
Safety researchers found two malicious file administration functions on Google Play with a collective set up rely of over 1.5 million that collected extreme person information that goes nicely past what’s wanted to supply the promised performance.
The apps, each from the identical writer, can launch with none interplay from the person to steal delicate information and ship it to servers in China.
Regardless of being reported to Google, the 2 apps proceed to be obtainable in Google Play on the time of publishing.
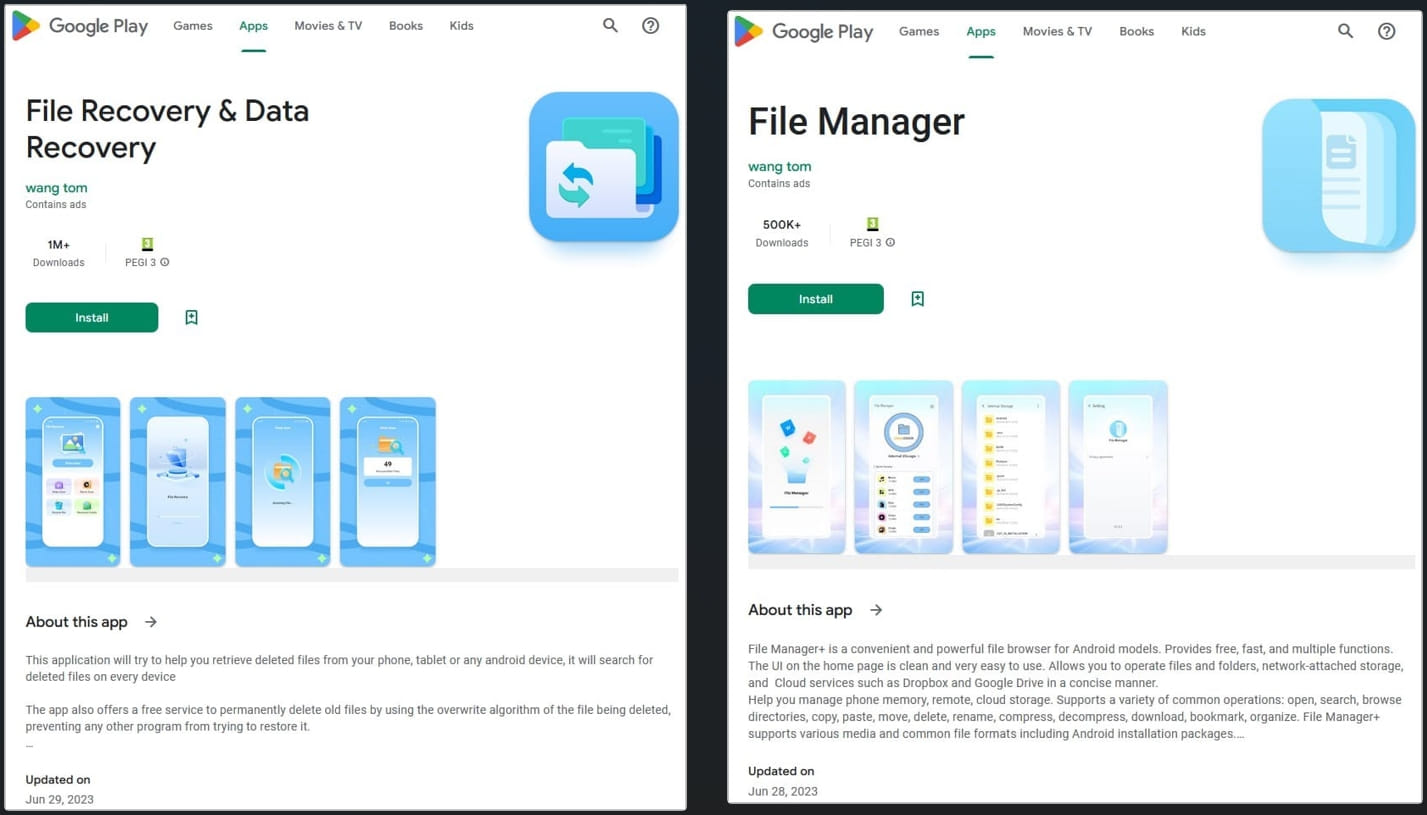
File Restoration and Information Restoration, recognized as “com.spot.music.filedate” on units, has at the least 1 million installs. The set up rely for File Supervisor reads at the least 500,000 and it may be recognized on units as “com.file.field.grasp.gkd.”
The 2 apps have been found by the behavioral evaluation engine from cellular safety options firm Pradeo and their description states that they don’t acquire any person information from the machine on the Information Security part of their Google Play entry
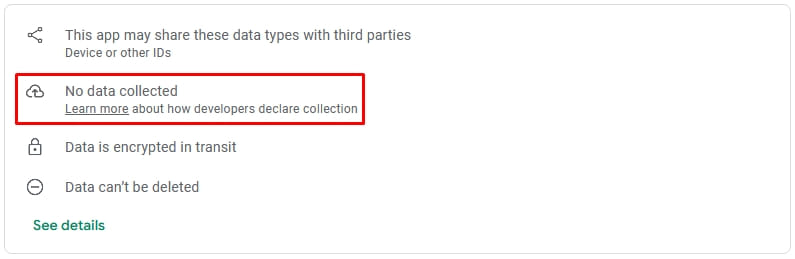
Nevertheless, Pradeo discovered that the cellular apps exfiltrate the next information from the machine:
- Customers’ contact checklist from on-device reminiscence, linked e-mail accounts, and social networks.
- Footage, audio, and video which are managed or recovered from inside the functions.
- Actual-time person location
- Cell nation code
- Community supplier title
- Community code of the SIM supplier
- Working system model quantity
- Machine model and mannequin
Whereas the apps might need a respectable motive to gather a number of the above to make sure good efficiency and compatibility, a lot of the collected information will not be vital for file administration or information restoration capabilities. To make issues worse, this information is collected secretly and with out gaining the person’s consent.
Pradeo provides that the 2 apps conceal their dwelling display icons to make it harder to seek out and take away them. They will additionally abuse the permissions the person approves throughout set up to restart the machine and launch within the background.
It’s seemingly that the writer used emulators or set up farms to bloat recognition and make their merchandise seem extra reliable, Pradeo speculates.
This concept is supported by the truth that the variety of person opinions on the Play retailer is approach too small in comparison with the reported userbase.
It’s at all times beneficial to examine person opinions earlier than putting in an app, take note of the requested permissions throughout app set up, and solely belief software program printed by respected builders.
Replace 7/6/23 5:51 PM ET: Google shared the next assertion with BleepingComputer and mentioned that they eliminated the apps from Google Play.
“These apps have been faraway from Google Play. Google Play Shield protects customers from apps identified to include this malware on Android units with Google Play Providers, even when these apps come from different sources exterior of Play.”
