
Proof-of-concept exploit code has been launched for a crucial SSH authentication bypass vulnerability in VMware’s Aria Operations for Networks evaluation software (previously often called vRealize Community Perception).
The flaw (tracked as CVE-2023-34039) was discovered by safety analysts at ProjectDiscovery Analysis and patched by VMware on Wednesday with the discharge of model 6.11.
Profitable exploitation allows distant attackers to bypass SSH authentication on unpatched home equipment and entry the software’s command line interface in low-complexity assaults that do not require person interplay due to what the corporate describes as “a scarcity of distinctive cryptographic key technology.”
To mitigate the flaw, VMware “extremely recommends” making use of safety patches for Aria Operations for Networks variations 6.2 / 6.3 / 6.4 / 6.5.1 / 6.6 / 6.7 / 6.8 / 6.9 / 6.10 out there on this help doc.
At this time, VMware confirmed that CVE-2023-34039 exploit code has been revealed on-line, two days after disclosing the crucial safety bug.
The proof-of-concept (PoC) exploit targets all Aria Operations for Networks variations from 6.0 to six.10, and it was developed and launched by Summoning Workforce vulnerability researcher Sina Kheirkhah.
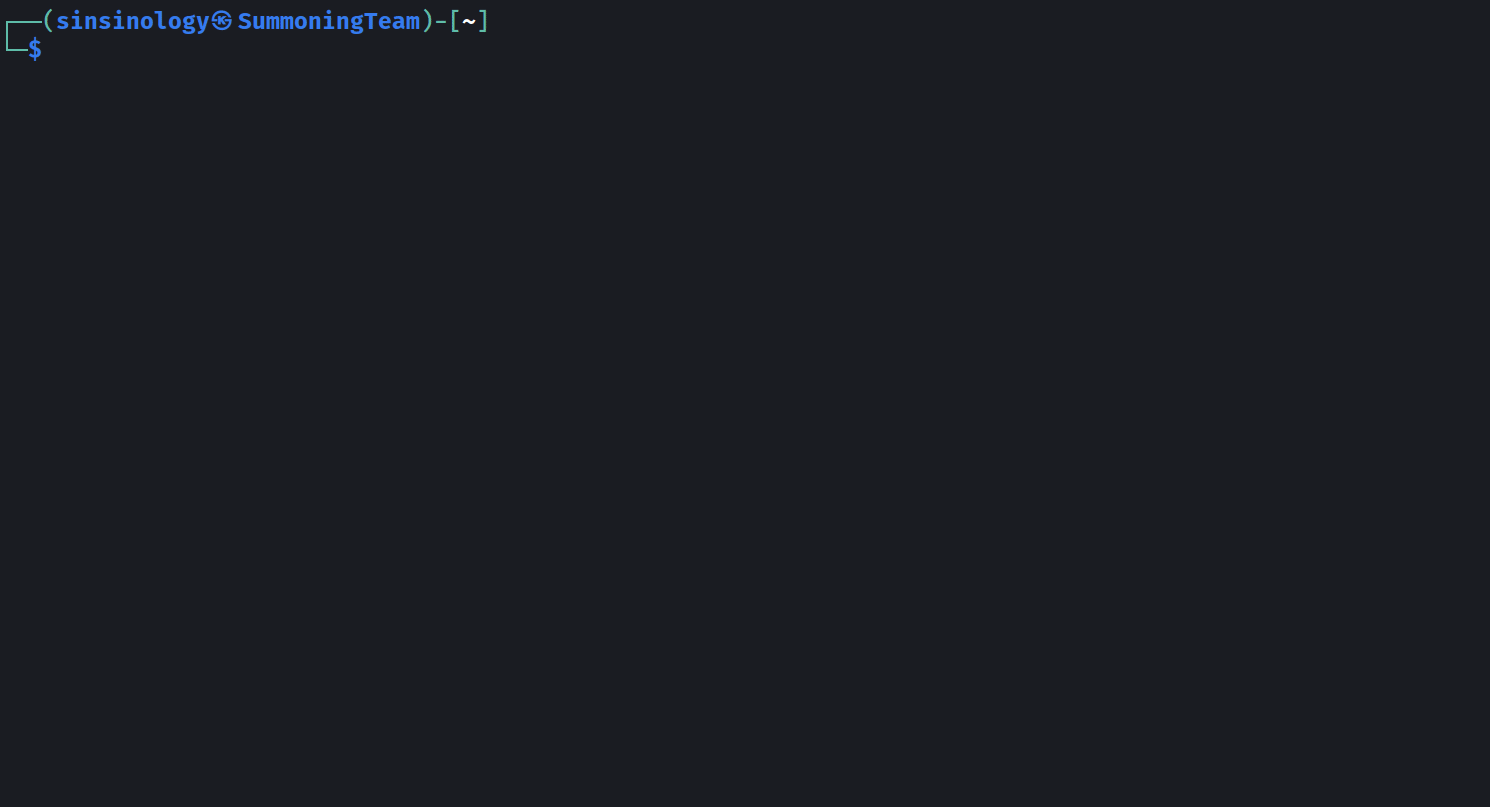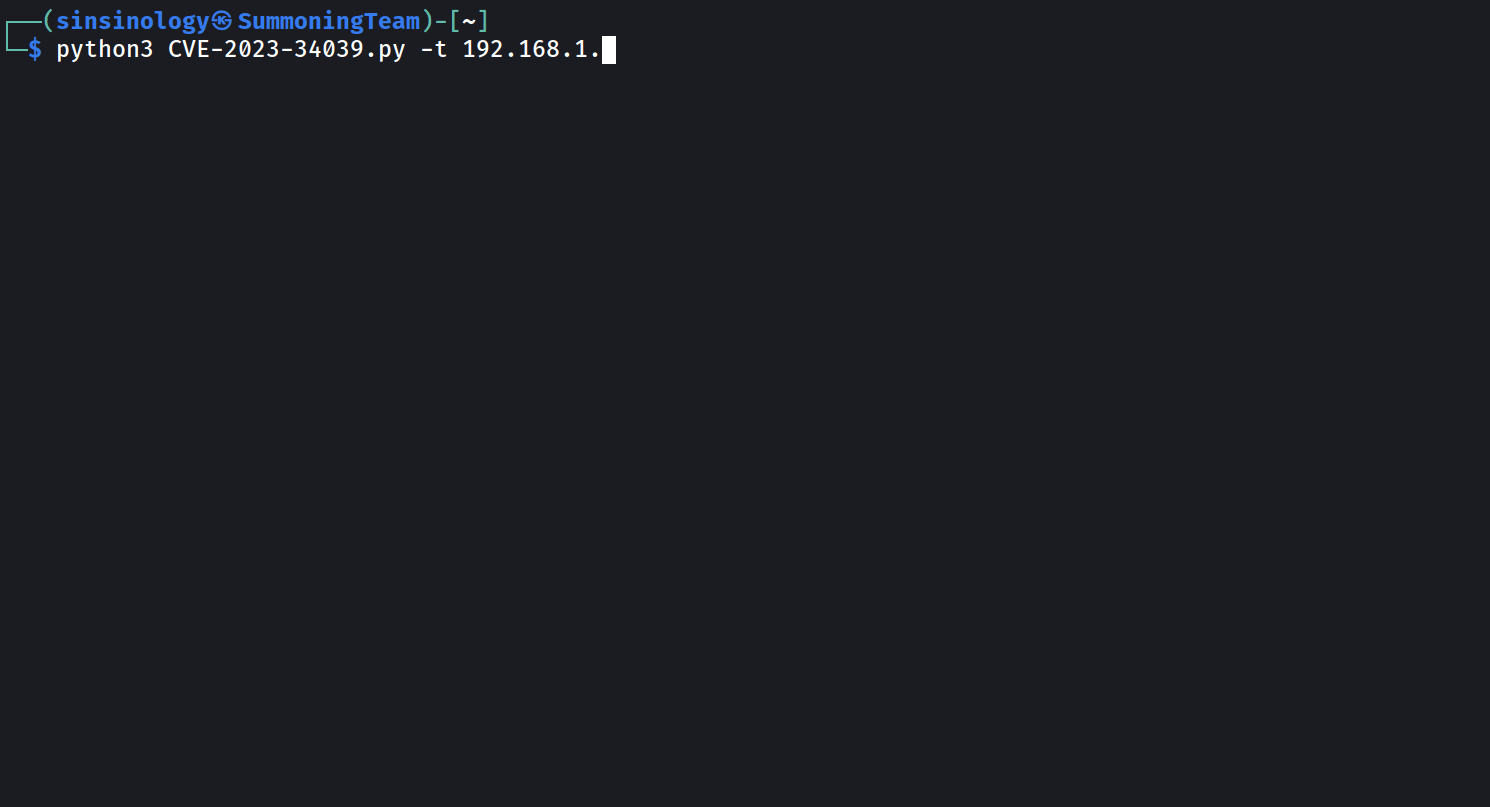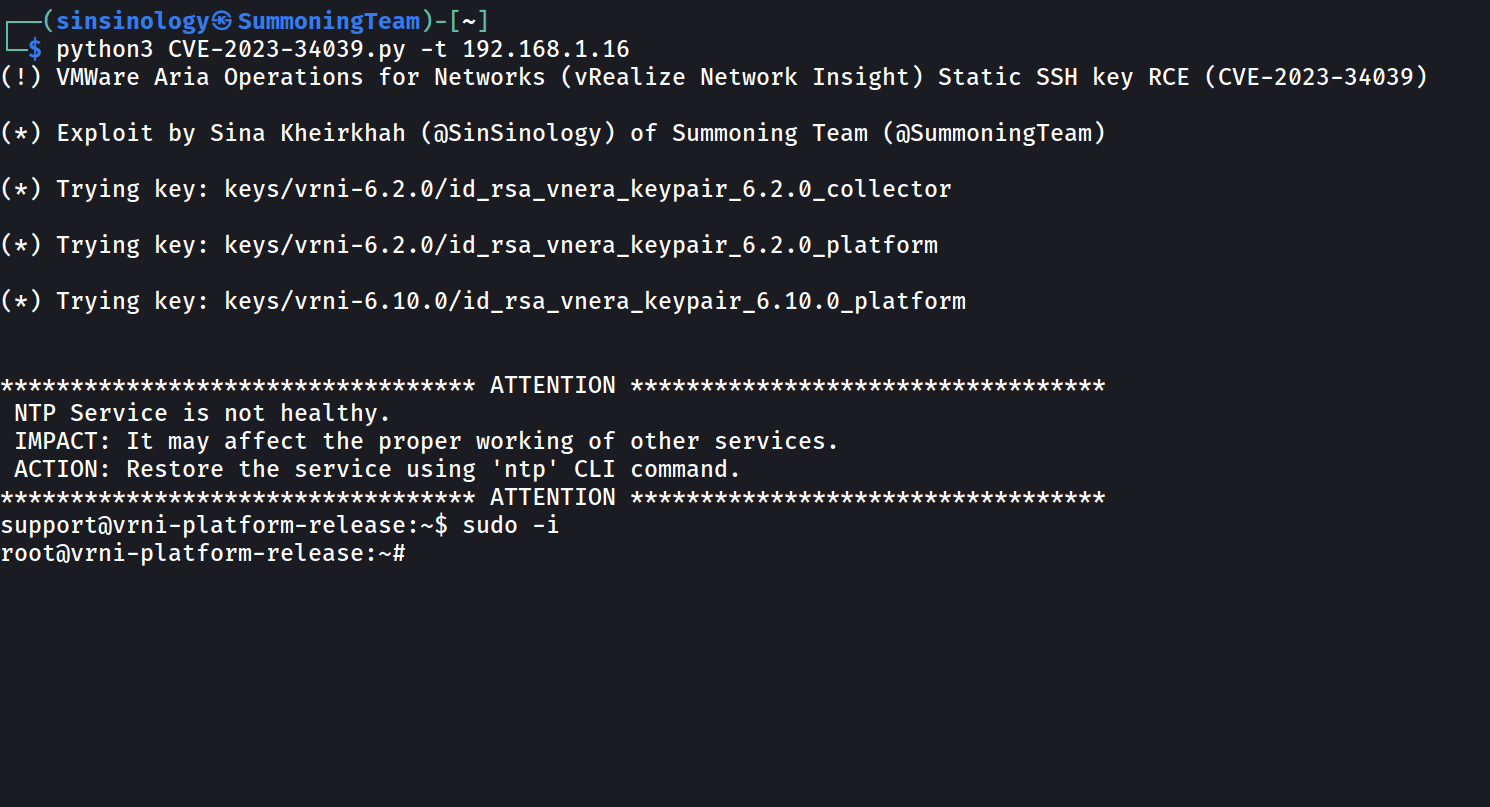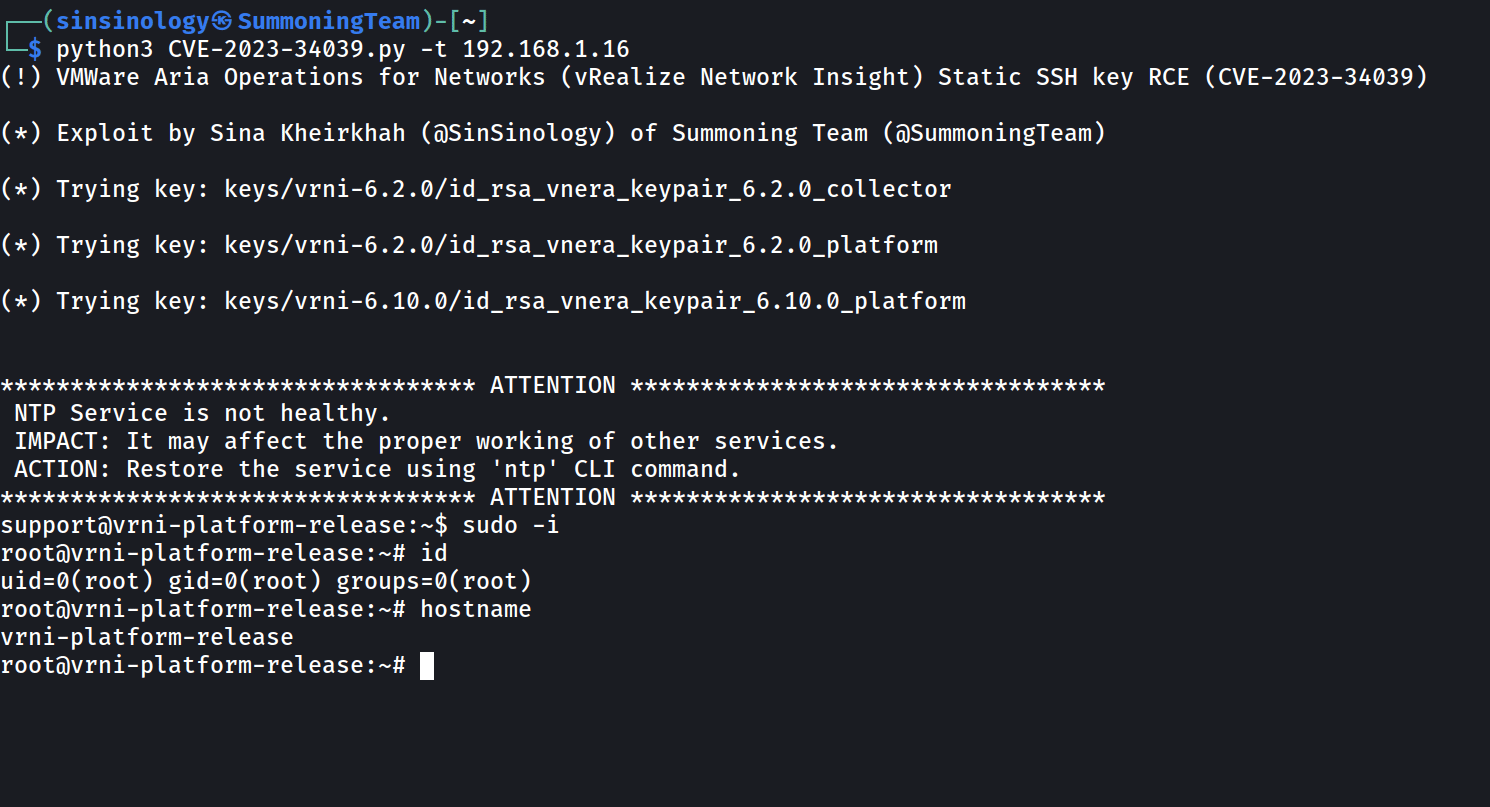
Kheirkhah stated that the basis reason behind the difficulty are hardcoded SSH keys left after VMware forgot to regenerate SSH approved keys.
“Every model of VMware’s Aria Operations for Networks has a singular SSH key. To create a totally useful exploit, I needed to gather all of the keys from completely different variations of this product,” Kheirkhah stated.
VMware additionally patched an arbitrary file write vulnerability this week (CVE-2023-20890), which permits attackers to realize distant code execution after acquiring admin entry to the focused equipment (the CVE-2023-34039 PoC may allow them to get root permissions following profitable assaults).
In July, VMware warned clients that exploit code was launched on-line for a crucial RCE flaw (CVE-2023-20864) within the VMware Aria Operations for Logs evaluation software, patched in April.
One month earlier, the corporate issued one other alert relating to the lively exploitation of one other Community Perception crucial bug (CVE-2023-20887) that may result in distant command execution assaults.
CISA ordered U.S. federal companies to patch their programs towards CVE-2023-20887 by July thirteenth after including it to its listing of identified exploited vulnerabilities.
In mild of this, admins are strongly advisable to replace their Aria Operations for Networks home equipment to the most recent model as quickly as attainable as a preemptive measure towards potential incoming assaults.
Whereas the variety of VMware vRealize cases uncovered on-line is comparatively low, it aligns with the meant use of those home equipment on inside networks.
