As know-how continues to advance, making certain the safety of laptop programs, networks and purposes turns into more and more crucial. One of many methods wherein safety professionals can assess the safety posture of a complete digital ecosystem is by finishing up penetration testing, or pen testing for brief.
Penetration testing is a elementary apply for assessing and strengthening the safety posture of a corporation’s digital property and is performed with penetration testing instruments. Given the proliferation of those instruments, we’ve provide you with an inventory of the highest penetration testing instruments accessible in 2023, with their options, advantages and downsides.
Leap to:
See Additionally: Vulnerability scanning vs penetration testing: What’s the distinction?
Penetration testing software program comparability desk
Here’s a characteristic comparability of our shortlisted pen testing instruments and the way they stack up in opposition to one another.
| Compliance checks | Variety of exams coated | Open-source/web-based | Cross-platform compatibility | Reporting and documentation | |
|---|---|---|---|---|---|
| Astra | Sure | 8,000+ | Net | Sure | Sure |
| Acunetix | No | 7,000+ | Net | Sure | Sure |
| Intruder | Sure | Not specified | Net | Sure | Sure |
| Metasploit | Sure | 1,500+ | Each | Sure | No |
| Core Influence | Sure | Not specified | Net | Sure | Sure |
| Kali Linux | Sure | Not specified | Open-source | Sure | Sure |
| Wireshark | No | Not specified | Open-source | Sure | Sure |
| SQL Map | No | Not specified | Open-source | Sure | Sure |
Astra: Finest for numerous infrastructure

Astra is a penetration testing instrument resolution with a number of automated testing options that mix guide with automated penetration testing options for purposes, networks, API and blockchains. With over 8,000 exams supported, this instrument will help safety professionals examine vulnerabilities inside a system. Astra covers completely different sorts of penetration testing, together with net app pentest, cloud safety pentest and cellular app pentest.
As a complete penetration testing resolution, Astra covers many exams that may assist organizations meet compliance requirements. A few of the compliance requirements that Astra can examine embrace SOC2, GDPR and ISO 27001. The Astra instrument additionally integrates with GitLab, Jira and Slack and infuses safety right into a steady integration/steady deployment (CI/CD) pipeline.
Determine A
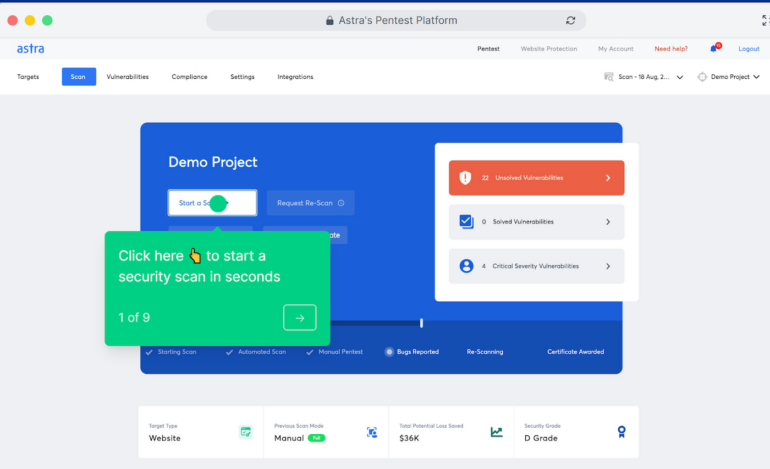
Pricing
Astra’s pricing is categorized into net app, cellular app and AWS cloud safety, every with completely different pricing.
- Net app: Scanner – $1,999/12 months, Pentest – $4,999/12 months and Enterprise – $6,999/12 months.
- Cellular: Pentest – $2,499/12 months and Enterprise – $3,999/12 months.
- AWS cloud safety: Beneath this are the Fundamental and Elite plans, and each require customers to talk to the gross sales crew for a quote.
Options
- Covers 8,000+ exams scanning.
- Covers all exams required for ISO 27001, HIPAA, SOC2 and GDPR.
- Integration with GitLab, GitHub, Slack and Jira.
- PWA/SPAs apps scanning help.
- Assist via Slack and Microsoft Groups.
Execs
- Helps publicly verifiable pentest certificates, which might be shared with customers.
- Provides one of many widest testing coverages (over 8,000).
- Assessments are automated with AI/ML.
- Assist by way of Slack or Microsoft Groups.
Cons
- What is meant to be a free trial is charged at $1 per day.
- Assist by way of Slack and MS Groups is barely accessible on the Enterprise plan.
Acunetix: Finest for pentest automation

Acunetix by Invicti is a robust pen testing instrument for net purposes. The answer is filled with scanning utilities that may assist penetration check groups rapidly get an perception into over 7,000 net utility vulnerabilities and supply an in depth report masking the scope of vulnerability.
A few of the notable vulnerabilities Acunetix can detect embrace XSS, SQL injections, uncovered databases, out-of-band vulnerabilities and misconfigurations.
Acunetix comes with a dashboard that may type vulnerabilities into lessons, comparable to crucial, excessive, medium and low. The instrument is written in C++ and may run on Microsoft Home windows, Linux, macOS and the cloud.
Determine B
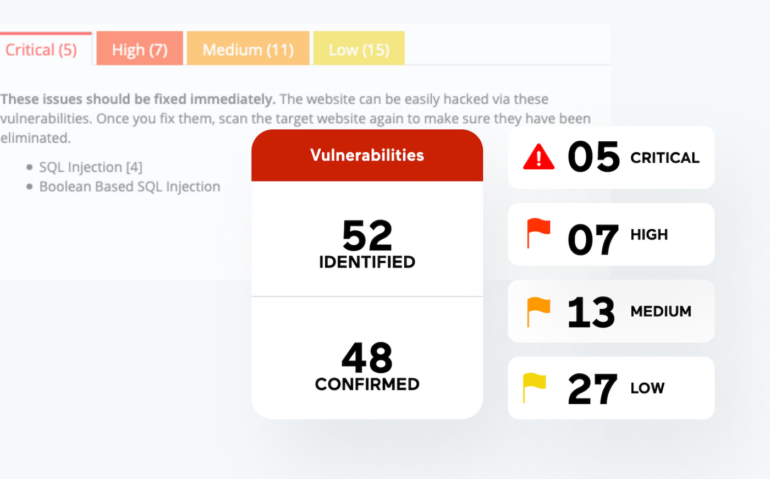
Pricing
Contact Acunetix for a quote.
Options
- Vulnerability categorization into an order of severity.
- Over 7,000 net app vulnerabilities are supported.
- Covers the OWASP Prime 10 customary for builders and net utility safety.
- Scan scheduling performance.
- Compatibility with issue-tracking instruments like Jira and GitLab.
Execs
- Detected vulnerabilities are categorized in keeping with their severity degree.
- Helps reporting and documentation.
- Over 7,000 vulnerability exams are a broad protection.
- Customers can schedule one-time or recurring scans.
- Helps concurrent scanning of a number of environments.
Cons
- No pricing particulars for customers.
- Absence of a free trial.
Core Influence: Finest for collaboration

Core Influence, now part of Fortra, ranks as one of many oldest penetration testing instruments which have developed alongside the present calls for of a testing setting. The software program can facilitate the method of assault replication throughout endpoints, community infrastructures, net and purposes to disclose exploited vulnerabilities and supply strategies for remediation.
Core Influence reduces the necessity for guide configuration throughout set up and testing. Customers can simply outline check scope and set testing parameters, and Core Influence does the remainder. As well as, this instrument can generate an assault map, giving customers a real-time report of assault actions throughout testing.
Determine E
Pricing
Core Influence has three pricing plans:
- Fundamental: Begins at $9,450/person per 12 months.
- Professional: Begins at $12,600/person per 12 months.
- Enterprise: Request a quote.
Options
- Automated Fast Penetration Assessments (RPTs).
- Multi-vector testing functionality that features community, consumer and net.
- Vulnerability validation of third-party scanner outcomes.
- Centralizes pen testing, from data gathering to reporting.
- Pen testing covers community safety, net utility, IoT safety and cloud safety.
Execs
- Makes use of automation wizards to find, check and report.
- Free trial accessible.
- Provides broader cybersecurity providers.
- New customers can study concerning the instrument by way of a demo.
Cons
- Pricing could be very costly.
- Free trial doesn’t state how lengthy the trial interval lasts.
Kali Linux: Finest for technical customers

Kali Linux is an open-source pen testing resolution that runs on the Debian-based Linux distribution. The instrument has superior multi-platform options that may help testing on cellular, desktop, Docker, subsystems, digital machines and naked metallic.
As an open-source instrument, professionals can simply customise it to match their testing conditions. There may be detailed documentation on utilizing Kali’s metapackages to generate software program variations for particular testing functions. Kali additionally saves customers the time wanted to arrange instruments manually by including an automatic configuration system that optimizes the instrument in keeping with completely different use instances.
Determine F

Pricing
It’s accessible freed from cost.
Options
- Metapackages can be utilized for particular duties.
- Provides Stay USB Boot for simple booting from a USB gadget.
- Helps over 600 penetration testing utilities.
- Open-source improvement mannequin might be accessed on GitHub.
Execs
- Helps a wide selection of variations.
- Out there at no cost.
- Programs and documentation can be found for brand new customers.
- Multi-language help.
Cons
- Principally superb for superior Linux customers.
Wireshark: Finest for Unix OS

The Wireshark instrument can analyze and check a corporation’s community protocol for threats. The instrument is a multi-platform penetration testing utility with helpful options comparable to stay seize, offline and VoIP evaluation.
As an open-source instrument, Wireshark gives numerous help for its customers via documentation, webinars and video tutorials. The instrument additionally gives decryption options for arrays of protocols comparable to Kerberos, SSL/TLS and WEP.
Determine G
Pricing
It’s accessible at no cost.
Options
- Out there for UNIX and Home windows.
- Seize stay packet information from a community interface.
- Show filters for sorting via and analyzing site visitors streams.
- Helps offline and VoIP evaluation.
Execs
- It’s accessible at no cost and is open supply.
- There may be an export objects perform for exporting check outcomes.
- It may be used for decryption throughout a variety of protocols.
- High quality documentation for brand new customers.
Cons
- Setup could be too technical for brand new customers.
- Restricted automated functionalities.
SQLMap: Finest for detecting SQL injection assaults

For open-source lovers, SQLMap is a wonderful penetration testing instrument for detecting and exploiting SQL injections in purposes. Penetration testers make the most of the instrument to hack databases and perceive the depth of vulnerabilities.
As well as, SQLMap has a testing engine that may run a number of SQL injection assaults concurrently, decreasing the time spent working the check. Some notable servers supported on the platform are Microsoft Entry, IBM DB2, SQLite and MySQL.
Additionally it is a cross-platform instrument, supporting macOS, Linux and Home windows working programs.
Determine H
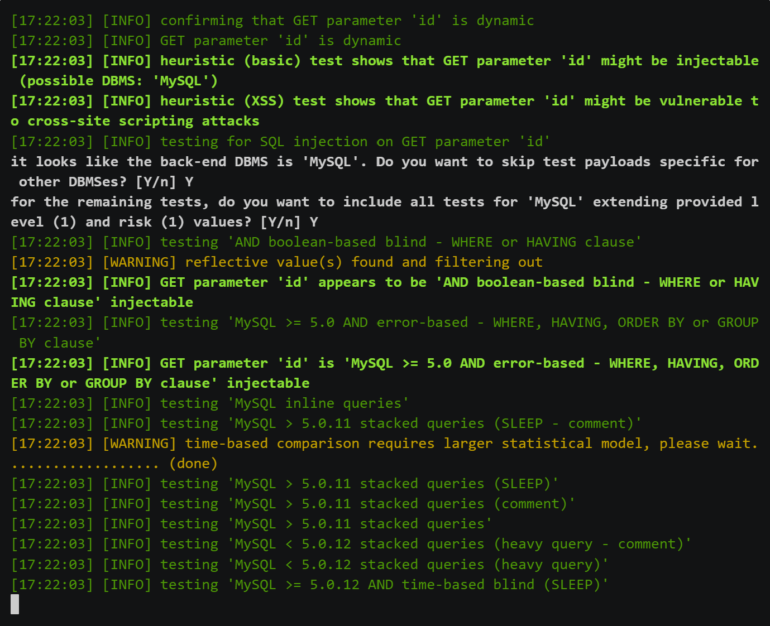
Pricing
Out there at no cost.
Options
- Helps a number of SQL injection methods.
- Computerized recognition of password hash codecs.
- Assist for cracking passwords utilizing a dictionary-based assault.
- Can execute arbitrary instructions and retrieve their customary output.
Execs
- Covers a broad vary of SQL injection methods.
- Appropriate with a number of database administration programs like MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Entry, IBM DB2 and extra.
- Out there at no cost.
- Has good documentation.
Cons
- Solely appropriate for command-line customers.
Options of penetration testing instruments
Penetration testing options supply a number of options and use instances relying on the target of the person. Beneath are the important thing options of penetration testing options.
Vulnerability scanning
Penetration testing typically entails vulnerability scans that seek for weaknesses and loopholes in software program purposes, networks and programs. These scans can detect potential vulnerabilities, comparable to outdated software program variations, misconfigurations and identified safety flaws.
Community mapping and reconnaissance
Community mapping and reconnaissance discuss with the method of gathering data and creating a visible illustration of a community’s infrastructure and its related units. Earlier than launching an assault, hackers sometimes collect details about their goal. Equally, penetration testing instruments help with reconnaissance actions by mapping networks, figuring out lively hosts and gathering details about the goal infrastructure. This characteristic aids safety professionals in understanding the group’s digital footprint and potential entry factors for attackers.
Site visitors evaluation and sniffing
Some penetration testing instruments can analyze community site visitors and seize packets. This functionality permits safety professionals to watch and examine community communication, determine potential vulnerabilities and detect any suspicious or malicious actions. By analyzing community site visitors, organizations can acquire helpful insights into the safety posture of their programs.
Reporting and documentation
Efficient communication of vulnerabilities and beneficial mitigation methods is crucial within the penetration testing course of. Penetration testing instruments supply reporting and documentation options to generate complete experiences detailing recognized vulnerabilities, steps taken throughout testing and proposals for remediation. These experiences help within the prioritization and implementation of safety measures and compliance verification processes.
Customization options
Totally different organizations have distinctive safety necessities. These instruments typically supply customization choices and extensibility options, permitting safety professionals to tailor the testing course of to their particular wants. Customization empowers organizations to give attention to their most crucial property and assess vulnerabilities which can be particular to their setting.
How do I select the perfect penetration testing software program for my enterprise?
Given the avalanche of pen testing instruments accessible to safety professionals, choosing the proper pen testing software program is usually a problem. Listed below are key concerns that will help you select the perfect penetration testing software program in your particular enterprise wants.
Establish your pen testing objectives
Earlier than getting began with the choice course of, clearly outline your aims for conducting penetration testing. Decide what you goal to attain via the testing course of, comparable to figuring out vulnerabilities in your programs, assessing the effectiveness of your safety controls, or assembly regulatory compliance necessities. Understanding your objectives will provide help to slender down the software program choices that align together with your particular necessities. As might be seen from our comparability desk, a few of the instruments are higher than others for various eventualities.
Contemplate testing methodologies
Penetration testing might be performed utilizing completely different methodologies, comparable to black field, white field, or grey field testing. Consider the software program’s functionality to help the specified testing methodology. Some instruments might concentrate on particular sorts of testing, so remember to examine that the software program aligns together with your most popular method. Flexibility in supporting varied testing methodologies might be useful if you happen to require completely different approaches for various programs or eventualities.
Contemplate ease of use and person interface
It is best to contemplate the user-friendliness of the software program and the intuitiveness of its person interface. Penetration testing entails complicated processes, so it’s essential to decide on a instrument that’s straightforward to navigate and perceive. A well-designed person interface and clear documentation can considerably improve your expertise with the software program and enhance productiveness. Whereas a few of the penetration testing instruments we shortlisted supply each GUI and command-line interfaces, some solely help the command-line interface. Though each interfaces result in the identical consequence, superior customers could also be extra comfy with the command-line interface than common customers.
Contemplate compatibility and integration choices
Assess the compatibility of the software program together with your current IT infrastructure. Make sure that the instrument can seamlessly combine together with your programs, networks, and purposes with out inflicting disruptions. Compatibility concerns embrace the working programs, databases, and programming languages supported by the software program. Moreover, confirm whether or not the instrument can combine with different safety options you at the moment use, comparable to vulnerability administration platforms or safety data and occasion administration programs.
Test for safety and compliance
Given the delicate nature of penetration testing be sure that the software program itself adheres to trade finest practices. Assess the software program’s skill to deal with confidential data securely and preserve the privateness of your testing actions. Moreover, contemplate whether or not the instrument helps compliance necessities particular to your trade or location.
Finest practices for penetration testing
Definition of scope and finances
Generally you assume it’s superb to check your complete system setting; nevertheless, defining the price of testing your complete software program ecosystem might persuade you in any other case. Each group has excessive and low vulnerability factors. Excessive-risk factors are the areas that malicious actors can simply exploit. They’ll embrace utility code base, configuration recordsdata and working programs. Realizing the scope of the check beforehand is a wonderful manner to assist the group plan a penetration testing finances.
Monetary and buyer information ought to be included
Many organizations deal with excessive volumes of monetary and buyer data of their database. This set of knowledge is essential to any group and have to be protected in any respect prices in opposition to breaches. There ought to be complete penetration testing on these information sources and the software program instruments that usually connect with them.
Contemplate testing remotely accessible sources
Your group’s penetration testing plans mustn’t exclude your distant sources and staff. Organizations that help distant roles generally present distant entry to helpful sources, which might be an entry level for hackers as a result of poor safety monitoring. Distant sources with restricted safety monitoring programs ought to be coated within the penetration testing.
Methodology
To curate our listing of the perfect penetration testing instruments, we performed in depth analysis by extracting data from official web sites, product documentation, case research, and person suggestions from dependable third-party overview websites. The factors that knowledgeable our selection embrace the important thing options and functionalities coated by the pen testing resolution, the neighborhood across the software program, the person base/reputation of the software program, ease of use and the standard of documentation supplied by the software program. All these components knowledgeable our choice course of for this overview.

