
A brand new phishing marketing campaign is abusing Microsoft Groups messages to ship malicious attachments that set up the DarkGate Loader malware.
The marketing campaign began in late August 2023, when Microsoft Groups phishing messages have been seen being despatched by two compromised exterior Workplace 365 accounts to different organizations.
These accounts have been used to trick different Microsoft Groups customers into downloading and opening a ZIP file named “Adjustments to the holiday schedule.”
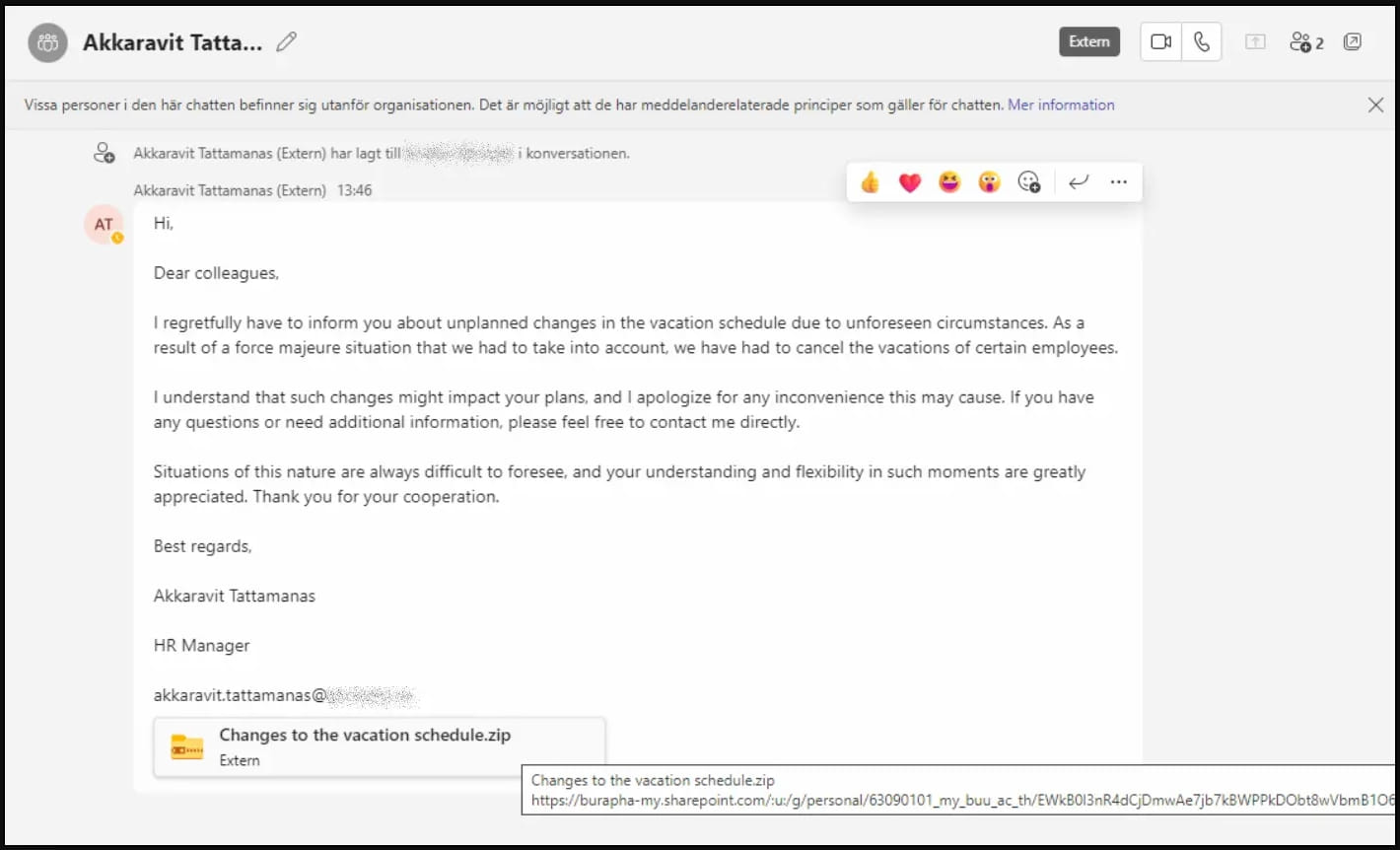
Clicking on the attachment triggers the obtain of the ZIP from a SharePoint URL and incorporates a LNK file masquerading as a PDF doc.
Researchers at Truesec analyzed the Microsoft Groups phishing marketing campaign and located that it incorporates malicious VBScript that triggers the an infection chain that results in a payload recognized because the DarkGate Loader.
To try to evade detection, the obtain course of makes use of Home windows cURL to fetch the malware’s executable and script information.
The script arrived pre-compiled, hiding its malicious code in the course of the file, starting with distinguishable “magic bytes” related to AutoIT scripts.
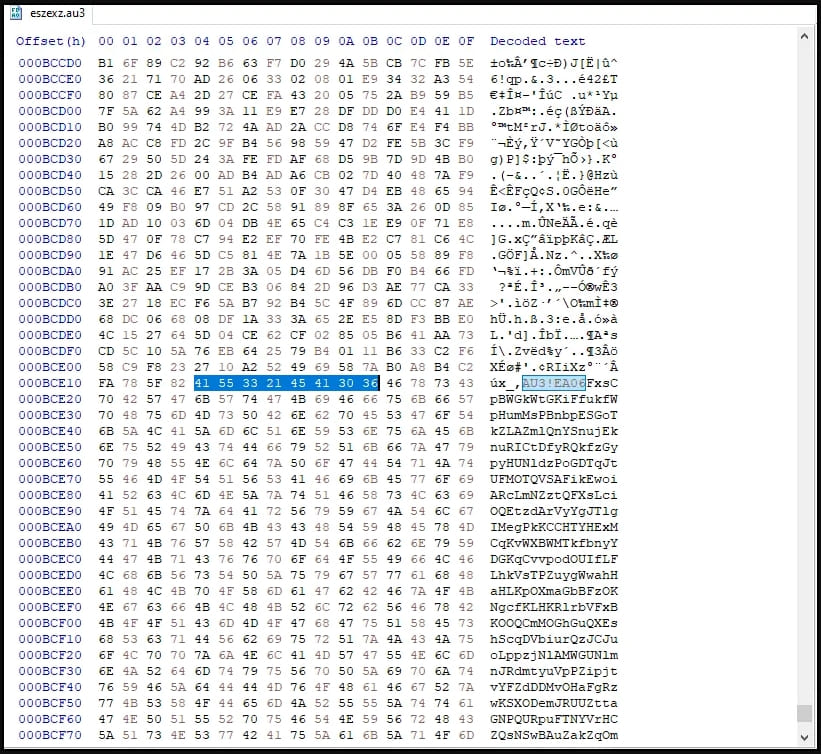
Earlier than continuing additional, the script checks if the Sophos antivirus software program is put in on the focused machine, and if it isn’t, it deobfuscates further code and launches the shellcode.
The shellcode makes use of a way known as “stacked strings” to assemble the DarkGate Home windows executable and cargo it in reminiscence.
Microsoft Groups phishing
The marketing campaign seen by Truesec and Deutsche Telekom CERT makes use of compromised Microsoft Groups accounts to ship the malicious attachments to different Groups organizations.
Microsoft Groups phishing was beforehand demonstrated in a June 2023 report by Jumpsec, who found a method to ship malicious messages to different organizations by means of phishing and social engineering, which is analogous to what we see within the reported assault.
Regardless of the stir attributable to this discovery, Microsoft determined to not tackle the chance. As a substitute, recommending that admins apply secure configurations like narrow-scoped allow-lists and disable exterior entry if communication with exterior tenants is not wanted.
A device {that a} Purple Teamer launched in July 2023 streamlined this Microsoft Groups phishing assault, additional rising the chance of it being abused within the wild.
Nonetheless, there isn’t any indication that this methodology is concerned within the assault chain of the not too long ago noticed marketing campaign.
DarkGate opens up
DarkGate has been circulating since 2017, seeing restricted use by a small circle of cybercriminals who used it in opposition to very particular targets.
It’s a potent malware that helps a variety of malicious actions, together with hVNC for distant entry, cryptocurrency mining, reverse shell, keylogging, clipboard stealing, and data stealing (information, browser information).
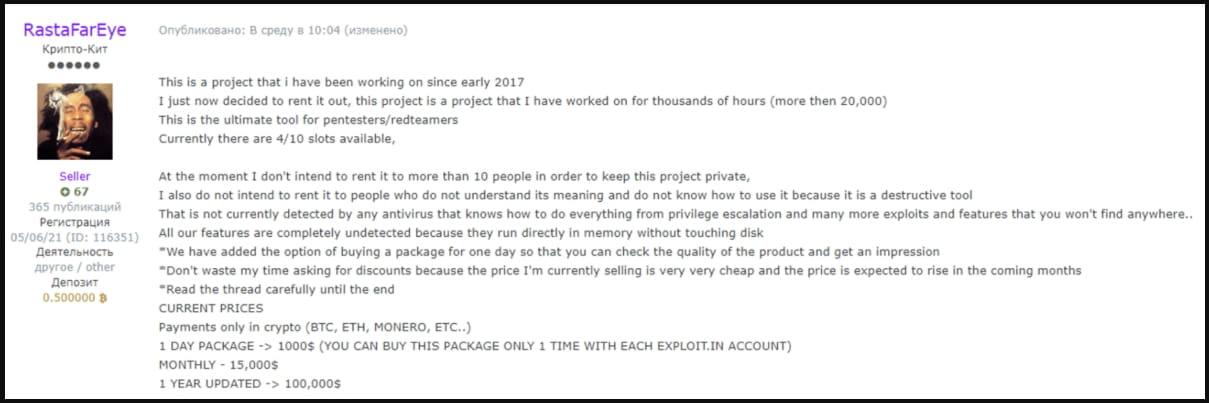
In June 2023, ZeroFox reported that somebody claiming to be the unique creator of DarkGate tried to promote entry to the malware to 10 folks for the absurd value of $100k/12 months.
Within the following months, there have been a number of stories of DarkGate distribution ramping up and utilizing varied channels, together with phishing and malvertising.
Whereas DarkGate might not be a widespread risk but, its increasing concentrating on and adoption of a number of an infection avenues make it an rising risk to observe intently.
