The Web was all about grey backgrounds and uninteresting textual content containers within the ’90s. However JavaScript modified all of that, permitting us to take pleasure in dynamic textual content, interactive web sites, and clickable parts with out sacrificing efficiency. JavaScript is likely one of the mostly used programming languages as we speak.
Nevertheless, attackers are exploiting vulnerabilities in JavaScript purposes with malicious scripts and session hijacking assaults to create a variety of manipulations — corresponding to session redirects, delicate knowledge harvesting (compliance breaches), and knowledge tampering. Many ransomware variants exploit loopholes in JavaScript code, corresponding to Magniber, Vjw0rm, and GootLoader. The MageCart group compromised British Airways, utilizing simply 22 traces of code to control the Modernizr library.
So how do you make JavaScript safer? There are dozens of how adversaries exploit JS vulnerabilities, together with difficult-to-counter assaults like cross-site scripting (XSS), session hijacking, OS command injection, common expression (Regex) exploits, and unfold operator injection. Nicely-established safety habits can thwart a few of these assaults. Let’s take a better have a look at some assault methods and the very best cybersecurity practices to mitigate them.
Widespread Assaults and Learn how to Defend Towards Them
SQL injections (SQLi). SQL injection assaults goal vulnerabilities corresponding to encoding procedures and improper validation to execute malicious database instructions.
To attenuate the dangers: Validate all inputs. Transfer away from utilizing specific SQL queries in code in favor of utilizing object-relational mapping (ORMs). There are a lot of nice choices, however I like TYPEORM.
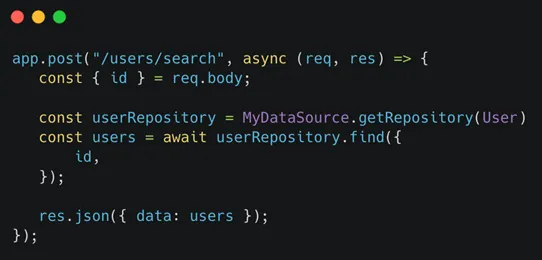
Cross-site scripting (XSS). Attackers exploit vulnerabilities corresponding to lack of validation or encoding within the internet purposes to insert malicious code. The contaminated software sends the code to the consumer as a browser-side script, which then offers attackers entry to session tokens, cookies, passwords, and different kinds of private info. There are several types of XSS assaults in use as we speak — Mirrored (Non-Persistent) XSS, Saved XSS, and DOM Primarily based XSS being the most typical variations.
To attenuate the dangers: Don’t simply belief content material handed from customers and run it; filter it upon arrival. Be sure that the content material your server returns applies the matching content-type headers to make sure that browsers interpret the responses in the way in which you plan. Apply a content material safety coverage at any time when and wherever you’ll be able to to manage which content material runs in your web site and which origins you belief with this content material.
Cross-site request forgery (CSRF). CSRF assaults are extraordinarily frequent as we speak. These exploits trick finish customers into performing and executing malicious actions whereas they’re utilizing Net purposes. This occurs after they’ve already been authenticated and utilization has began. The principle method used right here is social engineering, normally malicious emails or SMS messages with normal-looking hyperlinks. As soon as the hyperlink is clicked, the payload is executed.
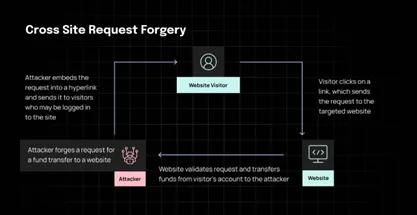
To attenuate the dangers: Use frameworks that include built-in CSRF safety. You may also implement CSRF tokens to all requests that trigger actions (state altering) and validate them in your backend.
Path traversal assaults. Often known as listing traversal assaults, path traversal assaults are used to realize unauthorized entry to directories, configuration information, and delicate passwords which were saved (fairly carelessly) outdoors the net root folder.
To attenuate the dangers: Keep away from storing delicate information outdoors your internet root folder. Work with out consumer enter when utilizing file system calls. Additionally, guarantee that the consumer cannot provide all components of the trail by surrounding consumer enter with your individual path code. Lastly, implement robust code entry insurance policies (with chrooted jails) to limit the place the information could be obtained or saved to.
Server-side request forgery (SSRF). SSRF assaults exploit server-side vulnerabilities to carry out a variety of unauthorized actions — accessing delicate assets (AWS metadata), connecting to inner companies, manipulating knowledge, and even modifying URLs to entry knowledge from safe distributors or channel buyer info to distant servers. Apart from utilizing HTTP protocols, SSRF assaults may also use FTP, SMTP, and SMB.
To attenuate the dangers: Validate knowledge and contexts. Search for V4 and V6 addresses. Cross-check offered IP addresses with the trusted vendor IP addresses. Do not save knowledge on servers — go along with S3 buckets and blobs as an alternative. Construct a case-sensitive whitelist of trusted and recognized domains. And by no means settle for full URLs from customers — they’re powerful to validate.
Delicate cookie publicity. There are a lot of variations of delicate knowledge publicity vulnerabilities, however there is a frequent theme in all of them: the publicity of data that ought to have been encrypted. The hackers additionally like to take advantage of weak cryptographic keys (for instance, the MD5 password hashing algorithm that is now not thought of safe) with brute pressure assaults which are powered by highly effective ASICs and GPUs.
To attenuate the dangers: Classify all saved, processed, and transmitted knowledge as per your regulatory necessities and apply controls accordingly. Discard unrequired delicate knowledge. Encrypt all knowledge at relaxation and knowledge in transit with TLS protocol, together with PFS ciphers and different safe parameters. Use HSTS. Disable all caching for responses that comprise delicate info.
In Abstract: Finest Practices
JavaScript is a real blessing due to its versatility and adaptability. It helps companies create highly effective consumer experiences and obtain enhanced performance. However it additionally presents safety necessities you should contemplate. Solely a proactive method may also help you avoid hassle — downtime, remediation prices, model injury, misplaced enterprise — and keep compliant with privateness rules.
Listed below are some greatest practices you need to have in place:
- Keep away from the eval() command in your code as a result of it merely can execute a handed argument identical to any common JS expression.
- Prioritize encryption protocols, and likewise set all your cookies as “safe” to restrict their use and stop hackers from exploiting them.
- Make a behavior of setting API entry keys. When you begin assigning particular person tokens for finish customers, unlawful entry can routinely be denied.
- innerHTML is a really highly effective DOM manipulation technique, which does not restrict or escape the values handed to them. Use innerText as an alternative.
It is also a good suggestion to code securely and have a supply code evaluation (SCA) resolution on board to detect vulnerabilities as early as doable. Site visitors also needs to undergo a confirmed and examined internet software firewall (WAF). Whereas neither of the 2 are silver bullets with regards to JavaScript safety — cyber immunity generally is a fable — you might be all the time safer with a number of protect layers.

