
This week we’ve a number of reviews of recent ransomware households concentrating on the enterprise, named Cactus and Akira, each more and more lively as they aim the enterprise.
The Cactus operation launched in March and has been discovered to use VPN vulnerabilities to realize entry to company networks.
The encryptor requires an encryption key to be handed on the command line to decrypt the configuration file utilized by the malware. If the right configuration key just isn’t handed, the encryptor will terminate, and nothing will probably be encrypted.
This technique is to evade detection by safety researchers and antivirus software program.
BleepingComputer additionally reported on the Akira ransomware, a brand new operation launched in March that rapidly amassed sixteen victims on its knowledge leak website.
The Akira operation makes use of a retro-looking knowledge leak website that requires you to enter instructions as for those who’re utilizing a Linux shell.
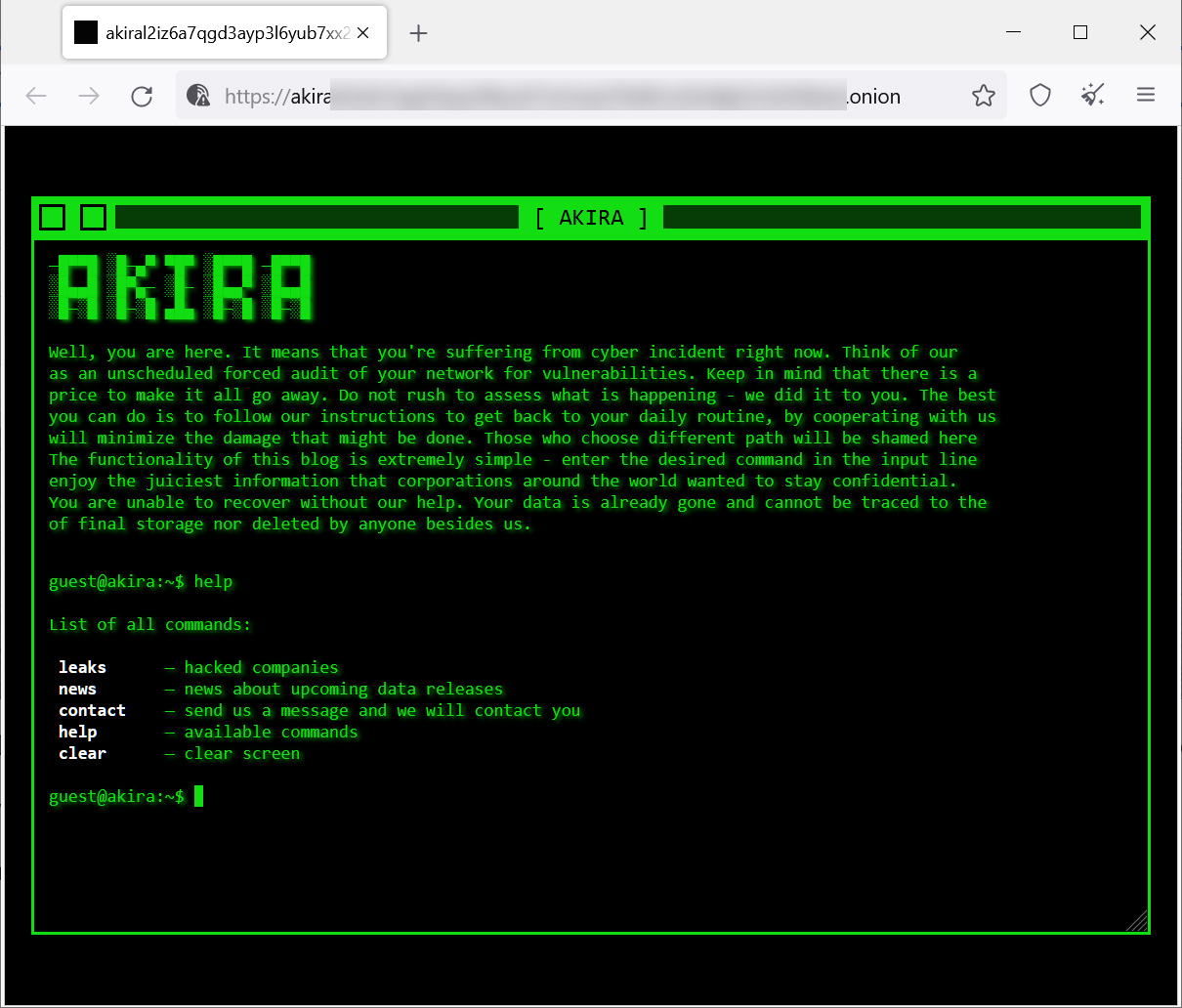
Supply: BleepingComputer
We additionally realized about new assaults and important builders in earlier ones.
On Could seventh, multinational automation agency ABB suffered a Black Basta ransomware assault, disrupting their community and factories.
ABB is the developer of quite a few SCADA and industrial management programs (ICS) for vitality suppliers and manufacturing, elevating issues about whether or not knowledge was stolen and what it contained.
Information additionally got here out final week that the Cash Message ransomware operation printed supply code belonging to MSI, which contained personal keys for Intel Boot Guard.
Binarly warned that these leaked keys may very well be used to digitally signal UEFI malware that may bypass Intel Boot Guard on MSI units.
Lastly, researchers and regulation enforcement launched new reviews:
Contributors and people who supplied new ransomware data and tales this week embody: @PolarToffee, @malwrhunterteam, @Ionut_Ilascu, @demonslay335, @struppigel, @malwareforme, @BleepinComputer, @billtoulas, @FourOctets, @serghei, @VK_Intel, @fwosar, @LawrenceAbrams, @Seifreed, @jorntvdw, @DanielGallagher, @LabsSentinel, @BrettCallow, @matrosov, @binarly_io, @Checkmarx, @KrollWire, @yinzlovecyber, and @pcrisk.
Could seventh 2023
Meet Akira — A brand new ransomware operation concentrating on the enterprise
The brand new Akira ransomware operation has slowly been constructing a listing of victims as they breach company networks worldwide, encrypt information, after which demand million-dollar ransoms.
New Cactus ransomware encrypts itself to evade antivirus
A brand new ransomware operation known as Cactus has been exploiting vulnerabilities in VPN home equipment for preliminary entry to networks of “massive industrial entities.”
New STOP ransomware variant
PCrisk discovered a brand new STOP ransomware variant that appends the .qore extension.
Could eighth 2023
Intel investigating leak of Intel Boot Guard personal keys after MSI breach
Intel is investigating the leak of alleged personal keys utilized by the Intel Boot Guard safety characteristic, doubtlessly impacting its capacity to dam the set up of malicious UEFI firmware on MSI units.
Could ninth 2023
New GlobeImposter ransomware variant
PCrisk discovered a brand new GlobeImposter ransomware variant that appends the .Struggling extension and drops a ransom notice named how_to_back_files.html.
New Solix ransomware
PCrisk discovered a brand new ransomware variant that appends the .Solix extension.
New MedusaLocker ransomware
PCrisk discovered a brand new ransomware variant that appends the .newlocker extension and drops a ransom notice named HOW_TO_RECOVER_DATA.html.
New BrightNite ransomware
PCrisk discovered a brand new ransomware variant that appends the .BrightNight extension and drops a ransom notice named README.txt.
New STOP ransomware variant
PCrisk discovered a brand new STOP ransomware variant that appends the .gash extension.
Could tenth 2023
New ransomware decryptor recovers knowledge from partially encrypted information
A brand new ‘White Phoenix’ ransomware decryptor permits victims to partially recuperate information encrypted by ransomware strains that use intermittent encryption.
New Xorist ransomware variant
PCrisk discovered a brand new Xorist ransomware variant that appends the .SIGSCH extension and drops a ransom notice named README_SIGSCH.txt.
New Military Sign ransomware
PCrisk discovered a brand new Xorist ransomware variant that appends the .zipp3rs extension.
Could eleventh 2023
Babuk code utilized by 9 ransomware gangs to encrypt VMWare ESXi servers
An rising variety of ransomware operations are adopting the leaked Babuk ransomware supply code to create Linux encryptors concentrating on VMware ESXi servers.
Multinational tech agency ABB hit by Black Basta ransomware assault
Swiss multinational firm ABB, a number one electrification and automation know-how supplier, has suffered a Black Basta ransomware assault, reportedly impacting enterprise operations.
New STOP ransomware variant
PCrisk discovered a brand new STOP ransomware variant that appends the .gatz extension.
Could twelfth 2023
FBI: Bl00dy Ransomware targets training orgs in PaperCut assaults
The FBI and CISA issued a joint advisory to warn that the Bl00dy Ransomware gang is now additionally actively exploiting a PaperCut remote-code execution vulnerability to realize preliminary entry to networks.
That is it for this week! Hope everybody has a pleasant weekend!
