The U.S. Authorities Nationwide Vulnerability Database (NVD) revealed discover of a crucial vulnerability affecting the Forminator WordPress Contact Kind plugin as much as an together with model 1.24.6.
Unauthenticated attackers can add malicious information to web sites which, in accordance with the warning, “might make distant code execution potential.”
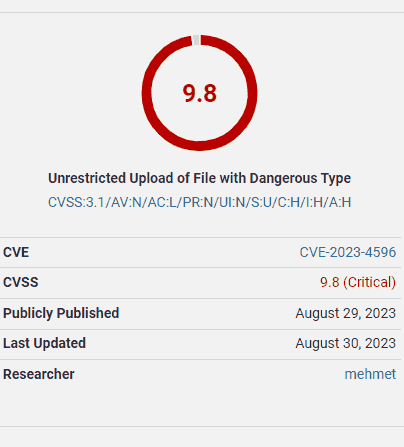
The vulnerability rating score is 9.8, on a scale of 1 to 10, with ten being probably the most extreme vulnerability stage.
Screenshot Of Wordfence Advisory
 Screenshot from Wordfence.com
Screenshot from Wordfence.comVulnerability To Unauthenticated Attackers
Many vulnerabilities are likely to require an attacker to first attain a WordPress person stage earlier than they’ll launch an assault.
For instance, some vulnerabilities can be found to these with a subscriber person stage, others require contributor or admin stage with a purpose to carry out an assault.
What makes this vulnerability significantly worrisome is that it permits unauthenticated attackers, these with no person stage in any respect, to efficiently hack the location.
A second cause why this vulnerability is rated 9.8 on a scale of 1 – 10 (crucial) is that the attacker can add an arbitrary file, which implies any type of file, like a malicious script.
The Nationwide Vulnerability Database (NVD) describes the vulnerability:
“The Forminator plugin for WordPress is weak to arbitrary file uploads attributable to file sort validation occurring after a file has been uploaded to the server within the upload_post_image() operate in variations as much as, and together with, 1.24.6.
This makes it potential for unauthenticated attackers to add arbitrary information on the affected website’s server which can make distant code execution potential.”
Distant Code Execution
A Distant Code Execution (RCE) vulnerability is a sort of exploit the place the attacker can execute malicious code on the attacked web site remotely from one other machine.
The harm from this type of exploit could be as extreme as a full website takeover.
Contact Types Should Be Locked Down
WordPress plugins that enable a registered or unauthenticated customers to add something, even textual content or photographs, will need to have a approach to restrict what could be uploaded.
Contact Types have to be particularly locked down as a result of they settle for enter from the general public.
RCE Not Particular To WordPress
These sorts of vulnerabilities should not explicit to WordPress, they’ll occur to any Content material Administration System.
WordPress publishes coding requirements for publishers to know tips on how to stop these sorts of issues.
The WordPress developer web page for plugin safety (Sanitizing Knowledge) explains tips on how to correctly deal with uploads from untrusted sources.
The developer web page advises:
“Untrusted information comes from many sources (customers, third celebration websites, even your individual database!) and all of it must be checked earlier than it’s used.
Sanitizing enter is the method of securing/cleansing/filtering enter information.
Validation is most popular over sanitization as a result of validation is extra particular.
However when “extra particular” isn’t potential, sanitization is the following smartest thing.”
Has the Forminator Contact Kind Plugin Mounted The Vulnerability?
In response to Nationwide Vulnerability Database and the Wordfence WordPress safety firm, the difficulty has been addressed in model 1.25.0.
Wordfence recommends updating to the most recent model:
“Replace to model 1.25.0, or a more moderen patched model…”
Forminator Plugin Changelog
A changelog is a file of all of the adjustments made to a software program. It permits customers to learn it and decide whether or not or not they wish to replace their software program.
It’s a superb follow to let your customers know {that a} software program replace accommodates a repair (referred to as a patch) for a vulnerability.
This lets customers know {that a} explicit replace is pressing in order that they’ll make an knowledgeable resolution about updating their software program.
In any other case, how would a software program person know that an replace is pressing with out the changelog informing them, proper?
Decide for your self whether or not the Forminator changelog provides ample notification to their customers a couple of vulnerability patch:
Screenshot of Forminator Changelog

Sources:
Learn the official Nationwide Vulnerability Database advisory:
Learn the Wordfence advisory on the Forminator WordPress Contact Kind Plugin Vulnerability
Forminator <= 1.24.6 – Unauthenticated Arbitrary File Add
Learn the Exploit Database report on the Forminator Contact Kind vulnerability
WordPress Plugin Forminator 1.24.6 – Unauthenticated Distant Command Execution
Featured picture by Shutterstock/ViDI Studio

