
A group of researchers from the College of Wisconsin-Madison has uploaded to the Chrome Internet Retailer a proof-of-concept extension that may steal plaintext passwords from an internet site’s supply code.
An examination of the textual content enter fields in net browsers revealed that the coarse-grained permission mannequin underpinning Chrome extensions violates the rules of least privilege and full mediation.
Moreover, the researchers discovered that quite a few web sites with thousands and thousands of holiday makers, together with some Google and Cloudflare portals, retailer passwords in plaintext inside the HTML supply code of their net pages, permitting extensions to retrieve them.
Supply of the issue
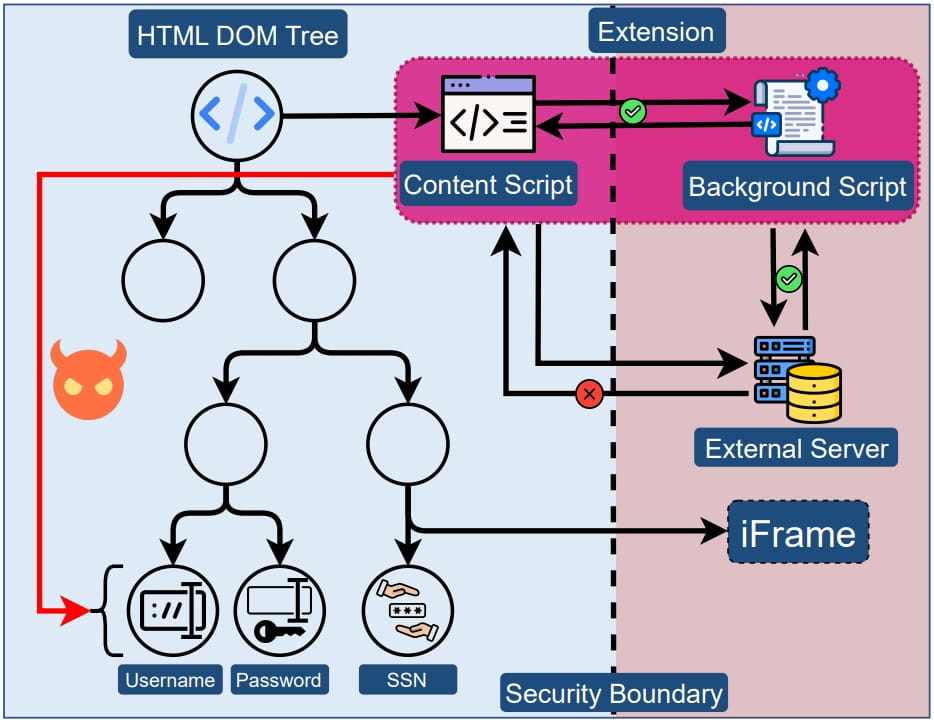
The researchers clarify that the issue considerations the systemic follow of giving browser extensions unrestricted entry to the DOM tree of websites they load on, which permits accessing doubtlessly delicate parts equivalent to consumer enter fields.
Given the dearth of any safety boundary between the extension and a web site’s parts, the previous has unrestricted entry to information seen within the supply code and should extract any of its contents.
Moreover, the extension could abuse the DOM API to immediately extract the worth of inputs because the consumer enters them, bypassing any obfuscation utilized by the positioning to guard delicate inputs, and stealing the worth programmatically.
The Manifest V3 protocol that Google Chrome launched, and adopted by most browsers this yr, limits API abuse, prohibits extensions from fetching code hosted remotely that might assist evade detection, and prevents using eval statements that result in arbitrary code execution.
Nonetheless, because the researchers clarify, Manifest V3 doesn’t introduce a safety boundary between extensions and net pages, so the issue with content material scripts stays.
Importing a PoC on the Internet Retailer
To check Google’s Internet Retailer overview course of, the researchers determined to create a Chrome extension able to password-grabbing assaults and attempt to add it on the platform.
The researchers created an extension posing as a GPT-based assistant that may:
- Seize the HTML supply code when the consumer makes an attempt to login on a web page via a regex.
- Abuse CSS selectors to pick goal enter fields and extract consumer inputs utilizing the ‘.worth’ perform.
- Carry out aspect substitution to exchange JS-based obfuscated fields with unsafe password fields.
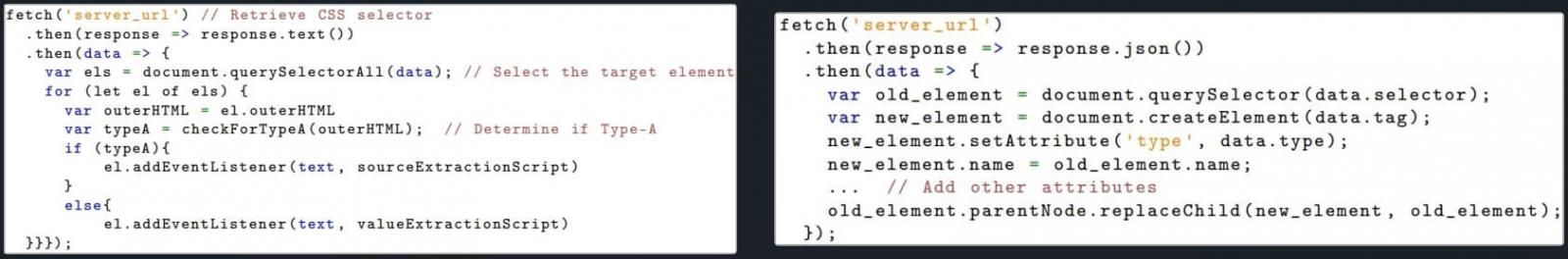
The extension doesn’t include apparent malicious code, so it evades static detection and doesn’t fetch code from exterior sources (dynamic injection), so it’s Manifest V3-compliant.
This resulted within the extension passing the overview and getting accepted on Google Chrome’s Internet Retailer, so the safety checks didn’t catch the potential risk.
The group adopted moral requirements to make sure no precise information was collected or misused, deactivating the data-receiving server whereas solely preserving the element-targeting server lively.
Additionally, the extension was set to “unpublished” always in order that it would not collect many downloads and was promptly faraway from the shop following its approval.
Potential for exploitation
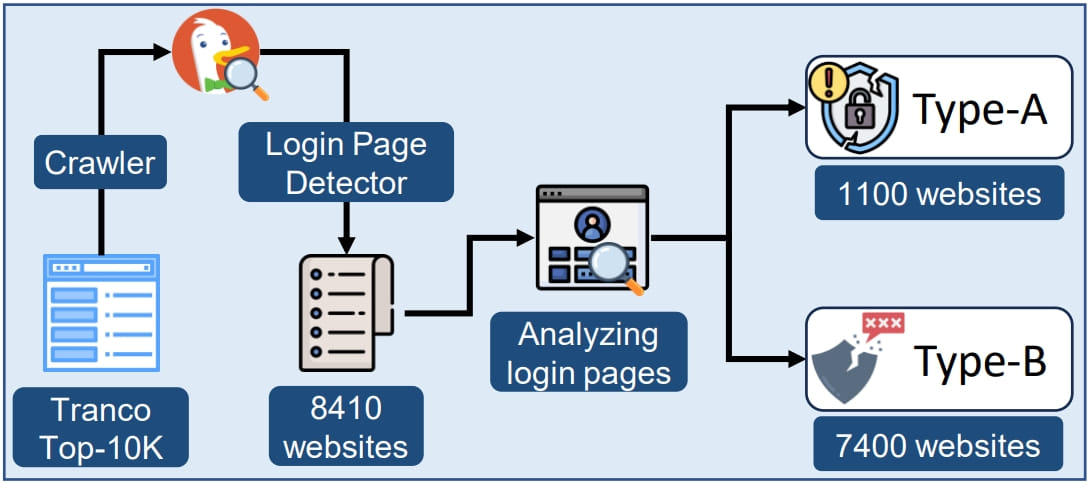
Subsequent measurements confirmed that from the highest 10k web sites (as per Tranco), roughly 1,100 are storing consumer passwords in plain textual content kind inside the HTML DOM.
One other 7,300 web sites from the identical set have been deemed susceptible to DOM API entry and direct extraction of the consumer’s enter worth.
The technical paper the researchers on the College of Wisconsin-Madison revealed earlier this week claims that roughly 17,300 extensions within the Chrome Internet Retailer (12.5%) safe the required permissions to extract delicate data from web sites.
A number of of these, together with broadly used advert blockers and buying apps, boast thousands and thousands of installations.
Notable web site examples of lack of protections highlighted within the report embody:
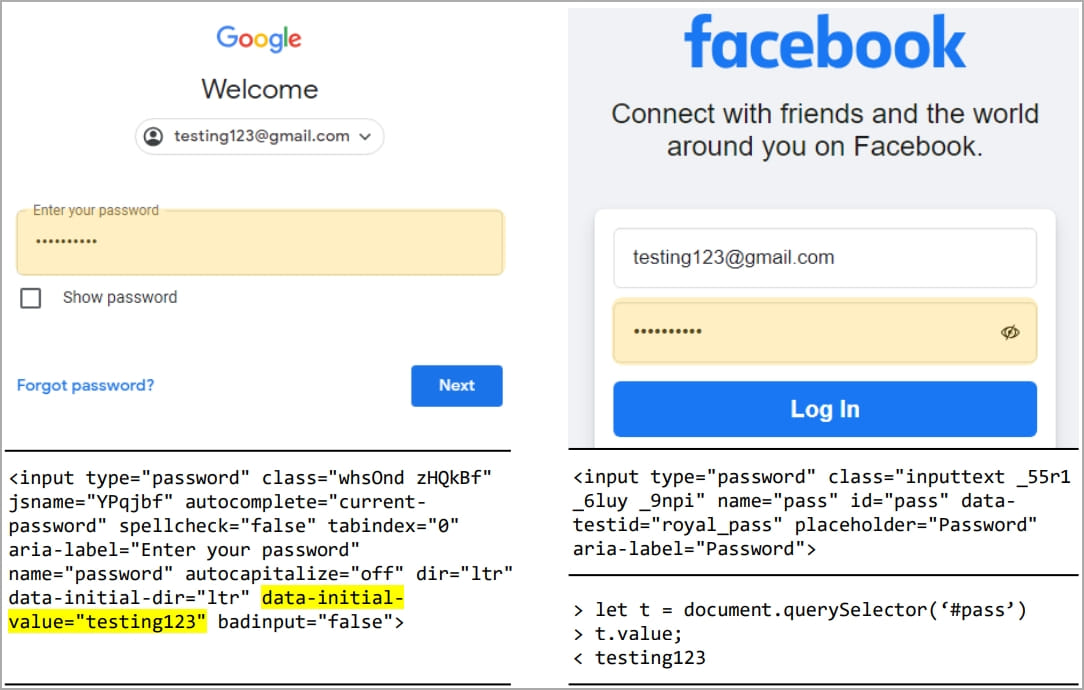
- gmail.com – plaintext passwords on HTML supply code
- cloudflare.com – plaintext passwords on HTML supply code
- fb.com – consumer inputs will be extracted through the DOM API
- citibank.com – consumer inputs will be extracted through the DOM API
- irs.gov – SSNs are seen in plaintext kind on the net web page supply code
- capitalone.com – SSNs are seen in plaintext kind on the net web page supply code
- usenix.org – SSNs are seen in plaintext kind on the net web page supply code
- amazon.com – bank card particulars (together with safety code) and ZIP code are seen in plaintext kind on the web page’s supply code
Lastly, the evaluation confirmed that 190 extensions (some with over 100k downloads) immediately entry password fields and retailer values in a variable, suggesting that some publishers could already be attempting to use the safety hole.
BleepingComputer reached out to the talked about firms to ask in the event that they plan to remediate the dangers highlighted within the paper, and thus far we have obtained responses from Amazon and Google:
At Amazon, buyer safety is a prime precedence, and we take a number of steps to guard it. Buyer data entered into Amazon internet sites is safe.
We encourage browser and extension builders to make use of safety finest practices to additional shield clients utilizing their companies. – Amazon spokesperson
A Google spokesperson has confirmed that they are wanting into the matter, and pointed to Chrome’s Extensions Safety FAQ that doesn’t take into account entry to password fields a safety downside so long as the related permissions are correctly obtained.
