A Chinese language nation-state group has been noticed concentrating on Overseas Affairs ministries and embassies in Europe utilizing HTML smuggling methods to ship the PlugX distant entry trojan on compromised methods.
Cybersecurity agency Verify Level mentioned the exercise, dubbed SmugX, has been ongoing since not less than December 2022.
“The marketing campaign makes use of new supply strategies to deploy (most notably – HTML Smuggling) a brand new variant of PlugX, an implant generally related to all kinds of Chinese language menace actors,” Verify Level mentioned.
“Though the payload itself stays much like the one present in older PlugX variants, its supply strategies end in low detection charges, which till not too long ago helped the marketing campaign fly below the radar.”
The precise identification of the menace actor behind the operation is a bit of hazy, though current clues level within the path of Mustang Panda, which additionally shares overlaps with clusters tracked as Earth Preta, RedDelta, and Verify Level’s personal designation Camaro Dragon.
Nevertheless, the corporate mentioned there’s “inadequate proof” at this stage to conclusively attribute it to the adversarial collective.
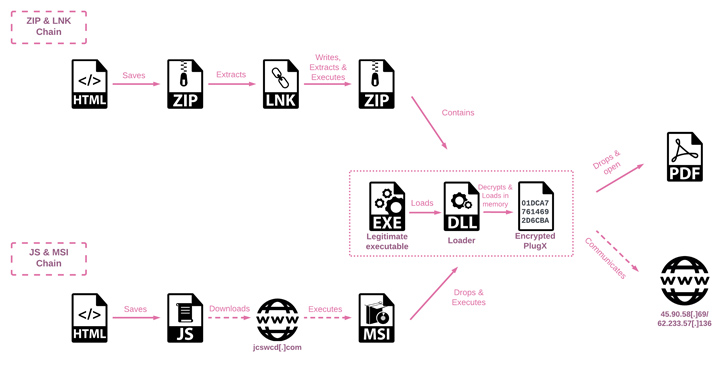
The newest assault sequence is important for the usage of HTML Smuggling – a stealthy approach wherein official HTML5 and JavaScript options are abused to assemble and launch the malware – within the decoy paperwork connected to spear-phishing emails.
“HTML smuggling employs HTML5 attributes that may work offline by storing a binary in an immutable blob of knowledge inside JavaScript code,” Trustwave famous earlier this February. “The info blob, or the embedded payload, will get decoded right into a file object when opened by way of an online browser.”
An evaluation of the paperwork, which have been uploaded to the VirusTotal malware database, reveals that they’re designed to focus on diplomats and authorities entities in Czechia, Hungary, Slovakia, the U.Ok., Ukraine, and in addition probably France and Sweden.
In a single occasion, the menace actor is claimed to have employed an Uyghur-themed lure (“China Tries to Block Distinguished Uyghur Speaker at UN.docx”) that, when opened, beacons to an exterior server by way of an embedded, invisible monitoring pixel to exfiltrate reconnaissance information.
The multi-stage an infection course of makes use of DLL side-loading strategies to decrypt and launch the ultimate payload, PlugX.
Additionally known as Korplug, the malware dates all the way in which again to 2008 and is a modular trojan able to accommodating “numerous plugins with distinct functionalities” that permits the operators to hold out file theft, display captures, keystroke logging, and command execution.
“In the course of the course of our investigating the samples, the menace actor dispatched a batch script, despatched from the C&C server, meant to erase any hint of their actions,” Verify Level mentioned.
“This script, named del_RoboTask Replace.bat, eradicates the official executable, the PlugX loader DLL, and the registry key applied for persistence, and finally deletes itself. It’s probably that is the results of the menace actors turning into conscious they have been below scrutiny.”