Whenever you roll out a safety product, you assume it would fulfill its function. Sadly, nevertheless, this typically seems to not be the case. A brand new report, produced by Osterman Analysis and commissioned by Silverfort, reveals that MFA (Multi-Issue Authentication) and PAM (Privileged Entry Administration) options are virtually by no means deployed comprehensively sufficient to supply resilience to id threats. As nicely, service accounts – that are usually past the scope of safety of those controls – are alarmingly uncovered to malicious compromise. These findings and lots of extra could be present in “The State of the Identification Assault Floor: Insights Into Vital Safety Gaps,” the primary report that analyzes organizational resilience to id threats.
What’s the “Identification Assault Floor”?
The id assault floor is any organizational useful resource that may be accessed by way of username and password. The principle manner that attackers goal this assault floor is thru using compromised consumer credentials. On this manner, the id assault floor differs considerably from different assault surfaces. When focusing on endpoints, for instance, attackers must develop modern malware and zero-day exploits. However on the earth of id the default assault instrument is legit usernames and passwords. And with an estimated 24B username-password combos accessible on the Darkish Internet, this implies the one work attackers have to do is acquire the preliminary entry.
However I Have MFA and PAM in Place to Forestall Assaults
Do you, although? In keeping with the report, which summarizes findings from 600 id safety professionals surveyed around the globe, the overwhelming majority of organizations have MFA and PAM options in place but stay uncovered to assaults. Here is why:
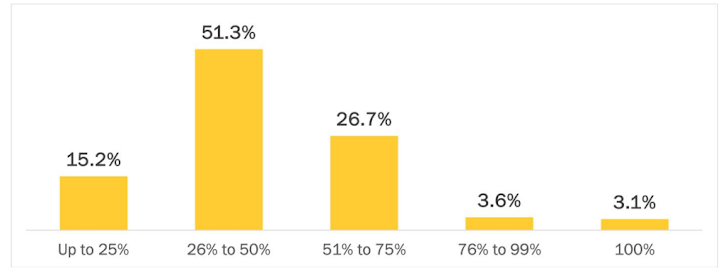
Lower than 7% of organizations have MFA safety for almost all of their crucial assets
One of many questions the survey requested was: What quantity of the next assets and entry strategies are you at present capable of defend with MFA?
- Desktop logins (e.g. Home windows, Mac)
- VPN and different distant connection strategies
- RDP
- Command-line distant entry (e.g. PowerShell, PsExec)
- SSH
- Homegrown and legacy apps
- IT infrastructure (e.g. administration consoles)
- VDI
- Virtualization platforms and hypervisors (e.g. VMware, Citrix)
- Shared community drives
- OT techniques
This graph summarizes the outcomes:
These numbers suggest a crucial hole, since a useful resource with out MFA is a useful resource that an adversary can seamlessly entry utilizing compromised credentials. Translating this to a real-life state of affairs, a risk actor utilizing command-line instrument that is not protected with MFA – akin to PsExec or Distant PowerShell – will encounter no obstacles when transferring throughout a community with the intention to plant a ransomware payload on a number of machines.
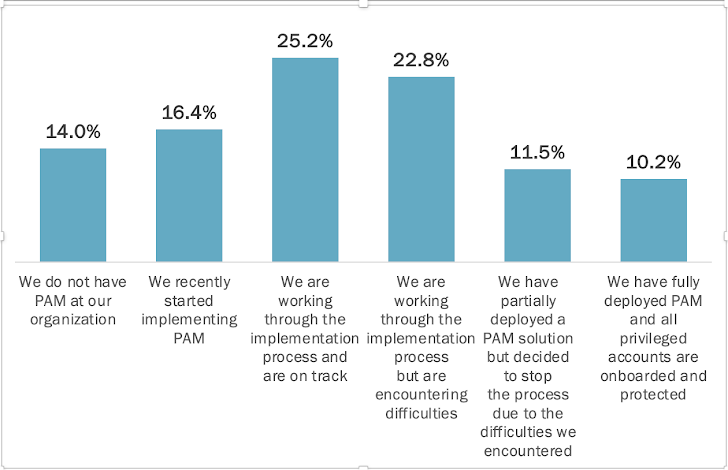
Solely 10.2% of organizations have a completely onboarded PAM resolution
PAM options are infamous for lengthy, complicated deployments, however how dangerous is it actually? The report reveals the reply: It is dangerous. Right here is an aggregation of respondents’ solutions to the query “The place are you in your PAM implementation journey?”
As you possibly can see, most organizations are caught someplace alongside their PAM journey, which implies at the very least a few of their privileged customers are uncovered to assaults. And take into account that admin customers are an attackers’ quickest path to your crown jewels. Failing to guard all of them is a threat no group can afford to disregard.
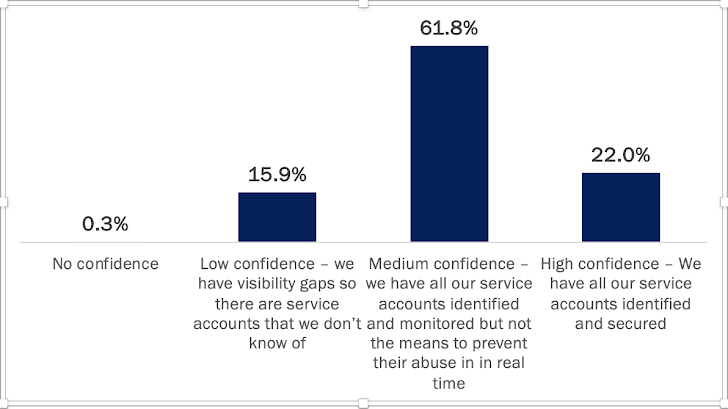
78% of organizations cannot forestall malicious entry with compromised service accounts
Service accounts are a widely known blind spot. As a result of these non-human accounts are sometimes extremely privileged but cannot be protected by MFA – in addition to the truth that they’re usually undocumented and thus unmonitored – they’re a primary goal for adversaries.
Listed here are the solutions to the query, “How assured are you in your skill to forestall attackers from utilizing service accounts for malicious entry in your setting?”
Notice that the time period “medium” here’s a bit deceptive, for the reason that absence of real-time prevention primarily voids the safety worth of with the ability to detect an account’s compromise.
How Effectively Are You Defending Your Atmosphere’s Identification Assault Floor? Use the Maturity Mannequin
The report goes past mentioning weaknesses and gaps — it provides a helpful scoring mannequin that, primarily based on aggregated outcomes throughout all of the id safety features, can reveal your stage of resilience to id threats.
The report discovered that only a few organizations – as little as 6.6% – have a disciplined and applied id safety technique in place. However use this mannequin to reply the identical questions and see how your group stacks up, and likewise what actions you want to take.
Able to see how resilient you might be to id threats? Entry the report right here.