
Menace actors have breached the community of a U.S. group within the crucial infrastructure sector after exploiting a zero-day RCE vulnerability presently recognized as CVE-2023-3519, a critical-severity problem in NetScaler ADC and Gateway that Citrix patched this week.
The Cybersecurity and Infrastructure Safety Company (CISA) says that the assault occurred in June and hackers used their entry to steal Lively Listing knowledge.
Hackers exfiltrated AD knowledge
In an advisory this week, CISA warns that hackers leveraged the unauthenticated distant code execution (RCE) flaw to plant a webshell on the goal’s non-production NetScaler Utility Supply Controller (ADC) equipment.
The backdoor enabled the attacker to find energetic listing (AD) objects, which embody customers, teams, functions, and units on the community, in addition to steal AD knowledge.
As a result of the focused NetScaler ADC equipment was in a segregated setting on the community, the hackers weren’t capable of transfer laterally to a website controller, CISA says.
CISA has launched an advisory with ways, methods, and procedures (TTPs) together with detection strategies to assist organizations, significantly these within the crucial infrastructure phase, decide if their methods have been compromised.
Throughout the preliminary exploit stage, the hackers uploaded to the weak equipment a TGZ archive with a generic webshell, a discovery script, and a setuid binary.
They did SMB scanning on the subnet and used the webshell to test and exfiltrate Lively Listing stock, with a selected curiosity in:
- NetScaler configuration recordsdata that include an encrypted password whose secret’s on the ADC equipment
- NetScaler decryption keys, which might unlock the AD password within the configuration file
- The listing of customers, methods, teams, subnets, organizational items, contacts, partitions, and trusts within the Lively Listing
The attacker encrypted the invention knowledge utilizing the OpenSSL library and readied it for exfiltration to a web-accessible location in compressed type as a tarball disguised as a PNG picture.
It seems that the hackers tried to cowl their tracks by deleting the authorization file, which might forestall admins from logging in remotely. To regain entry, a reboot into single-user mode is important, which can have deleted artifacts.
With risk actors exploiting the vulnerability because it was a zero-day, NetScaler admins ought to set up directly the most recent updates Citrix launched to deal with the difficulty.
Hundreds of weak servers uncovered
An preliminary evaluation from The Shadowserver Basis, a non-profit group for making the web safer, noticed that CVE-2023-3519 was possible affecting greater than 11,000 NetScaler ADC and Gateway servers uncovered on-line.
That quantity elevated to fifteen,000, the group advised BleepingComputer at this time, after refining their question to tag as weak all NetScaler home equipment that returned a “final modified” header with a date earlier than July 1st.
The brand new depend can be resulting from enhancing the detection protection for NetScaler AAA (authentication digital server) machines. Though elevated, the quantity possible represents a conservative estimate, the group says.
CISA has additionally launched a set of instructions that organizations can use to test for indicators of compromise by exploiting CVE-2023-3519.
Command stacking resulting in root
Citrix patched CVE-2023-3519 on July 18 together with two much less extreme vulnerabilities. One is a mirrored cross-site scripting (XSS) bug with an 8.3 severity rating and tracked as CVE-2023-3466.
Exploiting this flaw is feasible if the sufferer on the identical community because the weak equipment masses within the browser a malicious hyperlink from an attacker.
The opposite is a privilege escalation to root recognized as CVE-2023-3467. It acquired an 8.0 severity rating and it may be leveraged by an attacker with the least privileged position to the NetScaler command-line interface (CLI).
Jorren Geurts and Wouter Rijkborst, researchers at cybersecurity firm Resillion, revealed a detailed technical evaluation of the vulnerability, explaining how stacking particular instructions within the NetScaler CLI permits any consumer with read-only permissions to acquire root privileges on the system.
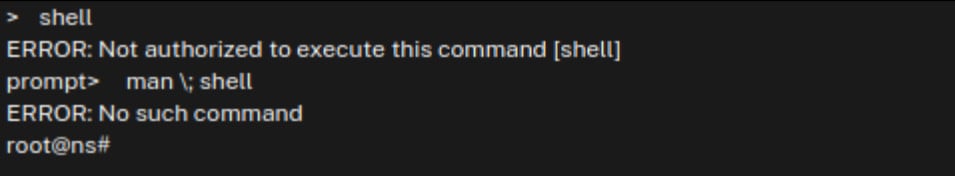
supply: Resillion
The researchers advised BleepingComputer that low-privileged consumer may additionally get root permission on the equipment utilizing the identical instructions within the net administration interface. Nevertheless, Rijkborst stated that this methodology is much less steady.
There may be presently no details about these much less extreme vulnerabilities being exploited within the wild however risk actors that have already got entry to the community may leverage them to extend their entry on the community.
Just lately, The Estée Lauder Corporations obtained breached twice in separate assaults from Clop, via the MOVEit zero-day vulnerability, and ALPHV/BlackCat ransomware gangs.
It stays unclear how ALPH/BlackCat obtained preliminary entry however the gang bragged that two weeks after the corporate engaged Microsoft DART and Mandiant companies to cope with the primary incident, they have been nonetheless on the community.
Menace actors, particularly superior teams, don’t all the time rush to maneuver laterally on the sufferer community and typically they wait silently to discover a methodology that’s much less noisy and will increase the success of the assault.
