We’re happy to announce the supply of the 2023 AT&T Cybersecurity Insights Report: Give attention to Manufacturing. The report examines the sting ecosystem, surveying manufacturing IT leaders from world wide, and gives benchmarks for assessing your edge computing plans. That is the twelfth version of our vendor-neutral and forward-looking report. Final 12 months’s give attention to manufacturing report documented how we safe the information, functions, and endpoints that depend on edge computing (get the 2022 report).
Get the complimentary 2023 report.
The strong quantitative area survey reached 1,418 safety, IT, utility improvement, and line of enterprise professionals worldwide. The qualitative analysis tapped subject material consultants throughout the cybersecurity trade. Manufacturing-specific respondents equal 202.
On the onset of our analysis, we established the next hypotheses.
- Momentum edge computing has out there.
- Approaches to connecting and securing the sting ecosystem – together with the position of trusted advisors to realize edge objectives.
- Perceived threat and perceived advantage of the frequent use circumstances in every trade surveyed.
The outcomes give attention to frequent edge use circumstances in seven vertical industries – healthcare, retail, finance, manufacturing, vitality and utilities, transportation, and U.S. SLED and delivers actionable recommendation for securing and connecting an edge ecosystem – together with exterior trusted advisors. Lastly, it examines cybersecurity and the broader edge ecosystem of networking, service suppliers, and high use circumstances.
The position of IT is shifting, embracing stakeholders on the ideation section of improvement
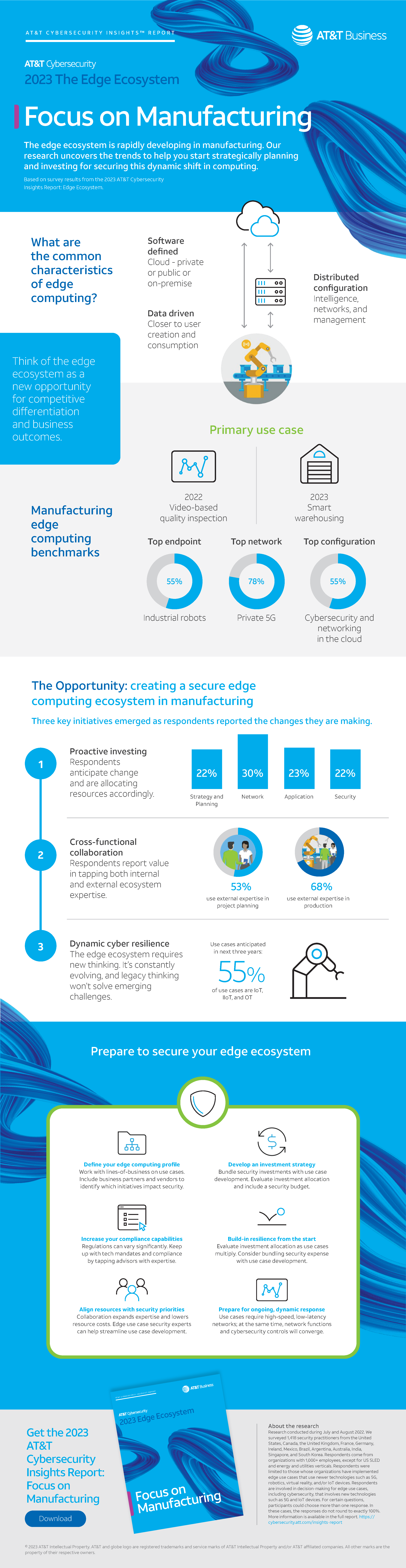
Edge computing is a transformative expertise that brings collectively numerous stakeholders and aligns their pursuits to drive built-in enterprise outcomes. The emergence of edge computing has been fueled by a technology of visionaries who grew up within the period of smartphones and limitless potentialities. Have a look at the infographic beneath for a topline abstract of key findings within the manufacturing trade.
On this paradigm, the position of IT has shifted from being the duty grasp to a collaborative companion in delivering revolutionary edge computing options. As well as, we discovered that manufacturing leaders are budgeting in a different way for edge use circumstances. These two issues, together with an expanded method to securing edge computing, had been prioritized by our respondents within the 2023 AT&T Cybersecurity Insights Report: Edge Ecosystem.
One of the crucial promising points of edge computing is its potential to successfully use near-real-time knowledge for tighter management of variable operations akin to stock and provide chain administration that ship improved operational effectivity. Including new endpoints is important for gathering the information, however how they’re related could make them weak to cyberattacks. Profitable cyberattacks can disrupt companies, highlighting the necessity for strong cybersecurity measures.
Edge computing brings the information nearer to the place selections are made
With edge computing, the intelligence required to make selections, the networks used to seize and transmit knowledge, and the use case administration are distributed. Distributed means issues work sooner as a result of nothing is backhauled to a central processing space akin to an information heart and delivers the near-real-time expertise.
With this stage of complexity, it’s frequent to re-evaluate selections concerning safety, knowledge storage, or networking. The report shares rising traits as manufacturing continues exploring edge computing use circumstances. One space that’s examined is expense allocation, and what we discovered might shock you. The analysis reveals the allocation of investments throughout general technique and planning, community, utility, and safety for the anticipated use circumstances that organizations plan to implement inside the subsequent three years.
Making ready to safe your manufacturing edge ecosystem.
Develop your edge computing profile. It’s important to interrupt down the obstacles that usually separate the interior line of enterprise groups, utility improvement groups, community groups, and safety groups. Know-how selections shouldn’t be made in isolation however reasonably by means of collaboration with line of enterprise companions. Understanding the capabilities and limitations of current enterprise and expertise companions makes it simpler to determine gaps in evolving undertaking plans.
The sting ecosystem is increasing, and experience is out there to supply options that handle value, implementation, mitigating dangers, and extra. Together with experience from the broader manufacturing edge ecosystem will increase the probabilities of excellent efficiency and alignment with organizational objectives.
Develop an funding technique. Throughout manufacturing edge use case improvement, organizations ought to fastidiously decide the place and the way a lot to take a position. Consider it as a part of monetizing the use case. Constructing safety into the use case from the beginning permits the group to contemplate safety as a part of the general value of products (COG). It is vital to notice that no one-size-fits-all resolution can present full safety for all points of edge computing. As a substitute, organizations ought to contemplate a complete and multi-layered method to deal with the distinctive safety challenges of every use case.
enhance your compliance capabilities. Rules in manufacturing can range considerably. This underscores the significance of not relying solely on a checkbox method or conducting annual opinions to assist guarantee compliance with the rising variety of rules. Maintaining with technology-related mandates and serving to to make sure compliance requires ongoing effort and experience. If navigating compliance necessities will not be inside your group’s experience, search exterior assist from professionals specializing on this space.
Align sources with rising priorities. Exterior collaboration permits organizations to make the most of experience and cut back useful resource prices. It goes past relying solely on inner groups inside the group. It entails tapping into the increasing ecosystem of edge computing consultants who supply strategic and sensible steerage. Partaking exterior subject material consultants (SMEs) to reinforce decision-making might help forestall pricey errors and speed up deployment. These exterior consultants might help optimize use case implementation, finally saving time and sources.
Construct-in resilience. Think about approaching edge computing with a layered mindset. Take the time to ideate on numerous “what-if” eventualities and anticipate potential challenges. For instance, what measures exist if a non-public 5G community experiences an outage? Can knowledge stay safe when using a public 4G community? How can business-as-usual operations proceed within the occasion of a ransomware assault?
Profitable edge computing implementations within the manufacturing trade require a holistic method encompassing collaboration, compliance, resilience, and adaptableness. By contemplating these components and proactively partaking with the experience accessible, manufacturing will proceed to unlock the potential of edge computing to ship improved operational effectivity, permitting the trade to give attention to innovation reasonably than operations.