
85% of IT decision-makers are prioritizing identification and entry administration investments extra extremely than different safety options. That is in line with the CISO Survival Information by Cisco’s startup arm, Cisco Investments, with cybersecurity enterprise capital corporations Forgepoint Capital, NightDragon and Team8.
The information, which explored the cybersecurity market round identification administration, information safety, software program provide chain integrity and cloud migration, resulted from interviews with Cisco clients, chief data safety officers, innovators, startup founders and different consultants.
The 30,000-foot view: Interviewees mentioned that, above all, they want extra interoperability and fewer friction, and information that’s truly helpful and understandable for decision-makers.
The important thing spending priorities the report unearthed constituted a reasonably even cut up, with consumer and machine identification being cited by the biggest variety of CISOs, adopted by cloud identification, governance and distant entry.
Cloud safety is the highest concern, with the rising space of cloud infrastructure entitlements administration an space of particular curiosity.
Soar to:
What CISOs need: Ease of use, holistic platforms, CIEMs
The important thing areas CISOs think about to be of most concern round identification entry administration, clouds and information are:
- The fragmented world of safety silos is because of a paucity of unified platforms overlaying IAMs, identification governance and administration and privileged entry administration.
- Cloud infrastructure entitlements administration is ascendent and enterprise clients are adopting these which might be provided by cloud service suppliers.
- Can we please nix the acronyms? CISOs are chafing on the proliferation of acronyms like CIEM.
On that final level, the authors of the Cisco Funding Research observe, “This pattern imposes cycles for CISOs to vet and unpack these purportedly new classes, just for them to find they’re a rehash of current options.”
High motivators for identification administration options
The highest motivators that CISOs cited for investing in identification administration options are managing consumer entry privileges, identification compliance and the fast development of organizations’ menace surfaces (Determine A).
Determine A
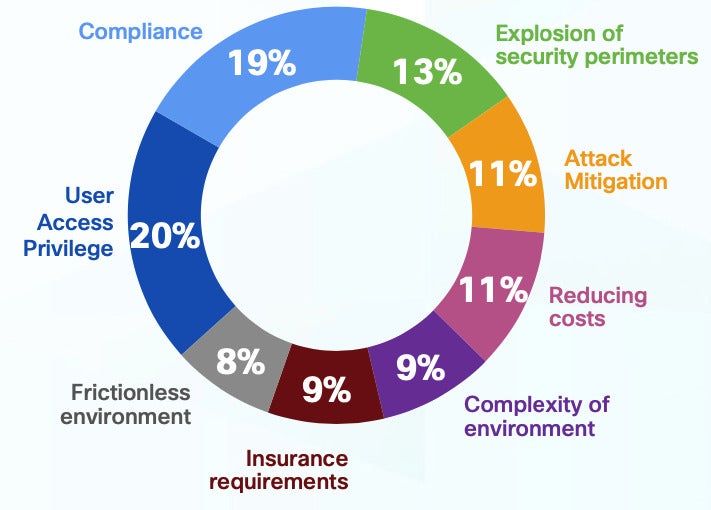
Right here’s what IT determination makers are in search of in next-generation identification platforms, in line with the research:
- Ease of integration (21% of these polled).
- Platform primarily based answer, versus single-point or endpoint choices (15%).
- Rankings from impartial analysts (15%).
- Value (11%).
- Market adoption (11%).
- Simplicity of deployment and operations (10%).
- Skill to deploy at scale simply (9%).
- Skill so as to add options simply (8%).
Decisions, decisions: Exploding choices and rising complexity are blockers
It is usually not stunning that almost all of CISOs are stymied in reaching entry and administration targets by the sheer variety of instruments accessible and the rising complexity of their very own operations.
The research famous that over one-third of the IT safety determination makers mentioned the cornucopia of identification and entry options and the growing variety of gadgets and customers concerned make adopting entry administration instruments more difficult. 53% of the CISOs polled for the report mentioned they’re challenged by “evolving identification wants” (Determine B).
Determine B
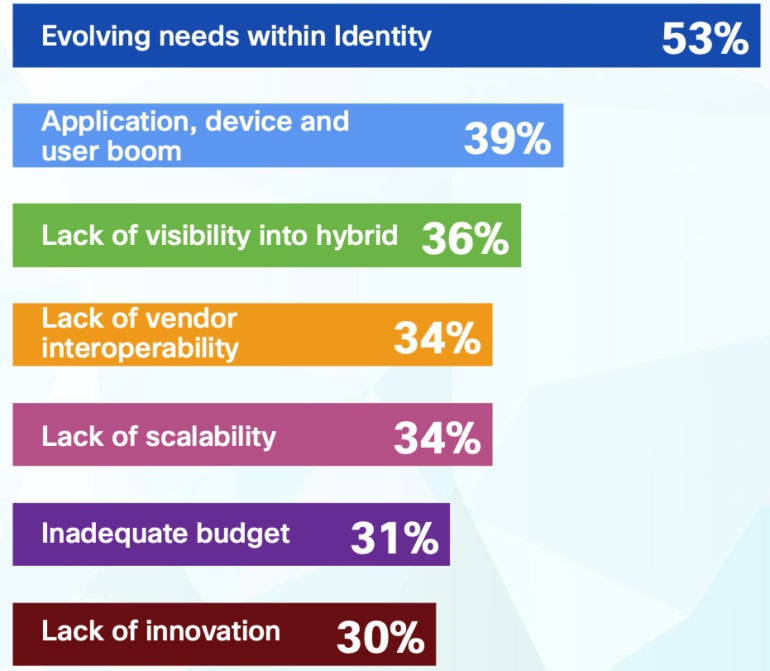
Nothing to concern however concern itself?
Cisco provided some recommendations for corporations stymied by decisions and afraid of the implications of making use of zero belief to their complicated organizations, together with downtime attributable to the mechanics of integrating new protocols: Chill, it’s not as dangerous as you suppose.
“What I’ve seen with new applied sciences is that everybody is afraid of them, however if you begin placing them in place, there’s a lot much less to be afraid of than CISOs initially thought,” mentioned Larry Lidz, Cisco’s cloud CISO, within the report. “So, I feel that the concern of adoption is way increased than the precise noise round adopting it.”
Different findings: Those that have entry to data have the keys to safety
Within the research, Forgepoint analysts mentioned controlling entry to data stays the crux of cybersecurity, with information identification and privileged entry administration being high precedence for CISOs. They famous that information safety represents yet one more hub class with many spokes, together with information entry management and information loss prevention.
SEE: Discover these cloud safety greatest practices.
NightDragon seemed on the software program provide chain: 55% of respondents mentioned they positioned compliance amongst their high three software program provide chain considerations.
“Corporations should create a holistic software program provide chain technique to handle the load,” mentioned the NightDragon report. “Finally, this includes managing OS code, the supply pipeline and third-party software program — once more, in a unified method.”
Shifting IT from price to innovation middle
Forgepoint famous that as organizations combine safety into enterprise targets, CISO’s roles will change to turn out to be much less about justifying IT investments and extra about making these initiatives a driver of strategic targets past “simply” cybersecurity.
To that time, Cisco final week launched a Lifecycle Companies program meant to assist group decision-makers on the highest ranges perceive how IT will be greater than a ledger merchandise in the price column.
Pushed by machine studying and synthetic intelligence telemetry, in line with Cisco, the service is designed to assist CISOs deliver return on funding information to bear on how they convey the enterprise worth of IT. By doing so, the corporate famous, the dialog shifts from one about justifying the price of know-how to how it’s important to innovation towards a corporation’s targets.
SEE: Obtain our information on the CISO safety menace panorama.
“Too usually IT is targeted on the supply of latest applied sciences and platforms, reasonably than enterprise targets, advantages and outcomes,” mentioned Cisco.
Cisco mentioned Lifecycle Companies will assist IT leaders scale know-how methods that help high enterprise priorities throughout their group by giving them entry to Cisco consultants, proprietary digital insights, ML/AI instruments and measurement greatest practices to report on KPIs in help of the general enterprise mission and targets of the group.
“More and more, organizations want the pliability to eat on-demand companies to be able to ship higher worth and enhanced expertise for his or her clients,” mentioned Leslie Rosenberg, vice chairman of community life-cycle companies and infrastructure companies at IDC. “The Lifecycle Companies provide from Cisco gives companies the power to align their priorities with clear and measurable outcomes to make sure their know-how investments help their enterprise, know-how and operational targets.”

