A Portuguese-language spy ware known as WebDetetive has been used to compromise greater than 76,000 Android telephones in recent times throughout South America, largely in Brazil. WebDetetive can be the newest telephone spy ware firm in current months to have been hacked.
In an undated be aware seen by TechCrunch, the unnamed hackers described how they discovered and exploited a number of safety vulnerabilities that allowed them to compromise WebDetetive’s servers and entry to its person databases. By exploiting different flaws within the spy ware maker’s net dashboard — utilized by abusers to entry the stolen telephone knowledge of their victims — the hackers mentioned they enumerated and downloaded each dashboard file, together with each buyer’s e mail handle.
The hackers mentioned that dashboard entry additionally allowed them to delete sufferer units from the spy ware community altogether, successfully severing the connection on the server stage to stop the gadget from importing new knowledge. “Which we positively did. As a result of we might. As a result of #fuckstalkerware,” the hackers wrote within the be aware.
The be aware was included in a cache containing greater than 1.5 gigabytes of knowledge scraped from the spy ware’s net dashboard. That knowledge included details about every buyer, such because the IP handle they logged in from, and buy historical past. The info additionally listed each gadget that every buyer had compromised, which model of the spy ware the telephone was working, and the kinds of knowledge that the spy ware was gathering from the sufferer’s telephone.
The cache didn’t embrace the stolen contents from victims’ telephones.
DDoSecrets, a nonprofit transparency collective that indexes leaked and uncovered datasets within the public curiosity, obtained the WebDetetive knowledge and shared it with TechCrunch for evaluation.
In complete, the info confirmed that WebDetetive had compromised 76,794 units thus far on the time of the breach. The info additionally contained 74,336 distinctive buyer e mail addresses, although WebDetetive doesn’t confirm a buyer’s e mail addresses when signing up, stopping any significant evaluation of the spy ware’s prospects.
It’s not recognized who’s behind the WebDetetive breach and the hackers didn’t present contact info. TechCrunch couldn’t independently verify the hackers’ declare that it deleted victims’ units from the community, although TechCrunch did confirm the authenticity of the stolen knowledge by matching a number of gadget identifiers within the cache towards a publicly accessible endpoint on WebDetetive’s server.
WebDetetive is a sort of telephone monitoring app that’s planted on an individual’s telephone with out their consent, typically by somebody with information of the telephone’s passcode.
As soon as planted, the app modifications its icon on the telephone’s dwelling display screen, making the spy ware tough to detect and take away. WebDetetive then instantly begins stealthily importing the contents of an individual’s telephone to its servers, together with their messages, name logs, telephone name recordings, pictures, ambient recordings from the telephone’s microphone, social media apps, and real-time exact location knowledge.
Regardless of the broad entry that these so-called “stalkerware” (or spouseware) apps should a sufferer’s private and delicate telephone knowledge, spy ware is notoriously buggy and recognized for his or her shoddy coding, which places victims’ already-stolen knowledge prone to additional compromise.
WebDetetive, meet OwnSpy
Little is understood about WebDetetive past its surveillance capabilities. It’s not unusual for spy ware makers to hide or obfuscate their real-world identities, given the reputational and authorized dangers that include producing spy ware and facilitating the unlawful surveillance of others. WebDetetive isn’t any totally different. Its web site doesn’t checklist who owns or operates WebDetetive.
However whereas the breached knowledge itself reveals few clues about WebDetetive’s directors, a lot of its roots might be traced again to OwnSpy, one other extensively used telephone spying app.
TechCrunch downloaded the WebDetetive Android app from its web site (since each Apple and Google ban stalkerware apps from their app shops), and planted the app onto a digital gadget, permitting us to investigate the app in an remoted sandbox with out giving it any actual knowledge, comparable to our location. We ran a community visitors evaluation to know what knowledge was flowing out and in of the WebDetetive app, which discovered it was a largely repackaged copy of OwnSpy’s spy ware. WebDetetive’s person agent, which it sends to the server to establish itself, was nonetheless referring to itself as OwnSpy, regardless that it was importing our digital gadget’s dummy knowledge to WebDetetive’s servers.
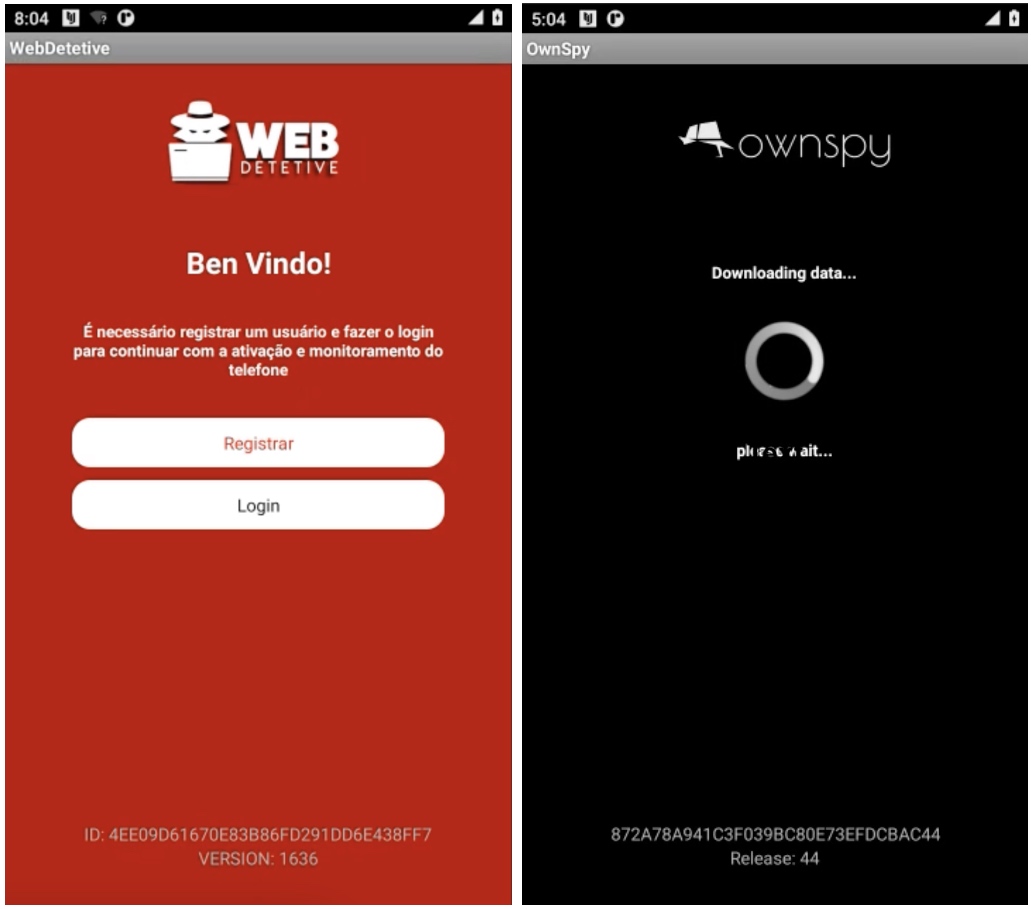
A side-by-side photograph comparability of WebDetetive (left) and OwnSpy (proper) working on Android. Picture Credit: TechCrunch
OwnSpy is developed in Spain by Cellular Improvements, a Madrid-based firm run by Antonio Calatrava. OwnSpy has operated since at the least 2010, in accordance with its web site, and claims to have 50,000 prospects, although it’s not recognized what number of units OwnSpy has compromised thus far.
OwnSpy additionally operates an affiliate mannequin, permitting others to make a fee by selling the app or providing “a brand new product to your shoppers” in return for OwnSpy taking a reduce of the income, in accordance with an archived copy of its associates web site. It’s not clear what different operational hyperlinks, if any, exist between OwnSpy and WebDetetive. Calatrava didn’t return a request for remark or present contact info for WebDetetive’s directors.
A short while after we emailed Calatrava, parts of OwnSpy’s recognized infrastructure dropped offline. A separate community visitors evaluation of OwnSpy’s app by TechCrunch discovered that OwnSpy’s spy ware app was now not functioning. WebDetetive’s app continues to perform.
Harmful assault?
WebDetetive is the second spy ware maker to be focused by a data-destructive hack in current months. LetMeSpy, a spy ware app developed by Polish developer Rafal Lidwin, shut down following a hack that uncovered and deleted victims’ stolen telephone knowledge from LetMeSpy’s servers. Lidwin declined to reply questions in regards to the incident.
By TechCrunch’s depend, at the least a dozen spy ware firms in recent times have uncovered, spilled, or in any other case put victims’ stolen telephone knowledge prone to additional compromise due to shoddy coding and simply exploitable safety vulnerabilities.
TechCrunch was unable to achieve the WebDetetive directors for remark. An e mail despatched to WebDetetive’s assist e mail handle in regards to the knowledge breach — together with whether or not the spy ware maker has backups — went unreturned. It’s not clear if the spy ware maker will notify prospects or victims of the info breach, or if it nonetheless has the info or information to take action.
Harmful assaults, though rare, might have unintended and harmful penalties for victims of spy ware. Adware usually alerts the abuser if the spy ware app stops working or is faraway from a sufferer’s telephone, and severing a connection with no security plan in place might put spy ware victims in an unsafe scenario. The Coalition In opposition to Stalkerware, which works to assist victims and survivors of stalkerware, has assets on its web site for many who suspect their telephone is compromised.
How one can discover and take away WebDetetive
Not like most telephone monitoring apps, WebDetetive and OwnSpy don’t conceal their app on an Android dwelling display screen, however as a substitute disguise themselves as an Android system-presenting Wi-Fi app.
WebDetetive is comparatively straightforward to detect. The app seems named as “WiFi” and encompasses a white wi-fi icon in a blue circle on a white background.
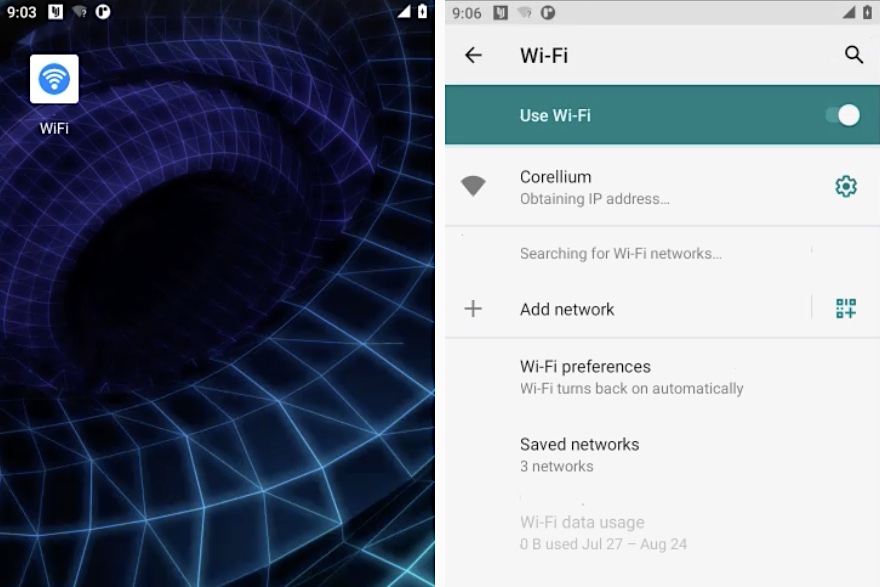
A screenshot exhibiting the “WiFi” app, which presents as a system Wi-Fi app. Nonetheless, this app is spy ware in disguise. Picture Credit: TechCrunch
When tapped and held, and the app information is considered, the app is definitely known as “Sistema.”
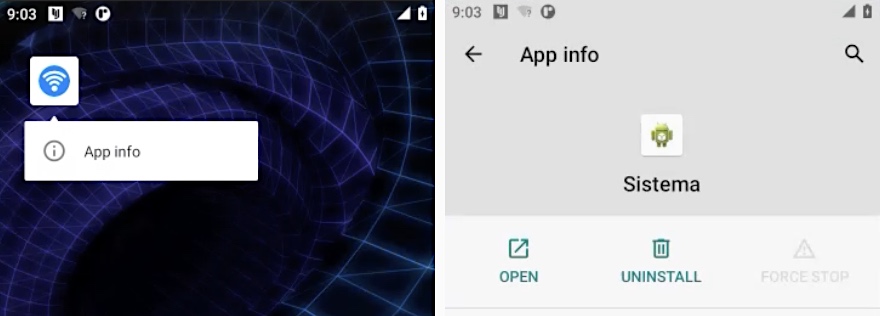
This “WiFi” app icon, when tapped, will really present as an app known as “Sistema,” designed to appear like an Android system app, however is definitely WebDetetive spy ware. Picture Credit: TechCrunch
We’ve got a common information that may enable you take away Android spy ware out of your telephone, whether it is protected to take action. You must be sure that Google Play Defend is switched on as this on-device safety function can defend towards malicious Android apps. You possibly can verify its standing from the settings menu in Google Play.
When you or somebody you recognize wants assist, the Nationwide Home Violence Hotline (1-800-799-7233) gives 24/7 free, confidential assist to victims of home abuse and violence. In case you are in an emergency scenario, name 911. The Coalition In opposition to Stalkerware additionally has assets in case you suppose your telephone has been compromised by spy ware.

