Whereas IT safety managers in firms and public administrations depend on the idea of Zero Belief, APTS (Superior Persistent Threats) are placing its sensible effectiveness to the take a look at. Analysts, however, perceive that Zero Belief can solely be achieved with complete perception into one’s personal community.
Only recently, an assault believed to be perpetrated by the Chinese language hacker group Storm-0558 focused a number of authorities businesses. They used faux digital authentication tokens to entry webmail accounts operating on Microsoft’s Outlook service. On this incident, the attackers stole a signing key from Microsoft, enabling them to problem useful entry tokens for Outlook Internet Entry (OWA) and Outlook.com and to obtain emails and attachments. Resulting from a plausibility test error, the digital signature, which was solely supposed for personal buyer accounts (MSA), additionally labored within the Azure Energetic Listing for enterprise prospects.
Embracing the Zero Belief Revolution
In line with a report by vendor Okta (State of Zero-Belief Safety 2022) 97% of respondents are already engaged in a zero-trust technique or plan to implement one inside the subsequent 18 months. This has elevated the proportion of Zero Belief advocates from 24% (2021) to 55% (2022). The safety mannequin often known as Zero Belief is an overarching safety technique designed to constantly audit and confirm entry to sources, each internally and externally. Many organizations are embracing this safety technique based mostly on the precept that community gadgets and customers should consistently show their id, as they don’t seem to be routinely trusted.
Zero Belief depends on steady monitoring and dynamic management for purposes, customers and gadgets. It limits entry to sources to absolutely the minimal and all identities on the platform are evaluated utilizing the identical standards as hosts. The overarching purpose is to boost safety by granting entry solely to those that constantly show their id and whose conduct is beneath fixed scrutiny.
Peering Previous the Perimeter: What’s Actually Occurring in Your Community
Id and entry administration (IAM) undoubtedly play a elementary function in Zero Belief. Sadly, fixed verification of customers’ identities proves ineffective in circumstances of stolen id. Furthermore, attackers can bypass these methods by manipulating meta-information, such because the geolocation of a possible login, utilizing a spoofed VPN tackle. IDS/IPS methods are tasked with detecting suspicious or unauthorized exercise, virus infections, malware and ransomware, zero-day assaults, SQL injection and extra. Nevertheless, IDS/IPS methods usually solely detect recognized signatures, corresponding to beforehand recognized malicious domains or IP addresses. If a site hasn’t been flagged as malicious beforehand, typical safety options could overlook it, permitting attackers to take advantage of the weak hyperlink within the chain. Consequently, conventional cybersecurity methods can typically falter with regards to actualizing Zero Belief in motion.
To implement a Zero Belief safety technique successfully, organizations are more and more turning to community evaluation instruments, as not too long ago advisable by the analyst agency Forrester (“The Community Evaluation and Visibility Panorama, Q1 2023”). In line with the Forrester report, safety and threat professionals ought to make use of Community Detection and Response (NDR) instruments to watch their networks, seek for threats, detect purposes and belongings, and seize malicious information packets. These actions contribute to the efficient detection of threats inside IT infrastructures.
Community Detection & Response (NDR): The Unsung Hero of Zero Belief Safety
NDR options are important for making a resilient and efficient Zero Belief structure. They supply real-time visibility into community site visitors, monitor consumer behaviour and machine exercise, and allow swift detection and response to suspicious community operations or anomalous actions. This visibility extends to all working methods, utility servers, and IoT gadgets.
Forrester has highlighted that the importance of enterprise networks in cyberattacks is usually underestimated. Cybercriminals use faux identities or zero-day exploits to infiltrate company networks, then transfer laterally throughout the community to seek for targets, acquire entry to privileged methods, set up ransomware or different malware, and exfiltrate company information. NDR facilitates inside reconnaissance—the place the attacker surveys potential targets—or lateral motion detection when the attacker is already within the community. NDR methods collect information from all switches and function completely with out brokers, which is probably not installable in lots of environments.
Machine Studying NDR: The New Commonplace in Anomaly Detection
With Machine Studying (ML), Community Detection and Response (NDR) methods are able to detecting site visitors anomalies with out counting on pre-stored, recognized “Indicators of Compromise” (IoCs). These ML fashions are designed to be constantly educated, enabling them to detect new threats and assault strategies. This method considerably accelerates the detection of malicious actions and allows early assault mitigation. Furthermore, it aids in figuring out unknown, suspicious behaviour and minimizes the time attackers can dwell unnoticed inside a community, thereby enhancing total safety.
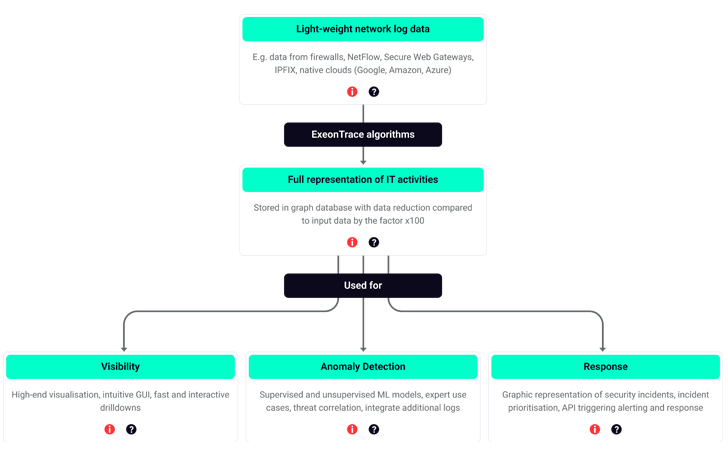 |
| How ExeonTrace, a number one ML-based NDR, analyzes meta information with a purpose to present community visibility, anomaly detection and incident response. |
Machine studying algorithms set up the baseline of regular community behaviour by analyzing information and algorithms to study what’s “regular” for the community in communication patterns. These algorithms are educated to study what constitutes “regular” exercise for the community, thereby enabling them to detect deviations from this established baseline. Examples of such deviations embody suspicious connections, uncommon information transfers, site visitors patterns that fall outdoors established norms, lateral actions inside the community, information exfiltration, and extra.
Exeon is a number one NDR options supplier headquartered in Switzerland with a robust information base and a basis rooted in cybersecurity experience. The NDR platform, Exeon Hint, provides complete community monitoring powered by superior Machine Studying know-how. It allows automated detection of potential cyber threats, making it a vital device for Safety Operations Middle (SOC) groups and Chief Info Safety Officers (CISOs), who’re dedicated to implementing and sustaining a strong Zero Belief safety technique.
Fascinated with seeing how NDR from Exeon fortifies cybersecurity and allows efficient Zero Belief implementations? Take into account reserving a demo with Exeon to witness firsthand how Zero Belief and cyber resilience are introduced into motion!

