software program outdoors of these associated to Microsoft to attain related targets.
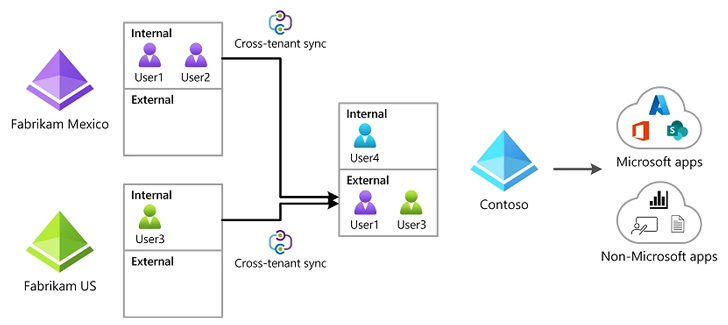
The findings come as Vectra disclosed a potential new assault vector that leverages Microsoft Entra ID (beforehand Azure Energetic Listing) cross-tenant synchronization (CTS) characteristic to facilitate lateral motion to different tenants assuming a privileged id has already been compromised within the cloud setting.
“An attacker working in a compromised setting can exploit an current CTS configuration tenant to maneuver laterally from one tenant to a different linked tenant,” the corporate mentioned. Alternatively, “an attacker working in a compromised tenant can deploy a rogue Cross Tenant Entry configuration to keep up persistent entry.”