Companies working within the Latin American (LATAM) area are the goal of a brand new Home windows-based banking trojan referred to as TOITOIN since Might 2023.
“This refined marketing campaign employs a trojan that follows a multi-staged an infection chain, using specifically crafted modules all through every stage,” Zscaler researchers Niraj Shivtarkar and Preet Kamal mentioned in a report printed final week.
“These modules are customized to hold out malicious actions, resembling injecting dangerous code into distant processes, circumventing Person Account Management by way of COM Elevation Moniker, and evading detection by Sandboxes by means of intelligent strategies like system reboots and father or mother course of checks.”
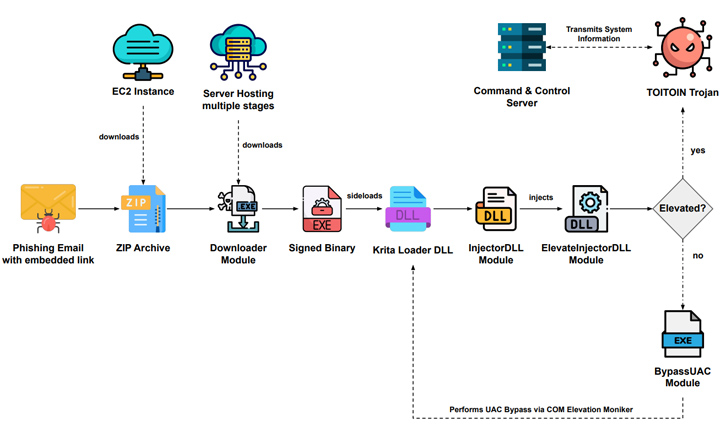
The six-stage endeavor has all of the hallmarks of a well-crafted assault sequence, starting with a phishing e mail containing an embedded hyperlink that factors to a ZIP archive hosted on an Amazon EC2 occasion to evade domain-based detections.
The e-mail messages leverage an invoice-themed lure to trick unwitting recipients into opening them, thereby activating the an infection. Throughout the ZIP archive is a downloader executable that is engineered to arrange persistence by the use of an LNK file within the Home windows Startup folder and talk with a distant server to retrieve six next-stage payloads within the type of MP3 recordsdata.
The downloader can be chargeable for producing a Batch script that restarts the system after a 10-second timeout. That is achieved in order to “evade sandbox detection because the malicious actions happen solely after the reboot,” the researchers mentioned.
Included among the many fetched payloads is “icepdfeditor.exe,” a legitimate signed binary by ZOHO Company Personal Restricted, which, when executed, sideloads a rogue DLL (“ffmpeg.dll”) codenamed the Krita Loader.
The loader, for its half, is designed to decode a JPG file downloaded alongside the opposite payloads and launch one other executable often known as the InjectorDLL module that reverses a second JPG file to kind what’s referred to as the ElevateInjectorDLL module.
The InjectorDLL element subsequently strikes to inject ElevateInjectorDLL into the “explorer.exe” course of, following which a Person Account Management (UAC) bypass is carried out, if required, to raise the method privileges and the TOITOIN Trojan is decrypted and injected into the “svchost.exe” course of.
🔐 PAM Safety – Skilled Options to Safe Your Delicate Accounts
This expert-led webinar will equip you with the data and techniques it is advisable rework your privileged entry safety technique.
“This method permits the malware to control system recordsdata and execute instructions with elevated privileges, facilitating additional malicious actions,” the researchers defined.
TOITOIN comes with capabilities to collect system data in addition to harvest information from put in internet browsers resembling Google Chrome, Microsoft Edge and Web Explorer, Mozilla Firefox, and Opera. Moreover, it checks for the presence of Topaz On-line Fraud Detection (OFD), an anti-fraud module built-in into banking platforms within the LATAM area.
The character of the responses from the command-and-control (C2) server is presently not identified on account of the truth that the server is not out there.
“By means of misleading phishing emails, intricate redirect mechanisms, and area diversification, the risk actors efficiently ship their malicious payload,” the researchers mentioned. “The multi-staged an infection chain noticed on this marketing campaign includes the usage of custom-developed modules that make use of numerous evasion strategies and encryption strategies.”