
Fortinet has issued an alert warning that the Gafgyt botnet malware is actively attempting to use a vulnerability within the end-of-life Zyxel P660HN-T1A router in hundreds of every day assaults.
The malware targets CVE-2017-18368, a important severity (CVSS v3: 9.8) unauthenticated command injection vulnerability within the system’s Distant System Log forwarding operate, which was patched by Zyxel in 2017.
Zyxel beforehand highlighted the menace from the then-new Gafgyt variant in 2019, urging customers nonetheless utilizing an outdated firmware model to improve to the most recent launch to guard their units from takeover.
Nonetheless, Fortinet continues to see a median of seven,100 assaults per day for the reason that starting of July 2023, with the quantity of assaults persevering with at the moment.
“[As of] Aug 7, 2023, FortiGuard Labs proceed to see assault makes an attempt focusing on the 2017 vulnerability and has blocked assault makes an attempt of over hundreds of distinctive IPS units during the last month,” reads a brand new Fortinet outbreak alert launched at the moment.
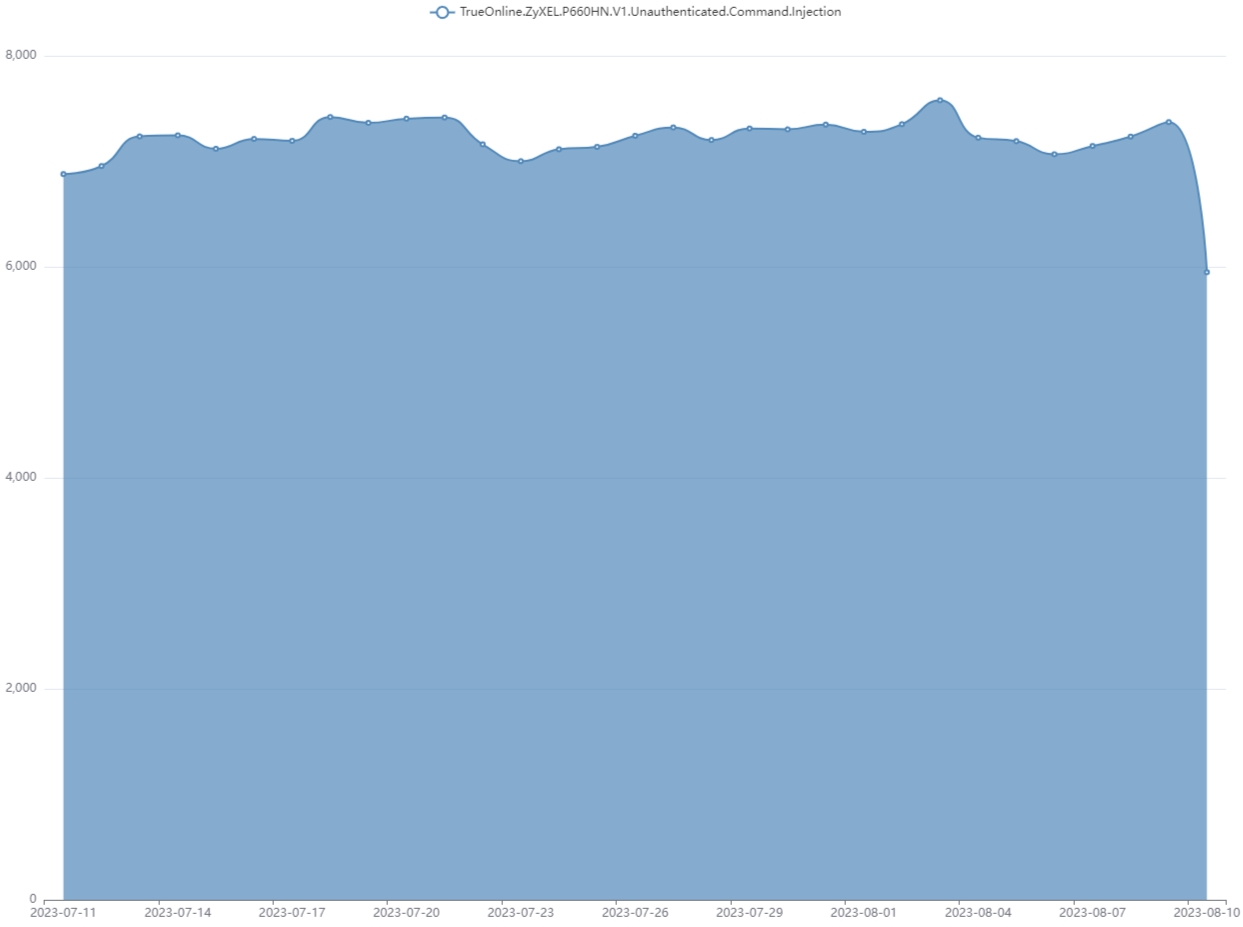
Supply: Fortinet
It’s unclear what portion of the noticed assault makes an attempt resulted in profitable infections. Nonetheless, the exercise has remained at a gradual quantity since July.
CISA additionally warned this week concerning the lively exploitation of CVE-2017-18368 within the wild, including the flaw to its catalog of recognized exploited vulnerabilities.
The cybersecurity company now requires federal businesses to patch the Zyxel vulnerability by August twenty eighth, 2023.
In response to the exploitation outbreak, Zyxel up to date its safety advisory, reminding prospects that CVE-2017-18363 solely impacts units working firmware variations 7.3.15.0 v001/3.40(ULM.0)b31 or older.
P660HN-T1A routers working the most recent firmware model made obtainable in 2017 to remediate the flaw, model 3.40(BYF.11), aren’t impacted by these assaults.
Nonetheless, the seller highlights that the system has reached end-of-life and is now not supported, so switching to a more recent mannequin could be clever.
“Please observe that the P660HN-T1A reached end-of-life a number of years in the past; due to this fact, we strongly suggest that customers exchange it with a newer-generation product for optimum safety,” warns Zyxel.
Frequent indicators of botnet infections on routers embody unstable connectivity, system overheating, sudden configuration modifications, unresponsiveness, atypical community site visitors, opening up of recent ports, and surprising reboots.
For those who suspect a compromise from botnet malware, carry out a manufacturing unit reset, replace your system firmware to the most recent model, and alter the default admin person credentials.
Additionally, it suggested that you just disable the distant administration panel and solely handle the units out of your inside community.
