The U.S. Cybersecurity and Infrastructure Safety Company (CISA) on Friday disclosed particulars of a “novel persistent backdoor” known as SUBMARINE deployed by risk actors in reference to the hack on Barracuda E-mail Safety Gateway (ESG) home equipment.
“SUBMARINE includes a number of artifacts — together with a SQL set off, shell scripts, and a loaded library for a Linux daemon — that collectively allow execution with root privileges, persistence, command and management, and cleanup,” the company stated.
The findings come from an evaluation of malware samples obtained from an unnamed group that had been compromised by risk actors exploiting a important flaw in ESG units, CVE-2023-2868 (CVSS rating: 9.8), which permits for distant command injection.
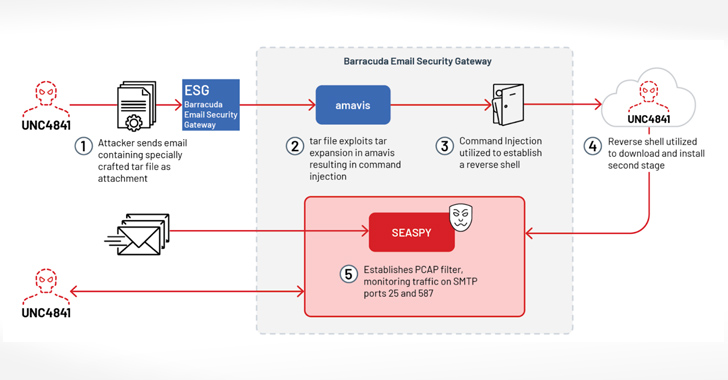
Proof gathered thus far reveals that the attackers behind the exercise, a suspected China nexus-actor tracked by Mandiant as UNC4841, leveraged the flaw as a zero-day in October 2022 to realize preliminary entry to sufferer environments and implanted backdoors to determine and preserve persistence.
To that finish, the an infection chain concerned sending phishing emails with booby-trapped TAR file attachments to set off exploitation, resulting in the deployment of a reverse shell payload to determine communication with the risk actor’s command-and-control (C2) server, from the place a passive backdoor often called SEASPY is downloaded for executing arbitrary instructions on the gadget.
SUBMARINE, additionally codenamed DEPTHCHARGE by the Google-owned risk intelligence agency, is the most recent malware household to be found in reference to the operation. Executed with root privileges, it resides in a Structured Question Language (SQL) database on the ESG equipment.
Defend In opposition to Insider Threats: Grasp SaaS Safety Posture Administration
Apprehensive about insider threats? We have you lined! Be part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
It is believed to have been “deployed in response to remediation efforts,” echoing Mandiant’s characterization of the adversary as an aggressive actor able to shortly altering their malware and using further persistence mechanisms in an try to take care of their entry.
The company additional stated it “analyzed artifacts associated to SUBMARINE that contained the contents of the compromised SQL database,” and that it “poses a extreme risk for lateral motion.”