
CISA is warning {that a} important Citrix ShareFile safe file switch vulnerability tracked as CVE-2023-24489 is being focused by unknown actors and has added the flaw to its catalog of recognized safety flaws exploited within the wild.
Citrix ShareFile (often known as Citrix Content material Collaboration) is a managed file switch SaaS cloud storage resolution that permits prospects and workers to add and obtain information securely.
The service additionally presents a ‘Storage zones controller’ resolution that permits enterprise prospects to configure their non-public information storage to host information, whether or not on-premise or at supported cloud platforms, similar to Amazon S3 and Home windows Azure.
On June thirteenth, 2023, Citrix launched a safety advisory on a brand new ShareFile storage zones vulnerability tracked as CVE-2023-24489 with a important severity rating of 9.8/10, which may permit unauthenticated attackers to compromise customer-managed storage zones.
“A vulnerability has been found within the customer-managed ShareFile storage zones controller which, if exploited, may permit an unauthenticated attacker to remotely compromise the customer-managed ShareFile storage zones controller,” Citrix explains.
Cybersecurity agency AssetNote disclosed the vulnerability to Citrix, warning in a technical writeup that the flaw is attributable to a number of small errors in ShareFile’s implementation of AES encryption.
“By means of our analysis we had been capable of obtain unauthenticated arbitrary file add and full distant code execution by exploiting a seemingly innocuous cryptographic bug,” AssetNote researchers clarify.
Utilizing this flaw, a risk actor may add an internet shell to a tool to achieve full entry to the storage and all its information.
CISA warns that risk actors generally exploit these kind of flaws and pose a major threat to federal enterprises.
Whereas CISA shares this similar warning on many advisories, flaws impacting managed file switch (MFT) options are of explicit concern, as risk actors have closely exploited them to steal information from corporations in extortion assaults.
One ransomware operation, often called Clop, has taken a selected curiosity in focusing on these kind of flaws, utilizing them in widescale information theft assaults since 2021, once they exploited a zero-day flaw within the Accellion FTA resolution.
Since then, Clop has performed quite a few data-theft campaigns utilizing zero-day flaws in SolarWinds Serv-U, GoAnywhere MFT, and, most just lately, the large assaults on MOVEit Switch servers.
Lively exploitation
As a part of AssetNote’s technical writeup, the researchers shared sufficient data for risk actors to develop exploits for the Citrix ShareFile CVE-2023-24489 flaw. Quickly after, different researchers launched their very own exploits on GitHub.
On July twenty sixth, GreyNoise started monitoring for makes an attempt to take advantage of the vulnerability. After CISA warned concerning the flaw at this time, GreyNoise up to date its report back to say there had been a major uptick in makes an attempt by completely different IP addresses.
“GreyNoise noticed a major spike in attacker exercise the day CISA added CVE-2023-24489 to their Identified Exploited Vulnerabilities Catalog,” warns GreyNoise.
Presently, GreyNoise has seen makes an attempt to take advantage of or test if a ShareFile server is susceptible from 72 IP addresses, with the bulk from South Korea and others in Finland, the UK, and the US.
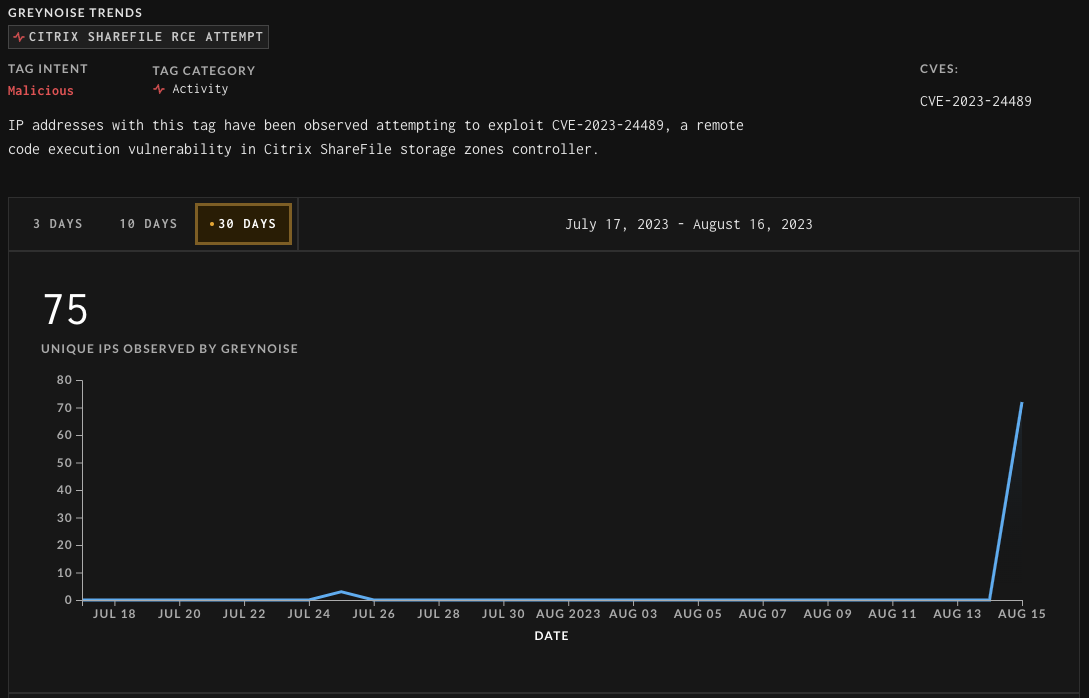
Supply: GreyNoise
Whereas no publicly recognized exploitation or information theft has been linked to this flaw, CISA now requires Federal Civilian Government Department (FCEB) businesses to use patches for this bug by September sixth, 2023.
Nonetheless, as a result of extremely focused nature of those bugs, it could be strongly suggested that every one organizations apply the updates as quickly as attainable.
