A obtain supervisor website served Linux customers malware that stealthily stole passwords and different delicate info for greater than three years as a part of a provide chain assault.
The modus operandi entailed establishing a reverse shell to an actor-controlled server and putting in a Bash stealer on the compromised system. The marketing campaign, which befell between 2020 and 2022, is now not energetic.
“This stealer collects information comparable to system info, looking historical past, saved passwords, cryptocurrency pockets information, in addition to credentials for cloud providers (AWS, Google Cloud, Oracle Cloud Infrastructure, Azure),” Kaspersky researchers Georgy Kucherin and Leonid Bezvershenko mentioned.
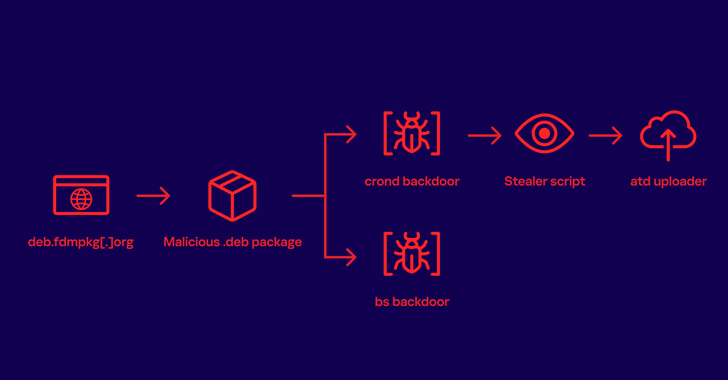
The web site in query is freedownloadmanager[.]org, which, in keeping with the Russian cybersecurity agency, gives a reliable Linux software program known as “Free Obtain Supervisor,” however beginning in January 2020, started redirecting some customers who tried to obtain it to a different area deb.fdmpkg[.]org that served a booby-trapped Debian package deal.
It is suspected that the malware authors engineered the assault based mostly on sure predefined filtering standards (say, a digital fingerprint of the system) to selectively lead potential victims to the malicious model. The rogue redirects led to 2022 for inexplicable causes.

The Debian package deal comprises a post-install script that is executed upon its set up to drop two ELF information, /var/tmp/bs and a DNS-based backdoor (/var/tmp/crond) that launches a reverse shell to a command-and-control (C2) server, which is obtained in response to a DNS request to one of many 4 domains –
- 2c9bf1811ff428ef9ec999cc7544b43950947b0f.u.fdmpkg[.]org
- c6d76b1748b67fbc21ab493281dd1c7a558e3047.u.fdmpkg[.]org
- 0727bedf5c1f85f58337798a63812aa986448473.u.fdmpkg[.]org
- c3a05f0dac05669765800471abc1fdaba15e3360.u.fdmpkg[.]org
“The communication protocol is, relying on the connection kind, both SSL or TCP,” the researchers mentioned. “Within the case of SSL, the crond backdoor launches the /var/tmp/bs executable and delegates all additional communications to it. In any other case, the reverse shell is created by the crond backdoor itself.”
The last word purpose of the assault is to deploy a stealer malware and harvest delicate information from the system. The gathering info is then uploaded to the attacker’s server utilizing an uploader binary downloaded from the C2 server.
crond, Kaspersky mentioned, is a variant of a backdoor generally known as Bew that has been in circulation since 2013, whereas an early model of the Bash stealer malware was beforehand documented by Yoroi in June 2019.
Id is the New Endpoint: Mastering SaaS Safety within the Trendy Age
Dive deep into the way forward for SaaS safety with Maor Bin, CEO of Adaptive Protect. Uncover why id is the brand new endpoint. Safe your spot now.
It isn’t instantly clear how the compromise truly befell and what the tip targets of the marketing campaign had been. What’s evident is that not everybody who downloaded the software program obtained the rogue package deal, enabling it to evade detection for years.
“Whereas the marketing campaign is at the moment inactive, this case of Free Obtain Supervisor demonstrates that it may be fairly troublesome to detect ongoing cyberattacks on Linux machines with the bare eye,” the researchers mentioned.
“Thus, it’s important that Linux machines, each desktop and server, are outfitted with dependable and environment friendly safety options.”