A nation-state exercise group originating from China has been linked to cyber assaults on dozens of organizations in Taiwan as a part of a suspected espionage marketing campaign.
The Microsoft Menace Intelligence staff is monitoring the exercise beneath the identify Flax Storm, which is also called Ethereal Panda.
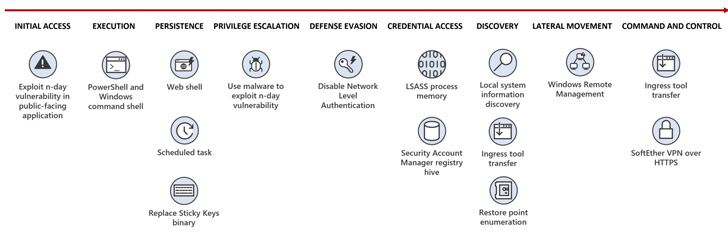
“Flax Storm good points and maintains long-term entry to Taiwanese organizations’ networks with minimal use of malware, counting on instruments constructed into the working system, together with some usually benign software program to quietly stay in these networks,” the corporate mentioned.
It additional mentioned it hasn’t noticed the group weaponize the entry to conduct data-collection and exfiltration. A majority of the targets embrace authorities companies, academic establishments, essential manufacturing, and data know-how organizations in Taiwan.
A smaller variety of victims have additionally been detected in Southeast Asia, North America, and Africa. The group is suspected to have been energetic since mid-2021.

“Ethereal Panda operations primarily deal with entities within the tutorial, know-how, and telecommunications sectors in Taiwan,” CrowdStrike notes in its description of the hacker crew. “Ethereal Panda depends closely on SoftEther VPN executables to take care of entry to sufferer networks, however has additionally been noticed deploying the GodZilla internet shell.”
The first focus of the actor revolves round persistence, lateral motion, and credential entry, with the actor using living-off-the-land (LotL) strategies and hands-on keyboard exercise to appreciate its targets.
The modus operandi is in step with menace actors’ observe of frequently updating their approaches to evade detection, banking on out there instruments within the goal atmosphere to keep away from pointless obtain and creation of customized elements.
Preliminary entry is facilitated via exploiting recognized vulnerabilities in public-facing servers and deploying internet shells like China Chopper, adopted by establishing persistent entry over Distant Desktop Protocol (RDP), deploy a VPN bridge to hook up with a distant server, and harvest credentials utilizing Mimikatz.

A noteworthy facet of the assaults is the modification of the Sticky Keys conduct to launch Activity Supervisor, enabling Flax Storm to conduct post-exploitation on the compromised system.
“In instances the place Flax Storm wants to maneuver laterally to entry different programs on the compromised community, the actor makes use of LOLBins, together with Home windows Distant Administration (WinRM) and WMIC,” the Home windows maker mentioned.
 |
| Supply: CrowdStrike |
CrowdStrike, which highlighted in February 2023 a case examine involving an Ethereal Panda intrusion, mentioned the actor possible abused an Apache Tomcat occasion to breach an unnamed group to be able to enumerate numerous sources throughout the host and dump credentials utilizing each ProcDump and Mimikatz.
The event comes three months after Microsoft uncovered one other China-linked actor named Volt Storm (aka Bronze Silhouette or Vanguard Panda), which has been noticed completely counting on LotL methods to fly beneath the radar and exfiltrate information.
Whereas crossover of ways and infrastructure amongst menace actors working out of China is not uncommon, the findings paint the image of a continuously evolving menace panorama, with adversaries shifting their tradecraft to develop into extra selective of their follow-on operations.
(The story was up to date after publication to incorporate further info shared by CrowdStrike.)