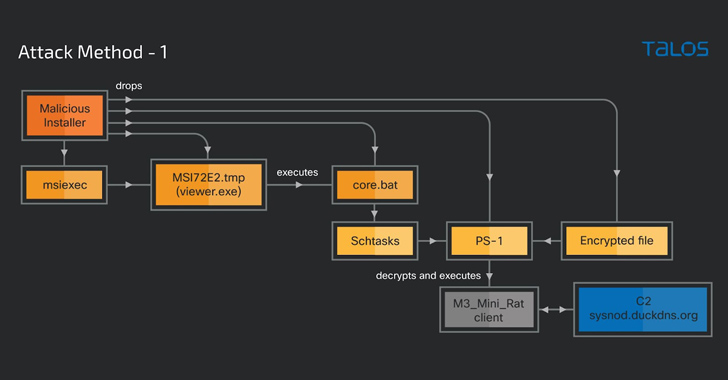
A reputable Home windows instrument used for creating software program packages known as Superior Installer is being abused by menace actors to drop cryptocurrency-mining malware on contaminated machines since no less than November 2021.
“The attacker makes use of Superior Installer to package deal different reputable software program installers, corresponding to Adobe Illustrator, Autodesk 3ds Max, and SketchUp Professional, with malicious scripts and makes use of Superior Installer’s Customized Actions characteristic to make the software program installers execute the malicious scripts,” Cisco Talos researcher Chetan Raghuprasad mentioned in a technical report.
The character of the purposes trojanized signifies that the victims doubtless span structure, engineering, development, manufacturing, and leisure sectors. The software program installers predominantly use the French language, an indication that French-speaking customers are being singled out.
This marketing campaign is strategic in that these industries depend on computer systems with excessive Graphics Processing Unit (GPU) energy for his or her day-to-day operations, making them profitable targets for cryptojacking.

Cisco’s evaluation of the DNS request knowledge despatched to the attacker’s infrastructure exhibits that the victimology footprint spans France and Switzerland, adopted by sporadic infections within the U.S., Canada, Algeria, Sweden, Germany, Tunisia, Madagascar, Singapore, and Vietnam.
The assaults culminate within the deployment of an M3_Mini_Rat, a PowerShell script that doubtless acts as a backdoor to obtain and execute further threats, in addition to a number of cryptocurrency-mining malware households corresponding to PhoenixMiner and lolMiner.
As for the preliminary entry vector, it is suspected that search engine marketing (search engine marketing) poisoning methods could have been employed to ship the rigged software program installers to the sufferer’s machines.
The installer, as soon as launched, prompts a multi-stage assault chain that drops the M3_Mini_Rat shopper stub and the miner binaries.
“M3_Mini_Rat shopper is a PowerShell script with distant administration capabilities that primarily focuses on performing system reconnaissance and downloading and executing different malicious binaries,” Raghuprasad mentioned.
The trojan is designed to contact a distant server, though it is presently unresponsive, making it tough to find out the precise nature of malware that will have been distributed by means of this course of.
Approach Too Susceptible: Uncovering the State of the Identification Assault Floor
Achieved MFA? PAM? Service account safety? Learn how well-equipped your group really is in opposition to id threats
The 2 different malicious payloads are used to illicitly mine cryptocurrency utilizing the machine’s GPU sources. PhoenixMiner is an Ethereum cryptocurrency-mining malware, whereas lolMiner is an open-source mining software program that can be utilized to mine two digital currencies on the similar time.
In yet one more case of reputable instrument abuse, Test Level is warning of a brand new kind of phishing assault that leverages Google Looker Studio to create bogus cryptocurrency phishing websites in an try to sidestep protections.
“Hackers are using it to create faux crypto pages which can be designed to steal cash and credentials,” safety researcher Jeremy Fuchs mentioned.
“This can be a great distance of claiming that hackers are leveraging Google’s authority. An e mail safety service will take a look at all these elements and have a great deal of confidence that it isn’t a phishing e mail, and that it comes from Google.”