In 2016, hackers utilizing a community of compromised internet-connected gadgets — susceptible safety cameras and routers — knocked a few of the then largest web sites on the web offline for a number of hours. Twitter, Reddit, GitHub and Spotify all went down intermittently that day, victims of what was on the time one of many largest distributed denial-of-service assaults in historical past.
DDoS is a type of cyberattack the place dangerous actors flood web sites with malicious visitors with the aim of taking them offline. DDoS assaults had existed for years earlier than 2016, however the truth that this one incident took down so many main providers drew the eye of people that didn’t know a lot about cybersecurity.
Since then, no DDoS assault has ever been so newsworthy, however the issue hasn’t gotten away. On December 15, 2022, proper earlier than Christmas — traditionally a well-liked time to launch DDoS assaults — the FBI introduced that it had taken down dozens of internet sites that promote what are referred to as booter or stressers, basically DDoS-for-hire providers. These are comparatively low-cost providers that enable folks with low or no hacking expertise to hold out DDoS assaults.
On the identical day, the feds additionally introduced that that they had arrested seven individuals who allegedly ran these providers. Then, the FBI focused these providers and took down extra booter websites in Could.
All these latest operations — in addition to the investigation into Mirai, the malware used within the notorious 2016 assaults — had been led by the FBI workplace in Anchorage.
On Wednesday, Elliott Peterson, one of many FBI brokers who led these investigations, spoke on the Black Hat cybersecurity convention in Las Vegas. Peterson, together with Cameron Schroeder, a prosecutor who makes a speciality of cybercrimes, talked concerning the work behind the investigations that led to the Christmas and Could takedowns.
Schroeder additionally revealed that it was Peterson himself who created the splash pages that changed the seized web sites.
Peterson, who has centered on DDoS assaults for a decade, sat down with TechCrunch on Thursday to speak about his work going after the folks behind these DDoS providers, and figuring out which providers to take down. He defined what objectives regulation enforcement has with these investigations, how DDoS assaults have modified over time, who’re the folks behind them,
The next transcript has been edited for brevity and readability.
TechCrunch: How lengthy have you ever been investigating DDoS assaults? And the way have DDoS assaults modified over time?
So most likely 9 or 10 years. And it’s modified fairly a bit. Once I began trying on the downside, we had been actually considering when it comes to the highest booter or stresser providers, which is the place a variety of the market and a variety of the client base was. After which, in the course of working investigations into booter and stressers, we bought drawn into the botnet world. And so it’s actually been sort of this yo-yo backwards and forwards between what we expect are probably the most threatening parts of the DDoS panorama, after which we’ll attempt to cope with that. After which the criminals react to what we do and alter, and we’ve got to relearn, and it’s simply been this sort of fixed course of over about 9 or 10 years.
What’s the largest change that you just’ve seen within the final 10 years?
I feel in a variety of methods simply the increasing of the companions that we’ve got. After we first began, we had been attempting to work with those who understood and centered on DDoS, and that was a very small subset of the safety group. I really feel like over time, we’ve had much more companions throughout the non-public sector, inside academia, and inside regulation enforcement, we’ve had lots of people actually all for the issue.
And possibly this can be a little little bit of a media bias, however I really feel like typically there’s a sense that DDoS is sort of a boring downside, or an issue that’s been solved?
Oh, no, no, you’re not improper in any respect. We bump up in opposition to it on a regular basis. And there’s methods through which it’s sort of true. And there’s methods through which it’s emphatically not true. However in case you take a look at the transitory, non permanent nature of some DDoS assaults, it’s an issue whereas it’s occurring, and possibly it’s an issue when the assault stops.
“Typically, in case you’re large enough to be within the information, you begin to be on our radar.” Elliott Peterson, FBI
If any person is intending solely to quickly disrupt an internet site or individual, it’s slightly little bit of an issue or a variety of an issue throughout it, after which afterwards, they could overlook or transfer on. Now, DDoS at a sure scale or quantity is a completely completely different downside. And so, a variety of the those who say DDoS isn’t an issue are crying for the hills when their web sites are down frequently, or there’s a risk that’s so giant, that there’s not a mitigation pathway.
I feel what’s sort of distinctive of what FBI Anchorage has been doing is we’ve been actually centered on that crime-type all through that interval. And it’s allowed us to reply much more rapidly when it does turn into a very sustained downside. However by quantity, it is likely one of the largest cybercrime issues when it comes to the frequency of assaults, for instance.
How giant is it when it comes to monetary losses?
That’s tougher to find out. You’ve gotten instances the place there’s extortion or a sufferer would possibly pay a sure amount of cash. However DDoS has a variety of oblique prices. If I’m getting DDoS’ed frequently, a variety of victims pays their manner outdoors of the ability of the attacker, however that’s incrementally growing their bandwidth prices. That’s actually laborious for us to seize, I feel. However in case you take a look at simply the dimensions of a few of the corporations focusing on DDoS mitigation, for instance, you may have very giant corporations that that’s their enterprise mannequin. So, I don’t wish to put a price ticket on it.
Yeah, Cloudflare is a huge firm…
As is Akamai, as is Fastly. There’s a variety of that. And each ISP could have plans that sure clients get pushed to as a result of it’s possibly the way in which to remain outdoors of sure DDoS providers. We predict that it’s one of many issues the place it will increase the expense for everyone on the web, nevertheless it’s laborious to know precisely how a lot.
And so how do you select who to go after? It’s an enormous downside, how do you decide your battles?
One of many issues that I feel it’s probably the most thrilling is that we’ve got that potential to decide on, we will take a look at it, and give it some thought. Typically, we’re prioritizing prime providers. So, who’s conducting probably the most assaults? Who’s been across the longest? Who has probably the most clients? Who’s able to conducting the most important assaults for booter stresser providers?
After we make questions on how are we specializing in — for instance — botnets? It’s an identical methodology. However typically, in case you’re large enough to be within the information, you begin to be on our radar. After which we would pause and concentrate on one thing like that.
Like Mirai from a number of years in the past.
Yeah, and that was an FBI Anchorage case. It’s an awesome instance of everybody says, ‘DDoS doesn’t matter.’ And then you definately lastly have a botnet like Mirai and for some time DDoS actually issues. That was really a case we labored from begin to end in Anchorage, and mainly used every thing we’d discovered about booter stresser providers and pivoted and handled Mirai, after which got here again to work on booter stresser providers.
Mirai was big, I bear in mind there was that day the web sort of went down for a number of or a few hours, which is loopy to consider now. What’s the aim? Clearly, catching criminals, however is it deterrence? Is it having access to low degree criminals as a way to then go after greater providers? What’s the considering?
I feel, huge image, our considering is what can we study in attempting to scale back the specter of these providers that we will apply to different crime varieties? What can we study in combating these DDoS providers, each to make the web safer, but additionally possibly to use to ransomware, distant entry trojans or different sorts of web instruments? That’s by and enormous what Cameron [Schroeder] and I had been attempting to debate. However we expect it’s an issue that folks solely take note of slightly little bit of the time, and we expect we’re having a variety of success by specializing in it on a regular basis.
How efficient has been the deterrence? Sooner or later Schroeder stated that after one huge operation that there was a 20% lower in DDoS exercise. Are you able to speak extra about that?
We’re ascribing worth to numbers. However as a result of we will measure DDoS and since we will precisely take a look at the place DDoS is and observe trajectories, we’ve got an estimate that most likely our final operation noticed a reasonably sustained internet 20% discount on every day assault quantity. Different operations we’ve seen much less or greater than that.
What’s neat this time is at the very least it appears to be like prefer it’s sustained. Possibly some portion of the client base possibly moved on. And that’s actually our aim: a mixture of training those who that is prison, holding folks accountable and attempting to not be ready the place younger males and a few younger girls develop up accustomed to getting access to these instruments. As a result of once you’ve had entry to the sort of firepower which you could get for $20 a month — that, by the way in which, in case you needed that sort of bandwidth, at house you’d be paying $250-$350 a month or extra — what we see is folks turn into habituated having that, so they only proceed to make use of these providers. We’d actually like to clarify to those who it’s prison, they shouldn’t do it, so we will concentrate on different crime issues.
You stated that for the final there was a 20% lower. That’s the March or the Christmas operation?
That was Christmas and March. There’s an entire sequence of operations that got here out after Christmas. We noticed a few 20% total discount within the assault volumes. However we’re hoping to have significantly better knowledge quickly, as a few of these universities examine that.
Goes after the booters additionally partially attempting to dismantle the botnets behind them?
To me, they’re functionally very various things with the exception that we’ve got had booter providers which have tied themselves to botnets or added botnet functionality. But when we take into account botnets sufferer gadgets, and usually, these are conducting what are sometimes referred to as layer 7, or TCP-based assaults, and they are often very highly effective as a result of you can also make the contaminated sufferer that includes the botnet, basically work together with the meant sufferer. Whereas more often than not with booters, they’re conducting these intelligent assaults the place they’re magnifying their knowledge. However on the finish of the day, it’s all unrequested UDP. It’s simply sheer bandwidth, it may be filtered, it may be dropped.
The botnets, typically, that’s much more difficult. We take a look at them as completely different threats. However we perceive that they type of exist throughout the identical prison financial system. The distinction is that botnets are usually much more costly. You’ve gotten those who have bigger prison financial objectives, they’re usually utilizing botnets, or you may have different instances the place the booting providers are usually lots cheaper and have a distinct clientele.
I suppose it’s truthful to say that possibly the botnets usually are not for teenagers that wish to disrupt gaming?
They are often, however typically a botnet is one thing that you’re utilizing to disrupt a whole gaming service, let’s say, as a result of the variety of bots after which the height out there capability of these bots isn’t all the time larger than what you’d see with a booter however usually it’s. The use case turns into slightly completely different. The place we regularly see botnets being profitable is they could take down your entire gaming service and never simply kick any person out of a sport.
Now that we’re speaking about it, I bear in mind a number of years in the past when the entire PlayStation Community went down, it was Christmas day or the day after Christmas.
“Our hope is to not arrest everyone, our hope is to arrest probably the most problematic folks and persuade the remainder of the those who this isn’t a great path.” Elliott Peterson, FBI
That may have been Star Patrol, and there have been a number of different names like Lizard Squad. That was proper earlier than Mirai took off.
A extremely humorous — and lengthy story that we don’t have time for — is that a part of Mirai’s growth was pushed by competitors, as a result of the group that did these Christmas assaults had an [Internet of Things] botnet that was very efficient.
They each had been conscious of the identical vulnerability. And whoever managed that vulnerability, managed tons of of 1000’s gadgets. They had been really combating with one another to see who would be capable of management all of these gadgets. That’s really what drove a variety of the development that made Mirai so efficient.
Typically you time your operations round instances when DDoS assaults are extra prevalent, like Christmas, for instance in 2022. What’s the motivation behind doing this?
Precisely what you described. You’ve had this historic tendency the place Christmas is the busiest DDoS interval for lots of causes. We’ve began attempting to time operations to coincide; the place within the vacuum created by our takedowns by December, DDoS is lots tougher to do, as a result of the operators that weren’t arrested are going again to need to reset up their stuff. Everybody’s typically slightly alarmed at what the subsequent shoe goes to drop. That’s why we’ve timed it. In some methods, we’re setting ourselves up the place we’re competing with probably the most intense DDoS interval. We might decide a distinct time and possibly see extra of a discount, however that’s why. Banks and different industries can get actually nervous round Christmas time. This modified that panorama slightly bit.
Does it additionally ship a message to the criminals themselves?
Ideally, what we’re attempting to do is ship this broad message of deterrence. Our hope is to not arrest everyone, our hope is to arrest probably the most problematic folks and persuade the remainder of the those who this isn’t a great path.
And talking of the cyber criminals, you stated yesterday that there are some improper assumptions about them, each when it comes to who makes use of these providers and who runs them?
Yeah, DDoS to me has a really distinct cybercriminal profile. Typically, you’re going to have any person based mostly in North America or Western Europe. They often will talk in gaming, they’re normally younger grownup males, they are often engaged in different cybercrime varieties, however usually DDoS could also be one of the fashionable varieties. They’re normally adjoining in a roundabout way to gaming, they usually’re usually making $30,000-$50,000 to $100,000 a yr, relying on how huge their providers are. They usually begin possibly between 16 and 19 [years of age], and by the point they’re prime service — and we catch as much as them — they’re someplace between 19 and 25 [years old], normally, when it comes to a profile.
That’s not dangerous cash for that sort of age.
And that’s the issue, proper? That’s what we’ve been attempting to determine is the place you may have this financial driver for the crime sort, it makes it tougher to maneuver folks away from the service.
And the way subtle are they? Since you confirmed that they make some fairly dangerous OPSEC errors.
I’d say that due to the crime sort, and due to who their clients are, I’d say that they’re typically not as subtle as you would possibly take into account a few of the extra conventional cyber actors. However that’s not even completely truthful, as a result of criminals who’re providing providers are usually extra subtle than the criminals which are consuming the providers. If I take a look at any person working a DDoS service, they’re normally way more technically subtle than their clients.
However they might not be far behind any person doing a distant entry trojan or any person doing one thing else, as a result of by and enormous, the instruments they’re utilizing have been positioned on-line. So, slightly little bit of internet growth, [and] a variety of customer support expertise is commonly required for them to achieve success. There’s a variety of backwards and forwards with clients that these guys need to be keen to do in the event that they wish to earn cash.

FBI discussing DDoS-for-hire websites on the Black Hat cybersecurity convention in Las Vegas. Picture Credit score: FBI (provided)
You talked about yesterday that some folks don’t even use VPNs. Are you able to speak slightly bit extra about that?
Tons of individuals don’t use VPNs. It’s actually a false impression, I feel, within the cybercrime area that each one of those actors are utilizing VPNs. And even after they’re utilizing VPNs, a variety of actors nonetheless don’t thankfully perceive the ways in which we regularly need to push previous VPNs.
Within the booter area, it’s most likely extra unusual than frequent for me to see VPN utilization. However that’s not unfaithful for different crime varieties the place folks don’t assume they are often caught. As a result of the actor is utilizing this prison service and he’s been advised there’s no logs saved by the prison actor, he doesn’t essentially really feel the identical must have a VPN engaged as he would possibly attempt to money out credentials from a financial institution or one thing.
I feel that a few of it’s, they exist in a spot the place they assume that they have already got some safety.
And so when you establish who to go after, what’s the proof that you just’re searching for, and the way do you acquire it?
It is dependent upon if we’re searching for clients or if we’re searching for operators. For operators, as we specified by the presentation, what we’re attempting to ascertain is does their service work as a result of we wish to focus our time on people who find themselves really actually facilitating DDoS typically? And if their service works, then we’re going to ask questions on who set that service off, and as soon as we begin to set up that, we’ll usually ask questions on their communication accounts. What are they utilizing, and the way are they speaking? And more often than not, that’ll take us over a interval of months to know the place we expect any person’s positioned, after which we go and ask a decide for permission to mainly go and take proof from them, and interview them. That begins this course of the place I’d take all of that accrued proof, and we give that to a prosecutor, after which they make choices about how we go ahead.
In order that’s on the folks’s aspect. At what level do you determine to grab and shut down the providers? And why do you determine to do it then?
What’s enjoyable about this case is as a result of we’re attempting to take action a lot concurrently, we’ll batch issues. So like my investigation, I may be batching questions on a bunch of actors, however I clearly can’t normally go to everyone on the identical day. We’d unfold all of our searches out over a interval of a month or two months. However we’ll normally decide a date, not simply with us however with our companions.
Typically you received’t hit that date. That’s what’s actually sophisticated on this area. To have so many issues occur concurrently, like we’ve been in a position to do, we’ve got to decide to a date usually months out, and everybody could have completely different roles, and it provides a variety of stress. The one factor we normally have performed effectively prematurely of that date is we’re prepared, we all know who we wish to cost. However the mechanisms of taking the service stuff away is actually sophisticated. And any person would possibly change internet hosting every week earlier than we do it, or one thing else might change that we’re scrambling.
What’s the function of the non-public sector in combating DDoS assaults?
In a variety of methods, they’re the entrance traces. They’re the internet hosting corporations, or the DDoS protection corporations which are actually centered on this. They do an unimaginable job of constructing positive we perceive the science and expertise we have to sustain with this.
If there’s a brand new assault method, or a brand new service, they’re usually the place we hear about that first. They’re offering us the knowledge we have to make higher choices, and that’s been a lot of the function that we’ve full of them. They’re serving to us form our technique by giving us suggestions when it comes to what they assume will or received’t work. And that isn’t essentially a query about which service to go after, or what we must always say to those actors throughout interviews, however extra like: Ought to we do that at Christmas? Which protocols ought to we prioritize for our testing of those providers? How can we take a look at these providers with out inflicting an excessive amount of hurt?
So it’s actually like a crew sport?
Very a lot, sure.
And what message would you ship to victims of DDoS?
Tell us. We do a variety of consulting in Anchorage for victims of DDoS, particularly giant platforms that get hit.
There’s methods to report it. We’re not essentially doing technical remediation, however we attempt to assist victims perceive is that this a brief time period assault? Is that this a long run assault? Do you perceive the motivations of the attacker? As a result of if you realize what the motivations are of the attacker, and you know the way they’re attacking you, we will additionally assist them perceive how a lot the attacker might be paying to do that. That may be vital as a result of an attacker who’s mad sufficient at a enterprise that they’ve 1000’s of {dollars} to spend, that places them in a completely completely different danger class than an attacker that’s utilizing an inexpensive plan on a booting service.
We’re encouraging victims to achieve out to us. In the event that they’re victims of DDoS assaults, in the event that they’ve misplaced cash. If it’s a variety of assaults, we’d like to know and speak to them.
You stated yesterday that you just’re nonetheless not making the hackers’ lives laborious sufficient. What are doing or going to do in a different way going ahead?
Our hope is to proceed to discover ways to conduct more practical operations, which could imply bigger, extra shifting items, [and] extra companions. Our subsequent part is taking a very laborious take a look at a few of these clients that most likely don’t assume that we’ve got the info we do, and in addition shifting to together with extra of the purchasers and mainly holding them accountable for his or her assaults.
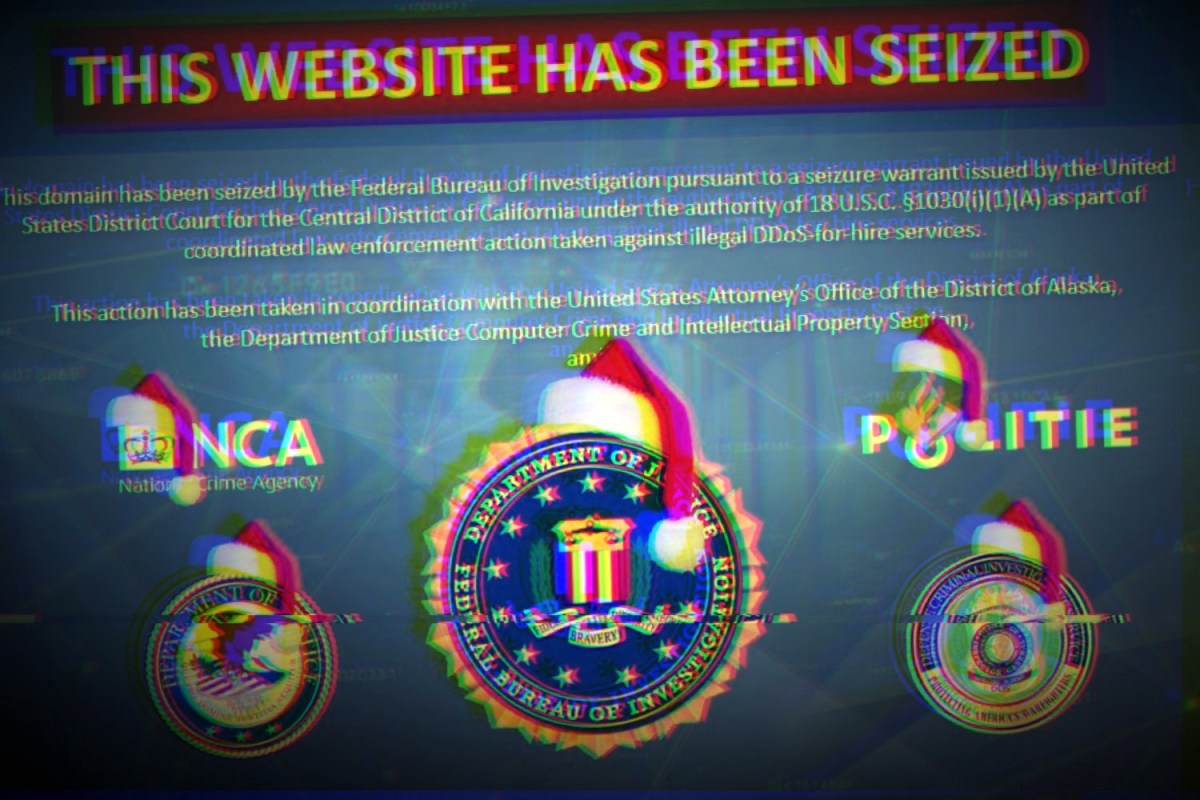
Lastly, are you able to inform me about your expertise making the logos for the seizure notices?
We get suggestions from a few of our companions, particularly worldwide regulation enforcement, who’ve a variety of expertise with these takedowns and these seizures. And they also’re those that say, ‘hey we’re doing these actually easy blue seizure pages.’ And like, ‘no, it must be pink, you’ve bought to speak viscerally to them this concept of cease.’ It appears easy, however how do you get a background everyone agrees on, whose brand goes the place, how giant, and there’s all these humorous issues that you just don’t anticipate to need to cope with, that we get requested to do? As a result of we don’t actually have a graphic assist division to assist us with a variety of that.
Did you set the Christmas hats on the logos?
No, researchers did that. And actually I had misplaced a battle. I attempted to make use of that as our official brand subsequent time, and I used to be advised we couldn’t, as a result of I assumed that may simply be actually a humorous gesture.