A telephone surveillance app referred to as Spyhide is stealthily amassing personal telephone knowledge from tens of 1000’s of Android gadgets around the globe, new knowledge exhibits.
Spyhide is a widely-used stalkerware (or spouseware) app that’s planted on a sufferer’s telephone, usually by somebody with data of their passcode. The app is designed to remain hidden on a sufferer’s telephone’s house display screen, making it tough to detect and take away. As soon as planted, Spyhide silently and regularly uploads the telephone’s contacts, messages, photographs, name logs and recordings, and granular location in real-time.
Regardless of their stealth and broad entry to a sufferer’s telephone knowledge, stalkerware apps are notoriously buggy and are recognized to spill, leak, or in any other case put victims’ stolen personal knowledge at additional threat of publicity, underlying the dangers that telephone surveillance apps pose.
Now, Spyhide is the most recent spy ware operation added to that rising record.
Switzerland-based hacker maia arson crimew mentioned in a weblog put up that the spy ware maker uncovered a portion of its growth atmosphere, permitting entry to the supply code of the web-based dashboard that abusers use to view the stolen telephone knowledge of their victims. By exploiting a vulnerability within the dashboard’s shoddy code, crimew gained entry to the back-end databases, exposing the inside workings of the secretive spy ware operation and its suspected directors.
Crimew offered TechCrunch with a duplicate of Spyhide’s text-only database for verification and evaluation.
Years of stolen telephone knowledge
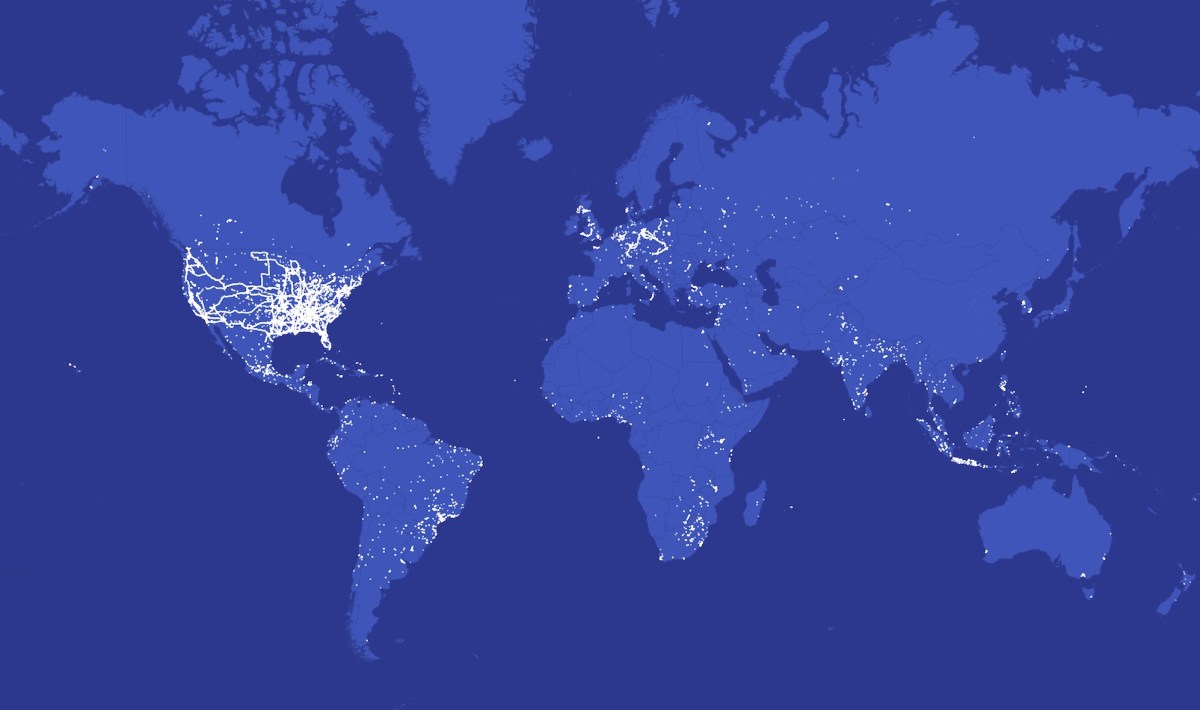
Spyhide’s database contained detailed data of about 60,000 compromised Android gadgets, relationship again to 2016 as much as the date of exfiltration in mid-July. These data included name logs, textual content messages, and exact location historical past relationship again years, in addition to details about every file, resembling when a photograph or video was taken and uploaded, and when calls had been recorded and for a way lengthy.
TechCrunch fed shut to 2 million location knowledge factors into an offline geospatial and mapping software program, permitting us to visualise and perceive the spy ware’s international attain.
Our evaluation exhibits Spyhide’s surveillance community spans each continent, with clusters of 1000’s of victims in Europe and Brazil. The U.S. has greater than 3,100 compromised gadgets, a fraction of the overall quantity worldwide, but these U.S. victims are nonetheless a number of the most surveilled victims on the community by the amount of location knowledge alone. One U.S. gadget compromised by Spyhide had quietly uploaded greater than 100,000 location knowledge factors.
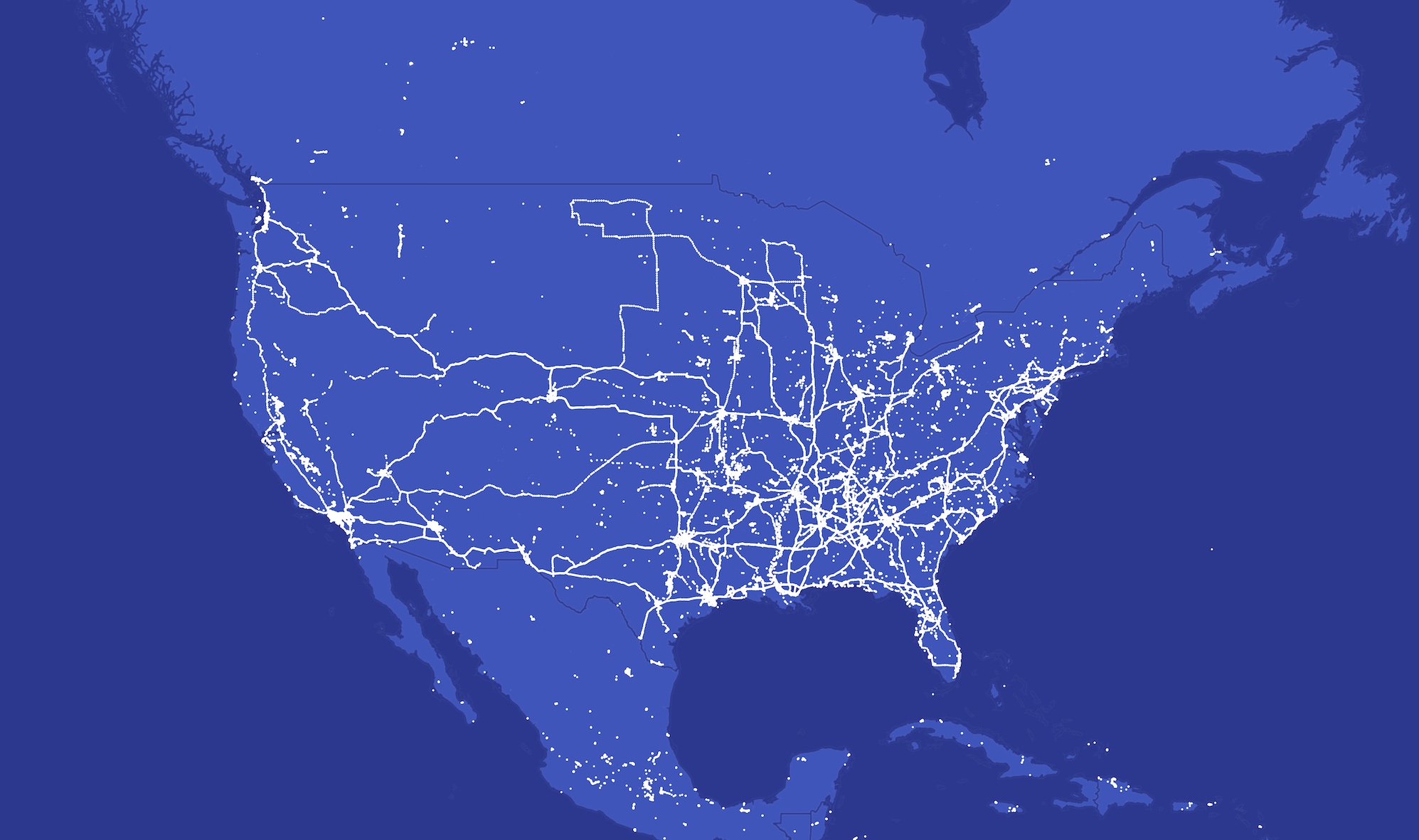
Picture Credit: TechCrunch
Spyhide’s database additionally contained data on 750,000 customers who signed as much as Spyhide with the intention of planting the spy ware app on a sufferer’s gadget.
Though the excessive variety of customers suggests an unhealthy urge for food for utilizing surveillance apps, most customers who signed up didn’t go on to compromise a telephone or pay for the spy ware, the data present.
That mentioned, whereas a lot of the compromised Android gadgets had been managed by a single person, our evaluation confirmed that greater than 4,000 customers had been in command of a couple of compromised gadget. A smaller variety of person accounts had been in command of dozens of compromised gadgets.
The information additionally included 3.29 million textual content messages containing extremely private info, resembling two-factor codes and password reset hyperlinks; greater than 1.2 million name logs containing the telephone numbers of the receiver and the size of the decision, plus about 312,000 name recording recordsdata; greater than 925,000 contact lists containing names and telephone numbers; and data for 382,000 photographs and pictures. The information additionally had particulars on shut to six,000 ambient recordings stealthily recorded from the microphone from the sufferer’s telephone.
Made in Iran, hosted in Germany
On its web site, Spyhide makes no reference to who runs the operation or the place it was developed. Given the authorized and reputational dangers related to promoting spy ware and facilitating the surveillance of others, it’s not unusual for spy ware directors to attempt to preserve their identities hidden.
However whereas Spyhide tried to hide the administrator’s involvement, the supply code contained the identify of two Iranian builders who revenue from the operation. One of many builders, Mostafa M., whose LinkedIn profile says he’s at the moment positioned in Dubai, beforehand lived in the identical northeastern Iranian metropolis as the opposite Spyhide developer, Mohammad A., in response to registration data related to Spyhide’s domains.
The builders didn’t reply to a number of emails requesting remark.
Stalkerware apps like Spyhide, which explicitly promote and encourage secret spousal surveillance, are banned from Google’s app retailer. As a substitute, customers should obtain the spy ware app from Spyhide’s web site.
TechCrunch put in the spy ware app on a digital gadget and used a community visitors evaluation device to know what knowledge was flowing out and in of the gadget. This digital gadget meant we might run the app in a protecting sandbox with out giving it any actual knowledge, together with our location. The visitors evaluation confirmed that the app was sending our digital gadget’s knowledge to a server hosted by German internet hosting large Hetzner.
When reached for remark, Hetzner spokesperson Christian Fitz instructed TechCrunch that the net host doesn’t permit the internet hosting of spy ware.
What you are able to do
Android spy ware apps are sometimes disguised as a normal-looking Android app or course of, so discovering these apps will be difficult. Spyhide masquerades as a Google-themed app referred to as “Google Settings” that includes a cog icon, or a ringtone app referred to as “T.Ringtone” with a musical observe icon. Each apps request permission to entry a tool’s knowledge, and instantly start sending personal knowledge to its servers.
You’ll be able to verify your put in apps via the apps menu within the Settings, even when the app is hidden on the house display screen.
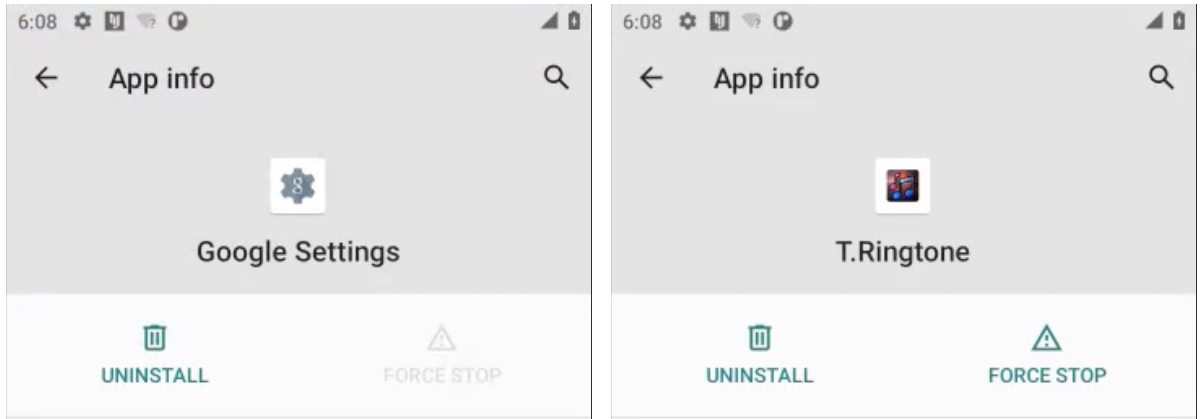
Picture Credit: TechCrunch
We now have a basic information that may aid you take away Android spy ware, if it’s secure to take action. Do not forget that switching off spy ware will probably alert the one who planted it.
Switching on Google Play Defend is a useful safeguards that protects towards malicious Android apps, like spy ware. You’ll be able to allow it from the settings menu in Google Play.
For those who or somebody wants assist, the Nationwide Home Violence Hotline (1-800-799-7233) gives 24/7 free, confidential help to victims of home abuse and violence. If you’re in an emergency state of affairs, name 911. The Coalition Towards Stalkerware additionally has assets in the event you assume your telephone has been compromised by spy ware.