Microsoft introduced a brand new Defender for IoT characteristic that can enable analyzing the firmware of embedded Linux units like routers for safety vulnerabilities and customary weaknesses.
Dubbed Firmware Evaluation and now obtainable in Public Preview, the brand new functionality can detect a variety of weaknesses, from hardcoded consumer accounts and outdated or susceptible open-source packages to using a producer’s non-public cryptographic signing key.
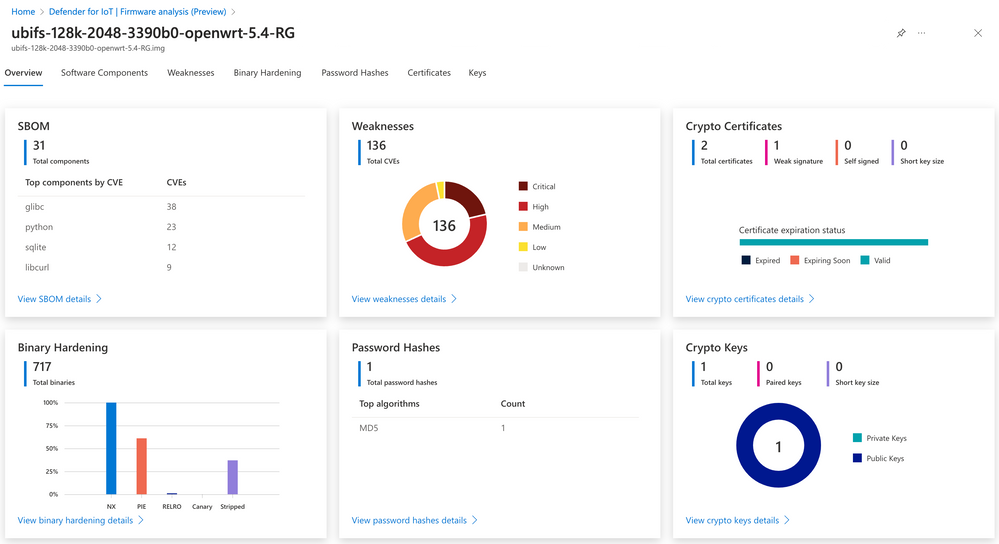
“Firmware evaluation takes a binary firmware picture that runs on an IoT gadget and conducts an automatic evaluation to determine potential safety vulnerabilities and weaknesses,” Microsoft’s Derick Naef says.
“This evaluation supplies insights into the software program stock, weaknesses, and certificates of IoT units with out requiring an endpoint agent to be deployed.”
The next options are at the moment obtainable to investigate IoT units’ firmware safety:
- Software program Invoice of Supplies (SBOM): Offers a listing of open-source packages used to construct the firmware, indicating the package deal model and the corresponding licensing agreements.
- CVE Evaluation: Affords insights into firmware parts with publicly recognized safety vulnerabilities and exposures.
- Binary Hardening Evaluation: Identifies binaries compiled with out safety flags, resembling buffer overflow safety, position-independent executables, and different widespread hardening methods.
- SSL Certificates Evaluation: Uncovers expired and revoked TLS/SSL certificates inside the firmware.
- Public and Personal Key Evaluation: Verifies the need and authenticity of private and non-private cryptographic keys discovered within the firmware
- Password Hash Extraction: Ensures that consumer account password hashes use safe cryptographic algorithms
To make use of it, customers need to go to the “Firmware evaluation (preview)” blade in Defender for IoT and add the Linux-based firmware picture from their gadget.
The system will then unpack the picture to detect the embedded file system and analyze the loaded firmware for hidden menace vectors.
It is vital to notice that solely compiled and unencrypted Linux-based firmware pictures obtained out of your gadget’s vendor might be analyzed utilizing the Defender for IoT Firmware Evaluation characteristic. Additionally, the picture should not exceed 1 GB in measurement.
“The Defender for IoT Firmware Evaluation characteristic is routinely obtainable should you at the moment entry Defender for IoT utilizing the Safety Admin, Contributor, or Proprietor function,” Microsoft says.
“In case you solely have the SecurityReader function or wish to use Firmware Evaluation as a standalone characteristic, then your Admin should give the FirmwareAnalysisAdmin function.”