A complicated stealer-as-a-ransomware menace dubbed RedEnergy has been noticed within the wild focusing on vitality utilities, oil, gasoline, telecom, and equipment sectors in Brazil and the Philippines via their LinkedIn pages.
The malware “possesses the flexibility to steal data from numerous browsers, enabling the exfiltration of delicate information, whereas additionally incorporating completely different modules for finishing up ransomware actions,” Zscaler researchers Shatak Jain and Gurkirat Singh mentioned in a latest evaluation.
The purpose, the researchers famous, is to couple information theft with encryption with the purpose of inflicting most harm to the victims.
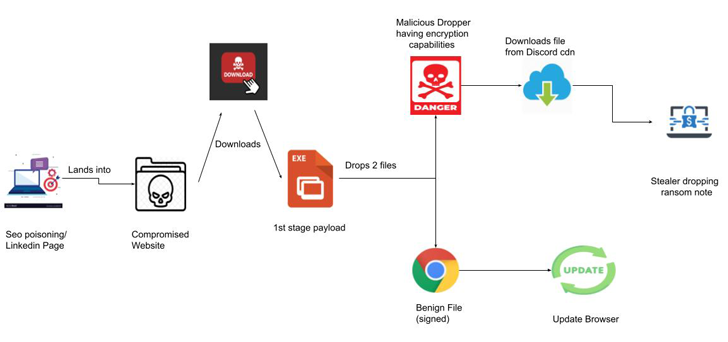
The start line for the multi-stage assault is a FakeUpdates (aka SocGholish) marketing campaign that methods customers into downloading JavaScript-based malware below the guise of net browser updates.
What makes it novel is the usage of respected LinkedIn pages to focus on victims, redirecting customers clicking on the web site URLs to a bogus touchdown web page that prompts them to replace their net browsers by clicking on the suitable icon (Google Chrome, Microsoft Edge, Mozilla Firefox, or Opera), doing so which ends up in the obtain a malicious executable.
Following a profitable breach, the malicious binary is used as a conduit to arrange persistence, carry out the precise browser replace, and likewise drop a stealer able to covertly harvesting delicate data and encrypting the stolen recordsdata, leaving the victims liable to potential information loss, publicity, and even the sale of their helpful information.
Zscaler mentioned it found suspicious interactions going down over a File Switch Protocol (FTP) connection, elevating the likelihood that helpful information is being exfiltrated to actor-controlled infrastructure.
Within the ultimate stage, RedEnergy’s ransomware part proceeds to encrypt the consumer’s information, suffixing the “.FACKOFF!” extension to every encrypted file, deleting current backups, and dropping a ransom word in every folder.
Victims are anticipated to make a cost of 0.005 BTC (about $151) to a cryptocurrency pockets talked about within the word to regain entry to the recordsdata. RedEnergy’s twin capabilities as a stealer and ransomware characterize an evolution of the cybercrime panorama.
The event additionally follows the emergence of a brand new RAT-as-a-ransomware menace class wherein distant entry trojans reminiscent of Venom RAT and Anarchy Panel RAT have been outfitted with ransomware modules to lock numerous file extensions behind encryption obstacles.
“It’s essential for people and organizations to train utmost warning when accessing web sites, particularly these linked from LinkedIn profiles,” the researchers mentioned. “Vigilance in verifying the authenticity of browser updates and being cautious of surprising file downloads is paramount to guard towards such malicious campaigns.”