Extra particulars have emerged a few botnet referred to as AVRecon, which has been noticed making use of compromised small workplace/house workplace (SOHO) routers as a part of a multi-year marketing campaign energetic since no less than Could 2021.
AVRecon was first disclosed by Lumen Black Lotus Labs earlier this month as malware able to executing further instructions and stealing sufferer’s bandwidth for what seems to be an unlawful proxy service made obtainable for different actors. It has additionally surpassed QakBot by way of scale, having infiltrated over 41,000 nodes positioned throughout 20 nations worldwide.
“The malware has been used to create residential proxy companies to shroud malicious exercise resembling password spraying, web-traffic proxying, and advert fraud,” the researchers stated within the report.
This has been corroborated by new findings from KrebsOnSecurity and Spur.us, which final week revealed that “AVrecon is the malware engine behind a 12-year-old service referred to as SocksEscort, which rents hacked residential and small enterprise gadgets to cybercriminals seeking to conceal their true location on-line.”
The premise for the connection stems from direct correlations between SocksEscort and AVRecon’s command-and-control (C2) servers. SocksEscort can also be stated to share overlaps with a Moldovan firm named Server Administration LLC that gives a cell VPN answer on the Apple Retailer referred to as HideIPVPN.
Black Lotus Labs informed The Hacker Information that the brand new infrastructure it recognized in reference to the malware exhibited the identical traits because the outdated AVrecon C2s.
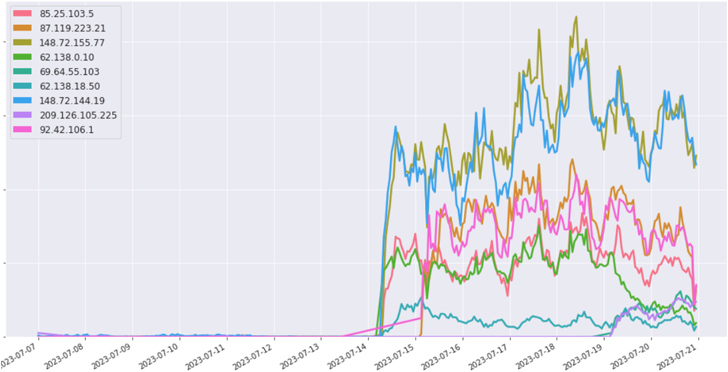 |
| The brand new SocksEscort nodes, which shifted throughout the second week of July (Supply: Lumen Black Lotus Labs) |
“We assess that the risk actors had been reacting to our publication and null-routing of infrastructure, and trying to take care of management over the botnet,” the corporate stated. “This means the actors want to additional monetize the botnet by sustaining some entry and proceed enrolling customers within the SocksEscort ‘proxy as a service.'”
Routers and different edge home equipment have turn out to be profitable assault vectors in recent times owing to the truth that such gadgets are occasionally patched towards safety points, might not help endpoint detection and response (EDR) options, and are designed to deal with increased bandwidths.
Protect Towards Insider Threats: Grasp SaaS Safety Posture Administration
Frightened about insider threats? We have got you lined! Be part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
AVRecon additionally poses a heightened risk for its capability to spawn a shell on a compromised machine, doubtlessly enabling risk actors to obfuscate their very own malicious site visitors or retrieve additional malware for post-exploitation.
“Whereas these bots are primarily being added to the SocksEscort proxy service, there was embedded performance throughout the file to spawn a distant shell,” the researchers stated.
“This might permit the risk actor the flexibility to deploy further modules, so we advise that managed safety suppliers try to analyze these gadgets of their networks, whereas house customers ought to power-cycle their gadgets.”

