Charming Kitten, the nation-state actor affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), has been attributed to a bespoke spear-phishing marketing campaign that delivers an up to date model of a fully-featured PowerShell backdoor known as POWERSTAR.
“There have been improved operational safety measures positioned within the malware to make it harder to research and acquire intelligence,” Volexity researchers Ankur Saini and Charlie Gardner stated in a report printed this week.
The menace actor is one thing of an knowledgeable in terms of using social engineering to lure targets, typically crafting tailor-made faux personas on social media platforms and interesting in sustained conversations to construct rapport earlier than sending a malicious hyperlink. It is also tracked underneath the names APT35, Cobalt Phantasm, Mint Sandstorm (previously Phosphorus), and Yellow Garuda.
Current intrusions orchestrated by Charming Kitten have made use of different implants equivalent to PowerLess and BellaCiao, suggesting that the group is using an array of espionage instruments at its disposal to appreciate its strategic targets.
POWERSTAR is one other addition to the group’s arsenal. Additionally known as CharmPower, the backdoor was first publicly documented by Examine Level in January 2022, uncovering its use in reference to assaults weaponizing the Log4Shell vulnerabilities in publicly-exposed Java functions.
It has since been put to make use of in no less than two different campaigns, as documented by PwC in July 2022 and Microsoft in April 2023.
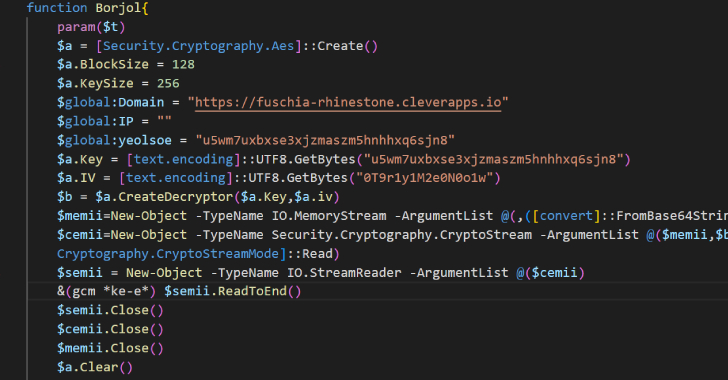
Volexity, which detected a rudimentary variant of POWERSTAR in 2021 distributed by a malicious macro embedded in DOCM file, stated the Might 2023 assault wave leverages an LNK file inside a password-protected RAR file to obtain the backdoor from Backblaze, whereas additionally taking steps to hinder evaluation.
“With POWERSTAR, Charming Kitten sought to restrict the chance of exposing their malware to evaluation and detection by delivering the decryption technique individually from the preliminary code and by no means writing it to disk,” the researchers stated.
“This has the added bonus of appearing as an operational guardrail, as decoupling the decryption technique from its command-and-control (C2) server prevents future profitable decryption of the corresponding POWERSTAR payload.”
The backdoor comes with an intensive set of options that allow it to remotely execute PowerShell and C# instructions, arrange persistence, acquire system data, and obtain and execute extra modules to enumerate operating processes, seize screenshots, seek for recordsdata matching particular extensions, and monitor if persistence parts are nonetheless intact.
Additionally improved and expanded from the sooner model is the cleanup module that is designed to erase all traces of the malware’s footprint in addition to delete persistence-related registry keys. These updates level to Charming Kitten’s continued efforts to refine its strategies and evade detection.
Volexity stated it additionally detected a distinct variant of POWERSTAR that makes an attempt to retrieve a hard-coded C2 server by decoding a file saved on the decentralized InterPlanetary Filesystem (IPFS), signaling an try and make its assault infrastructure extra resilient.
The event coincides with a MuddyWater’s (aka Static Kitten) use of beforehand undocumented command-and-control (C2) framework known as PhonyC2 to ship malicious payload to compromised hosts.
“The final phishing playbook utilized by Charming Kitten and the general goal of POWERSTAR stay constant,” the researchers stated. “The references to persistence mechanisms and executable payloads inside the POWERSTAR Cleanup module strongly suggests a broader set of instruments utilized by Charming Kitten to conduct malware-enabled espionage.”

.jpg)