
In some ways, you’ll be able to deal with Microsoft Energy BI as the subsequent technology of Excel. And like Excel, it’s not simply helpful for enterprise analysts and information engineers; IT professionals can make the most of it for understanding massive quantities of knowledge. If the safety instruments you utilize don’t have the proper dashboards and experiences that can assist you see at a look what’s happening along with your methods, you’ll be able to construct them your self in Energy BI — and also you don’t should be an knowledgeable in analytics to create one thing helpful.
For instance, you should utilize Microsoft Energy BI to convey collectively information from the numerous safety instruments most organizations use, so you’ll be able to see what’s taking place throughout all of the totally different methods attackers can be probing — e-mail, identification, endpoints, functions and extra — and spot the totally different levels of an assault.
SEE: Obtain our Microsoft 365 cheat sheet.
Customized safety dashboards
The benefit of Energy BI is how simple it’s to create precisely the proper experiences and visualizations for what’s vital to you, together with AI-powered analytics that discover and spotlight anomalies and outliers within the information. With a unending to-do listing, safety groups are at all times busy and at all times on the lookout for methods to prioritize a very powerful problem they need to be engaged on.
“With little or no coaching, we now have seen people creating detailed and interactive experiences that actually assist with compliance, audit and safety reporting,” Amir Netz, technical fellow and chief know-how officer for Microsoft Cloth, instructed TechRepublic.
You possibly can make cellular variations of your experiences, in order that they’re simple to test if there’s an incident outdoors of hours that it’s essential to assess shortly.
Make a Home windows safety replace dashboard
There are Energy BI content material packs for numerous safety instruments, and several other of Microsoft’s safety instruments have APIs, so you’ll be able to convey that data into Energy BI to visualise. Microsoft Defender for Endpoint has APIs to entry menace and vulnerability information for software program stock, software program vulnerabilities and gadgets which have been detected as being misconfigured — which incorporates lacking Home windows safety updates (Determine A).
Determine A
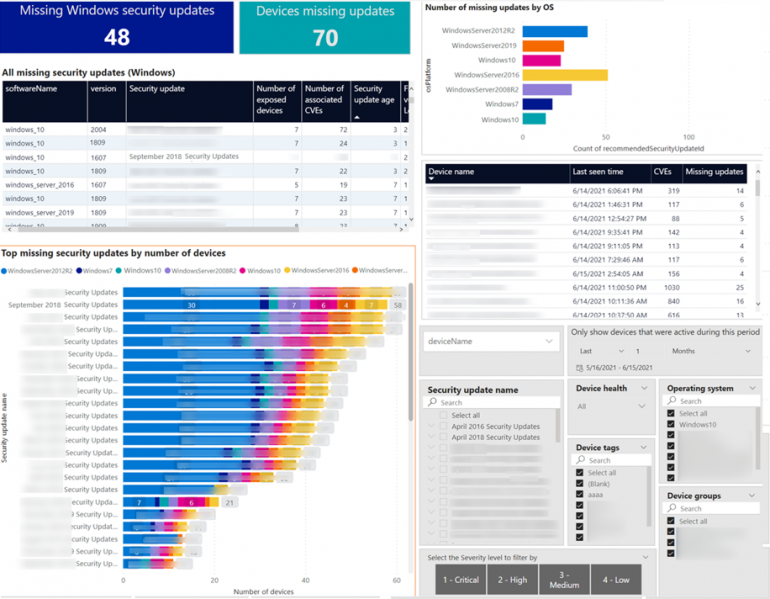
That manner you’ll be able to keep watch over what number of CVEs your group is uncovered to, see how a lot new software program is being put in throughout your group, get a precedence listing of uncovered gadgets or have a look at what OS model susceptible gadgets are working — no matter metrics and points it’s essential to have at your fingertips.
SEE: Make the most of TechRepublic Premium’s Microsoft Energy BI developer hiring equipment.
Select what to see in your dashboard
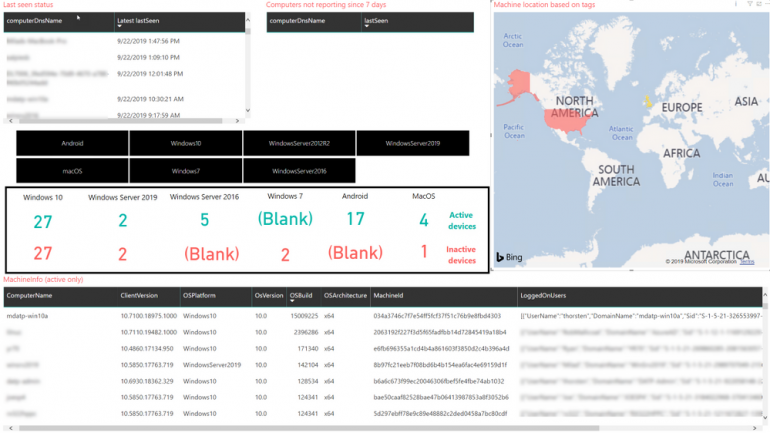
Netz suggests utilizing the Treemap visible to shortly see the comparative numbers of gadgets and points or perhaps a easy bar chart that ranks numerous key measures.
“They present you relative magnitude of influence from a look,” stated Netz. “The Bing map visible will also be very efficient in exhibiting geo distribution of sure actions.”
You possibly can add slicers to filter shortly to what you’re interested by, similar to by working system, and the visuals will replace to point out simply that information (Determine B).
Determine B
Different methods you’ll be able to customise your Energy BI dashboard embrace:
- You may want an in depth report with plenty of visuals or simply some key figures you’ll be able to test shortly in your telephone.
- The Microsoft Defender group runs a repository of helpful Energy BI Defender report templates that features firewall, community, assault floor and menace administration layouts.
- If in case you have a big numbers of gadgets, take the time to scope your queries to optimize them, so your Energy BI experiences don’t decelerate as a result of they’re pulling extra information than you really need.
- You possibly can pull a full snapshot or solely the modifications because you final pulled the info, relying on whether or not you need to look again at safety information over time to see patterns and see if safety insurance policies you’ve launched are making a distinction or whether or not you’re on the lookout for the identical type of real-time overview that Energy BI may give you for IoT gadgets.
- You can too connect with the Superior Looking APIs from Microsoft Defender 365 within the Microsoft Graph safety API in a question in Energy BI Desktop.
“Some clients are content material with being in a extra reactive place and look at every day/weekly snapshots, whereas others demand extra real-time monitoring,” Netz stated. Microsoft Energy BI permits you to pull collectively both type of report shortly whenever you want it.
Monitor Energy BI with Energy BI
As a result of Microsoft Energy BI can connect with nearly any information supply in your group, you in all probability need to maintain monitor of who’s accessing information and visualizations and ensure it’s solely the individuals you count on to have entry to what could be vital or confidential enterprise data.
The role-based entry constructed into Microsoft Energy BI will guarantee solely the proper workers see data, as will Microsoft Purview Info Safety, so long as you’ve arrange discovery, classification and sensitivity labels.
However, the Cloth administrator position lets admins maintain monitor of who’s taking a look at dashboards, experiences and datasets while not having to be a world administrator. Monitoring person entry permissions on Energy BI workspace and artifacts means the IT division can really feel certain customers observe auditing and safety necessities, Netz stated.
You are able to do the identical for any vital enterprise belongings, due to Energy BI’s integration with Microsoft Defender for Cloud Apps. With Defender for Cloud Apps, you’ll be able to create conditional entry insurance policies that may be utilized in actual time by Microsoft Entra ID (the brand new title for Azure Energetic Listing). Within the Defender for Cloud Apps portal you’ll be able to set insurance policies and get alerts that can allow you to:
- Cease customers from copying and pasting information from a delicate report.
- Search for people who find themselves downgrading sensitivity ranges on a number of paperwork.
- Search for individuals sharing plenty of experiences or sharing a delicate report with a brand new exterior e-mail tackle they haven’t despatched experiences to earlier than.
“Microsoft Defender for Cloud Apps allows organizations to observe and management, in actual time, dangerous Energy BI periods, similar to person entry from unmanaged gadgets,” stated Netz. “Safety directors can outline insurance policies to regulate person actions, similar to downloading experiences with delicate data. With Energy BI’s integration, you’ll be able to set monitoring coverage and anomaly detection and increase Energy BI person exercise with the Exercise log.”
That may assist you to discover patterns like a malicious insider who makes use of Energy BI information to search out the vital enterprise methods to exfiltrate information from with one other software.
“We offer uncooked audit log information that goes again 30 days by way of API and by way of the Microsoft 365 compliance middle,” Netz stated.
That manner, if you happen to see one thing suspicious in considered one of your customized safety dashboards, you’ll be able to return and see what else was happening on the similar time.

