A brand new phishing assault is leveraging Fb Messenger to propagate messages with malicious attachments from a “swarm of pretend and hijacked private accounts” with the final word aim of taking up the targets’ accounts.
“Originating but once more from a Vietnamese-based group, this marketing campaign makes use of a tiny compressed file attachment that packs a robust Python-based stealer dropped in a multi-stage course of full of straightforward but efficient obfuscation strategies,” Guardio Labs researcher Oleg Zaytsev mentioned in an evaluation revealed over the weekend.
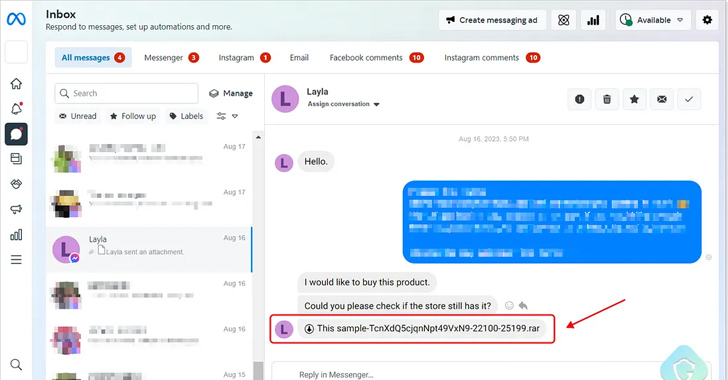
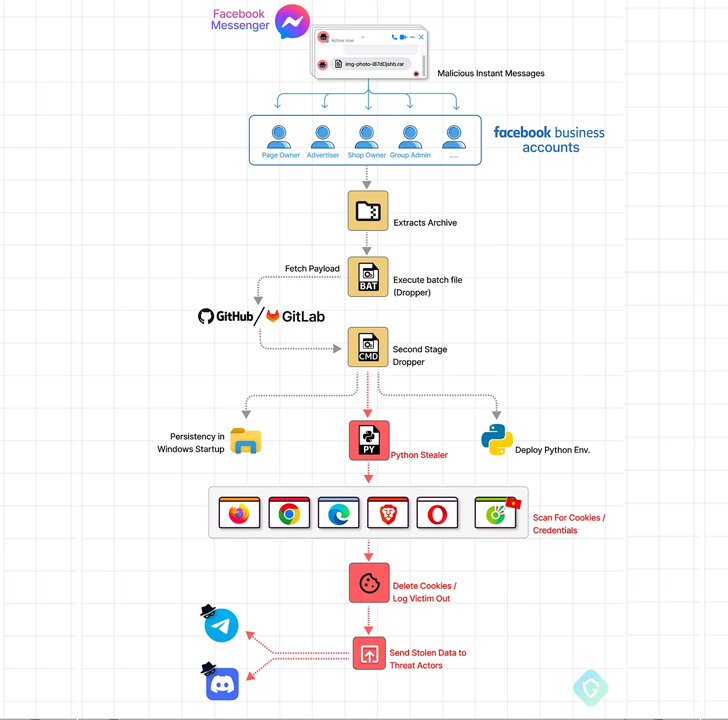
In these assaults, dubbed MrTonyScam, potential victims are despatched messages that entice them into clicking on the RAR and ZIP archive attachments, resulting in the deployment of a dropper that fetches the next-stage from a GitHub or GitLab repository.
This payload is one other archive file that accommodates a CMD file, which, in flip, harbors an obfuscated Python-based stealer to exfiltrate all cookies and login credentials from totally different net browsers to an actor-controlled Telegram or Discord API endpoint.

A intelligent tactic adopted by the adversary entails deletes all cookies after stealing them, successfully logging victims out of their very own accounts, at which level the scammers hijack their periods utilizing the stolen cookies to vary their passwords and seize management of them.
The risk actor’s hyperlinks to Vietnam comes from the presence of Vietnamese language references within the supply code of the Python stealer and the inclusion of Cốc Cốc, a Chromium-based browser common within the nation.
Although triggering the an infection requires consumer interplay to obtain a file, unzip, and execute the attachment, Guardio Labs discovered that the marketing campaign has witnessed a excessive success charge the place 1 out of 250 victims are estimated to have been contaminated over the past 30 days alone.
A majority of the compromises have been reported within the U.S., Australia, Canada, France, Germany, Indonesia, Japan, Nepal, Spain, the Philippines, and Vietnam, amongst others.
“Fb Accounts with fame, vendor ranking, and excessive variety of followers will be simply monetized on darkish markets,” Zaytsev mentioned. “These are used to achieve a broad viewers to unfold ads in addition to extra scams.”
Manner Too Weak: Uncovering the State of the Id Assault Floor
Achieved MFA? PAM? Service account safety? Learn the way well-equipped your group really is towards id threats
The disclosure comes days after WithSecure and Zscaler ThreatLabz detailed new Ducktail and Duckport campaigns that concentrate on Meta Enterprise and Fb accounts utilizing malverposting techniques.
“The Vietnamese-centric aspect of those threats and excessive diploma of overlaps by way of capabilities, infrastructure, and victimology suggests lively working relationships between numerous risk actors, shared tooling and TTPs throughout these risk teams, or a fractured and service-oriented Vietnamese cybercriminal ecosystem (akin to ransomware-as-a-service mannequin) centered round social media platforms resembling Fb,” WithSecure famous.