Menace actors are utilizing Android Package deal (APK) recordsdata with unknown or unsupported compression strategies to elude malware evaluation.
That is based on findings from Zimperium, which discovered 3,300 artifacts leveraging such compression algorithms within the wild. 71 of the recognized samples will be loaded on the working system with none issues.
There isn’t any proof that the apps had been accessible on the Google Play Retailer at any time limit, indicating that the apps had been distributed by way of different means, usually through untrusted app shops or social engineering to trick the victims into sideloading them.

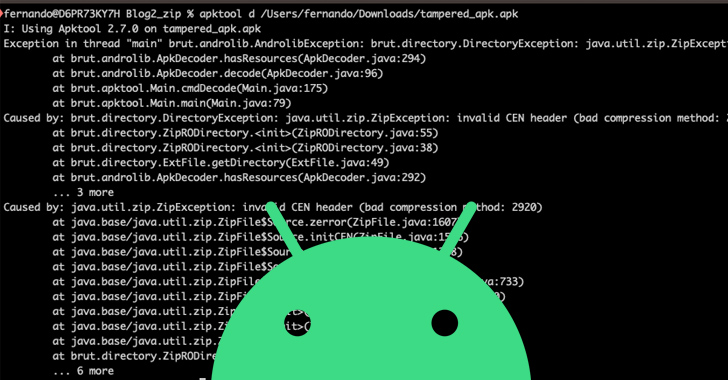
The APK recordsdata use “a way that limits the opportunity of decompiling the appliance for a lot of instruments, decreasing the probabilities of being analyzed,” safety researcher Fernando Ortega mentioned. “As a way to try this, the APK (which is in essence a ZIP file), is utilizing an unsupported decompression methodology.”
The benefit of such an strategy is its capability to withstand decompilation instruments, whereas nonetheless with the ability to be put in on Android gadgets whose working system model is above Android 9 Pie.
The Texas-based cybersecurity agency mentioned it began its personal evaluation after a publish from Joe Safety on X (beforehand Twitter) in June 2023 about an APK file that exhibited this conduct.

Android packages use the ZIP format in two modes, one with out compression and one utilizing the DEFLATE algorithm. The essential discovering right here is that APKs packed utilizing unsupported compression strategies will not be installable on handsets operating Android variations under 9, however they work correctly on subsequent variations.
As well as, Zimperium found that malware authors are additionally intentionally corrupting the APK recordsdata by having filenames with greater than 256 bytes and malformed AndroidManifest.xml recordsdata to set off crashes on evaluation instruments.
The disclosure comes weeks after Google revealed that menace actors are leveraging a way referred to as versioning to evade its Play Retailer’s malware detections and goal Android customers.