In at the moment’s tech-driven panorama, it’s hardly stunning that hackers are setting their sights on these units. What’s much more regarding is the fact: a current examine found that over 1 in 5 Android telephones have already been compromised.
These numbers hit near dwelling, emphasizing the crucial significance of fortifying our digital safety measures to guard our cherished units and private info. On this information, we’ll discover the most effective methods to determine your Android telephone is hacked or not.
What’s Cellphone Hacking?
Cellphone hacking is when somebody will get into your smartphone with out permission. Hackers do that to take your private information, put dangerous stuff in your telephone, or management it from far-off. They could steal your cash information, personal chats, and extra. They will even put dangerous software program, referred to as malware, in your telephone to trigger issues. This can be a large violation of your privateness and may hurt you in some ways.
How Do You Know That Your Cellphone Has Been Hacked?
1. Information Utilization is Greater Than Regular
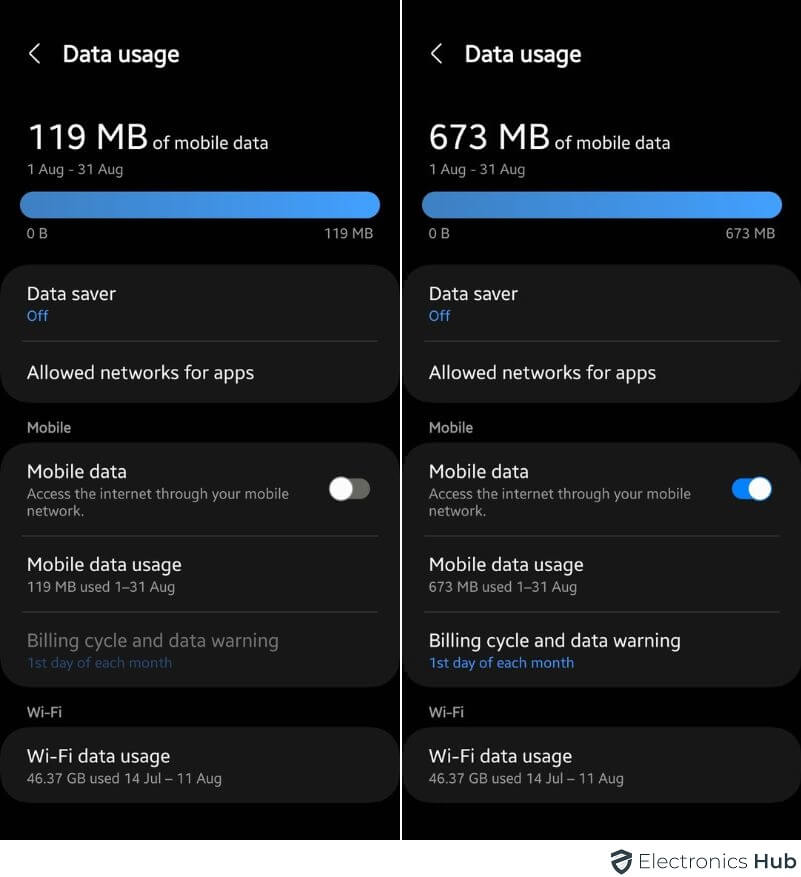 Think about your telephone’s information being taken over by a hacker – they will make it do dangerous issues. They could use your information to ship and obtain dangerous stuff, making your information utilization shoot up.
Think about your telephone’s information being taken over by a hacker – they will make it do dangerous issues. They could use your information to ship and obtain dangerous stuff, making your information utilization shoot up.
Hackers can flip your telephone right into a software for “mining” cryptocurrency. This course of makes use of loads of your telephone’s energy, drawing it out of your information plan. So, in case your telephone is hacked, you may see your information utilization going loopy due to these sneaky actions.
2. Unusual or Inappropriate Pop Ups
 When your telephone begins exhibiting unusual or inappropriate pop-ups, these pop-ups are sometimes instruments that hackers use to idiot you into clicking on dangerous hyperlinks or downloading malicious software program.
When your telephone begins exhibiting unusual or inappropriate pop-ups, these pop-ups are sometimes instruments that hackers use to idiot you into clicking on dangerous hyperlinks or downloading malicious software program.
These pop-ups can take varied varieties:
- Warnings claiming your telephone has malware.
- Provides to repair your telephone for a price.
- Shows of specific or offensive content material.
- Requests for private information like bank card or Social Safety numbers.
In case you encounter such pop-ups, it’s essential to not click on them. As an alternative, take these steps:
- Shut the pop-up.
- Use a trusted antivirus or anti-malware app to scan your telephone.
- Replace your passwords for all on-line accounts.
3. Cellphone is Too Sizzling
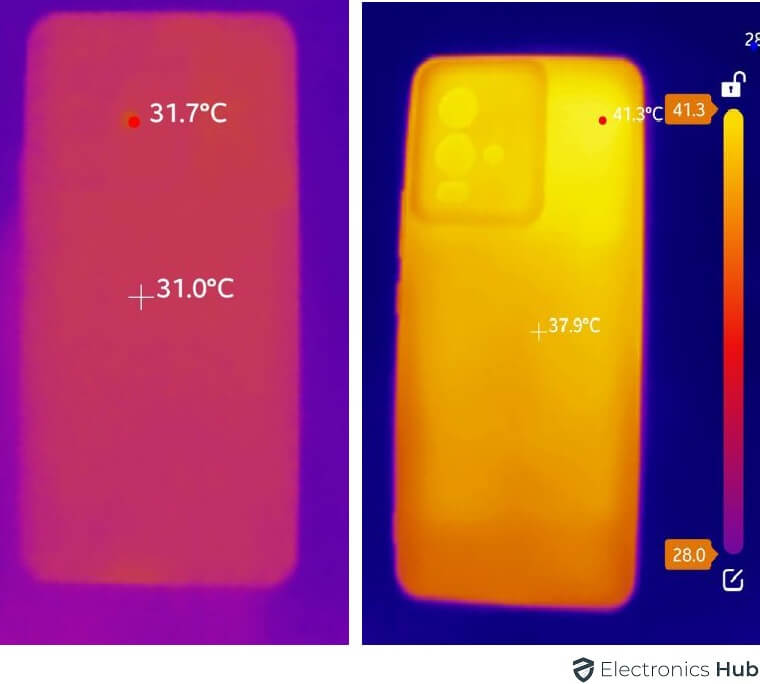 In case your telephone begins feeling unusually heat, even if you’re not utilizing it, it would elevate a priority a couple of doable hack. Hackers typically plant dangerous software program, referred to as malware, in telephones, which may result in overheating. This occurs as a result of the malware secretly works within the background, utilizing up your telephone’s assets.
In case your telephone begins feeling unusually heat, even if you’re not utilizing it, it would elevate a priority a couple of doable hack. Hackers typically plant dangerous software program, referred to as malware, in telephones, which may result in overheating. This occurs as a result of the malware secretly works within the background, utilizing up your telephone’s assets.
When your telephone’s temperature rises past the norm, it’s value contemplating:
- The potential of malware presence.
- Background actions by malicious software program.
- The hacker’s try to use your machine.
To reply:
- Monitor your telephone’s temperature.
- Run a radical scan utilizing respected antivirus or anti-malware instruments.
- If vital, take motion to take away the malware and reinforce your telephone’s safety in opposition to potential breaches.
4. Texts or Calls That Are Not Made By You
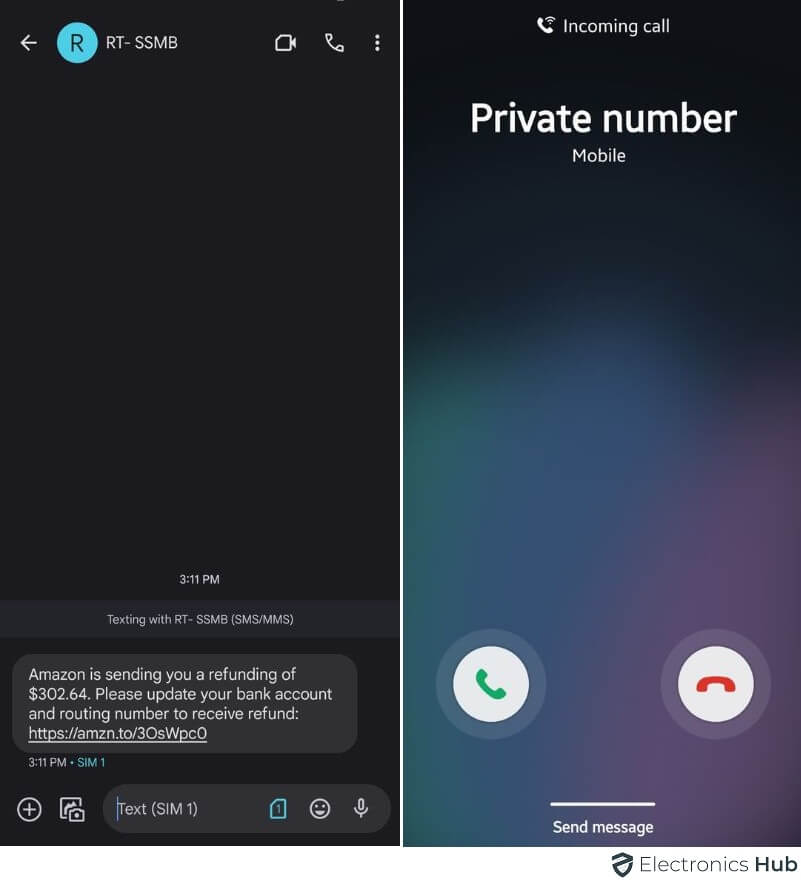 In case you discover texts or calls you don’t keep in mind making, it would sign a hack. Hackers typically misuse telephones for sending spam or unauthorized calls.
In case you discover texts or calls you don’t keep in mind making, it would sign a hack. Hackers typically misuse telephones for sending spam or unauthorized calls.
Indicators of potential hacking linked to calls or texts:
- Unusual numbers exhibiting up in your name log.
- Receiving texts from unfamiliar numbers.
- Noticing odd actions in your on-line accounts, like unauthorized logins or password modifications.
If hacking appears probably, safe your machine by:
- Checking for threats utilizing a trusted antivirus or anti-malware app.
- Altering passwords for all of your on-line accounts.
5. Cellphone is Performing Slowly
 Experiencing a slow-down in your telephone? It’s doable fallen sufferer to hacking. In these cases, cyber attackers slip in undetected, sneaking malicious software program onto your machine. This hidden program quietly will increase your telephone’s energy—its CPU and reminiscence—leading to noticeable slowness. Apps may drag their ft when opening or responding. What’s worse, these hackers is likely to be exploiting your machine as half of a bigger community, inflicting additional lags because it’s used for spam or cyber assaults. To make issues much more regarding, these unauthorized customers is also siphoning off your private information, putting a further load in your telephone’s assets and compounding the slowdown.
Experiencing a slow-down in your telephone? It’s doable fallen sufferer to hacking. In these cases, cyber attackers slip in undetected, sneaking malicious software program onto your machine. This hidden program quietly will increase your telephone’s energy—its CPU and reminiscence—leading to noticeable slowness. Apps may drag their ft when opening or responding. What’s worse, these hackers is likely to be exploiting your machine as half of a bigger community, inflicting additional lags because it’s used for spam or cyber assaults. To make issues much more regarding, these unauthorized customers is also siphoning off your private information, putting a further load in your telephone’s assets and compounding the slowdown.
6. Battery is Draining Quicker
 Ever discovered your telephone all of a sudden slowing down? It’s doable that hackers are at play. They slip in unnoticed and set up hidden software program that devours your telephone’s energy – each its CPU and reminiscence. This causes apps to behave sluggish, making you wait. Shockingly, your telephone may also be recruited into a bunch of hacked units, utilized by hackers to launch spam or cyberattacks, including to the sluggishness.
Ever discovered your telephone all of a sudden slowing down? It’s doable that hackers are at play. They slip in unnoticed and set up hidden software program that devours your telephone’s energy – each its CPU and reminiscence. This causes apps to behave sluggish, making you wait. Shockingly, your telephone may also be recruited into a bunch of hacked units, utilized by hackers to launch spam or cyberattacks, including to the sluggishness.
7. Service Disruptions
 Ever confronted service points in your telephone? Surprisingly, round 68% of hacking circumstances lead to service disruptions. They push your telephone to the restrict, inflicting apps to crash, calls to drop, and texts to stall. These disruptions can stretch on for days, inflicting actual frustration. Astonishingly, about 56% of these affected face monetary losses.
Ever confronted service points in your telephone? Surprisingly, round 68% of hacking circumstances lead to service disruptions. They push your telephone to the restrict, inflicting apps to crash, calls to drop, and texts to stall. These disruptions can stretch on for days, inflicting actual frustration. Astonishingly, about 56% of these affected face monetary losses.
8. Surprising Invoice Costs
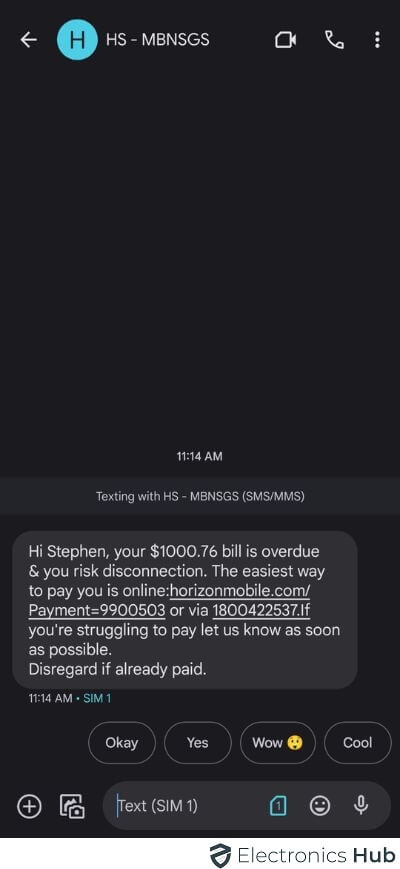 Shocked by heavy telephone payments? They manipulate your machine to make premium calls or texts, piling up prices you by no means licensed. On common, victims find yourself coping with practically $200 in additional charges. It’s staggering – about 47% of these affected additionally face monetary losses. Hacking doesn’t simply decelerate your telephone; it additionally hits your pockets arduous.
Shocked by heavy telephone payments? They manipulate your machine to make premium calls or texts, piling up prices you by no means licensed. On common, victims find yourself coping with practically $200 in additional charges. It’s staggering – about 47% of these affected additionally face monetary losses. Hacking doesn’t simply decelerate your telephone; it additionally hits your pockets arduous.
What to do When Your Cellphone is Hacked?
1. Delete Suspicious Apps
- Guarantee app permissions: Earlier than eradicating an app, evaluate its permissions. If pointless entry is granted, revoke it.
- Look ahead to odd behaviour: If apps open autonomously or battery drains swiftly, a suspicious app might be the trigger. Scan for malware and delete uncertain apps.
- Obtain cautiously: Follow trusted sources like Google Play Retailer or Apple App Retailer. Make away from third-party websites.
2. Run Anti Malware Software program
Safeguarding your telephone in opposition to malware is paramount. Malicious software program can infiltrate by way of deceitful hyperlinks, contaminated attachments. As soon as inside, it will possibly plunder your personal information—passwords, bank card information, contacts—whereas additionally exploiting your machine for spam and assaults. Counter this menace by utilizing anti-malware software program.
3. Reset Cellphone
 Resetting your telephone is a final resort to remove malware. This course of erases all information, apps, and settings. Previous to resetting, again up your information to a pc, cloud service, or SD card. Entry the Settings menu, select “Reset,” after which “Erase all information.”
Resetting your telephone is a final resort to remove malware. This course of erases all information, apps, and settings. Previous to resetting, again up your information to a pc, cloud service, or SD card. Entry the Settings menu, select “Reset,” after which “Erase all information.”
4. Change Passwords and Allow 2FA
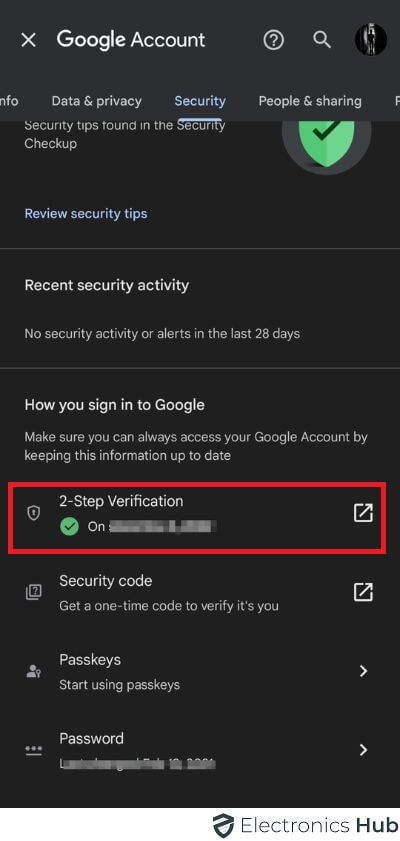 Put up-phone hack, altering passwords is significant. Hackers might have your previous passwords, so replace all accounts—electronic mail, banks, social media—with robust, distinctive ones. For added safety, activate two-factor authentication (2FA). This additional layer calls for a phone-entered code together with a password. Google’s examine reveals 2FA slashes account breach danger by as much as 99%.
Put up-phone hack, altering passwords is significant. Hackers might have your previous passwords, so replace all accounts—electronic mail, banks, social media—with robust, distinctive ones. For added safety, activate two-factor authentication (2FA). This additional layer calls for a phone-entered code together with a password. Google’s examine reveals 2FA slashes account breach danger by as much as 99%.
5. Inform Your Contacts
Alert your contacts concerning the telephone hack to stop them from falling sufferer to suspicious messages or calls. Hackers may exploit your telephone to ship scams or emails to your contacts. By notifying them by way of textual content, electronic mail, or social media, you may inform them to acknowledge potential dangers.
6. Contact Service Supplier
 Attain out to your service supplier urgently to dam your telephone’s quantity and thwart hackers. Illegal calls or texts is likely to be made utilizing your telephone. By securing your quantity, you may determine fraudulent actions. Join by way of telephone, electronic mail, or chat, detailing the hacking incident and your want for quantity blocking.
Attain out to your service supplier urgently to dam your telephone’s quantity and thwart hackers. Illegal calls or texts is likely to be made utilizing your telephone. By securing your quantity, you may determine fraudulent actions. Join by way of telephone, electronic mail, or chat, detailing the hacking incident and your want for quantity blocking.
7. Disconnect Your Cellphone From Web
 Defend your information by disconnecting your telephone from the web. Hackers exploit your machine to transmit and obtain information, risking your contacts, images, and looking historical past. Reducing off their entry is essential. Disable Wi-Fi and mobile information or activate airplane mode to sever the connection.
Defend your information by disconnecting your telephone from the web. Hackers exploit your machine to transmit and obtain information, risking your contacts, images, and looking historical past. Reducing off their entry is essential. Disable Wi-Fi and mobile information or activate airplane mode to sever the connection.
8. Set Password Supervisor
Elevate your safety with a password supervisor—a software that shops and organizes your passwords. Within the wake of a telephone hack, it turns into a vital defend, serving to you handle passwords and thwart hackers’ entry to your accounts.
What Are The Possibilities/Methods That The Telephones Could be Hacked?
1. False Ads
“Keep cautious of hackers’ misleading advertisements manipulate as real gives. These advertisements promise freebies, reductions, and extra. Nevertheless, clicking them can result in malicious web sites that plant malware in your telephone.
2. Malware
Malware, dangerous software program, poses threats to your telephone’s safety. It sneaks in by malicious hyperlinks, contaminated attachments, or faux apps. As soon as infiltrated, it will possibly swipe delicate information—passwords, bank card information, contacts—and misuse your telephone for spam or assaults.
3. Public Wi-Fi
 Public Wi-Fi networks are dangerous as they’re typically unsecured, letting hackers intercept your information. In case you share private information like passwords or bank card particulars whereas related to such networks, hackers can steal it.
Public Wi-Fi networks are dangerous as they’re typically unsecured, letting hackers intercept your information. In case you share private information like passwords or bank card particulars whereas related to such networks, hackers can steal it.
Greatest Methods to Defend Your Cellphone From Hackers
- Flip off the Bluetooth when not in use
- Don’t save info like passwords or bank card info in your telephone
- Repeatedly monitor your telephone to search out out uncommon exercise
- Replace your software program and working system
- Create a singular password to your telephone
- Use a password lock for delicate apps
Conclusion
In a digitally related world, vigilance is essential. A staggering 76% of hacking circumstances contain suspicious apps, whereas 64% result in shock invoice spikes. 68% of hacks trigger service disruptions. Prioritize robust, distinctive passwords and activate two-factor authentication (2FA). Swift motion is essential – 47% of victims face monetary loss on account of unexplained costs. Public Wi-Fi? Dangerous. Hackers exploit it to intercept information. Keep in mind, your telephone might be an unwitting confederate in cybercrimes. Safeguard it in opposition to malware, be cautious with apps, and preserve a watchful eye for uncommon behaviour. Your proactive efforts guarantee your telephone stays safe
Cellphone Hacked – FAQs
Ans: Certo Cell Safety finds a menace in your machine
This free app will help you scan your machine and discover out for certain if there’s malicious software program put in in your Android system.
Ans: If you wish to cease telephone monitoring, you may change your telephone settings, change to a non-public browser, configure your app permissions extra fastidiously, or use a VPN.
Ans: Sure, a manufacturing unit reset can take away most malware and return your telephone to its authentic state. Nevertheless, some superior malware can persist even after a manufacturing unit reset, so combining it with different safety measures is beneficial.
Ans: Public Wi-Fi networks might be dangerous as they’re extra vulnerable to hacking. Keep away from accessing delicate info on public Wi-Fi, and think about using a digital personal community (VPN) for added safety.
Ans: Phishing makes an attempt typically contain unsolicited emails or messages asking for private info, passwords, or fee particulars. Be cautious of misspellings, generic greetings, and pressing requests.