Cybersecurity researchers stated they’ve found what they are saying is the primary open-source software program provide chain assaults particularly focusing on the banking sector.
“These assaults showcased superior methods, together with focusing on particular elements in internet belongings of the sufferer financial institution by attaching malicious functionalities to it,” Checkmarx stated in a report printed final week.
“The attackers employed misleading ways comparable to making a pretend LinkedIn profile to look credible and customised command-and-control (C2) facilities for every goal, exploiting reliable companies for illicit actions.”
The npm packages have since been reported and brought down. The names of the packages weren’t disclosed.
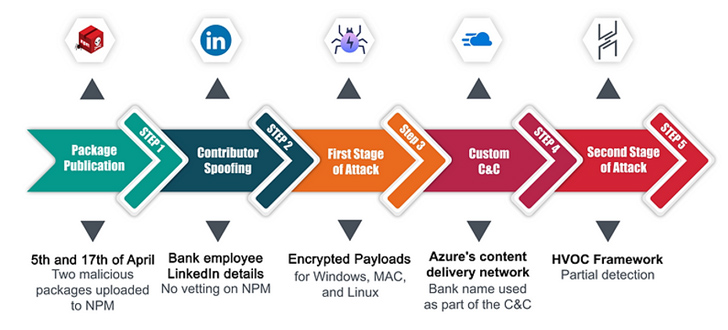
Within the first assault, the malware writer is alleged to have uploaded a few packages to the npm registry in early April 2023 by posing as an worker of the goal financial institution. The modules got here with a preinstall script to activate the an infection sequence. To finish the ruse, the menace actor behind it created a pretend LinkedIn web page.
As soon as launched, the script decided the host working system to see if it was Home windows, Linux, or macOS, and proceeded to obtain a second-stage malware from a distant server by utilizing a subdomain on Azure that included the title of the financial institution in query.
“The attacker cleverly utilized Azure’s CDN subdomains to successfully ship the second-stage payload,” Checkmarx researchers stated. “This tactic is especially intelligent as a result of it bypasses conventional deny record strategies, as a result of Azure’s standing as a reliable service.”
The second-stage payload used within the intrusion is Havoc, an open-source command-and-control (C2) framework that has more and more come beneath the radar of malicious actors seeking to sidestep detection stemming from the usage of Cobalt Strike, Sliver, and Brute Ratel.
In an unrelated assault detected in February 2023 focusing on a distinct financial institution, the adversary uploaded to npm a bundle that was “meticulously designed to mix into the web site of the sufferer financial institution and lay dormant till it was prompted to spring into motion.”
Particularly, it was engineered to covertly intercept login information and exfiltrate the main points to an actor-controlled infrastructure.
“Provide chain safety revolves round defending your complete technique of software program creation and distribution, from the start levels of improvement to the supply to the top consumer,” the corporate stated.
“As soon as a malicious open-source bundle enters the pipeline, it is basically an instantaneous breach – rendering any subsequent countermeasures ineffective. In different phrases, the injury is finished.”
The event comes because the Russian-speaking cybercrime group RedCurl breached an unnamed main Russian financial institution and an Australian firm in November 2022 and Could 2023 to siphon company secrets and techniques and worker info as a part of a complicated phishing marketing campaign, Group-IB’s Russian arm, F.A.C.C.T., stated.
“Over the previous 4 and a half years, the Russian-speaking group Purple Curl […] has carried out at the very least 34 assaults on firms from the UK, Germany, Canada, Norway, Ukraine, and Australia,” the corporate stated.
Protect Towards Insider Threats: Grasp SaaS Safety Posture Administration
Apprehensive about insider threats? We have you coated! Be a part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
“Greater than half of the assaults – 20 – fell on Russia. Among the many victims of cyber spies had been building, monetary, consulting firms, retailers, banks, insurance coverage, and authorized organizations.”
Monetary establishments have additionally been on the receiving finish of assaults leveraging a web-inject toolkit known as drIBAN to carry out unauthorized transactions from a sufferer’s laptop in a way that circumvents identification verification and anti-fraud mechanisms adopted by banks.
“The core performance of drIBAN is the ATS engine (Automated Switch System),” Cleafy researchers Federico Valentini and Alessandro Strino famous in an evaluation launched on July 18, 2023.
“ATS is a category of internet injects that alters on-the-fly reliable banking transfers carried out by the consumer, altering the beneficiary and transferring cash to an illegitimate checking account managed by TA or associates, that are then answerable for dealing with and laundering the stolen cash.”