
GitHub is now robotically blocking the leak of delicate info like API keys and entry tokens for all public code repositories.
At the moment’s announcement comes after the corporate launched push safety in beta a couple of 12 months in the past, in April 2022.
This function proactively prevents leaks by scanning for secrets and techniques earlier than ‘git push’ operations are accepted, and it works with 69 token sorts (API keys, non-public keys, secret keys, authentication tokens, entry tokens, administration certificates, credentials, and extra) detectable with a low “false constructive” detection fee.
“In case you are pushing a commit containing a secret, a push safety immediate will seem with info on the key kind, location, and tips on how to remediate the publicity,” GitHub mentioned at this time.
“Push safety solely blocks secrets and techniques with low false constructive charges, so when a commit is blocked, you already know it is price investigating.”
Since its beta launch, software program builders who enabled it efficiently averted round 17,000 unintended exposures of delicate info, saving greater than 95,000 hours that might’ve been spent revoking, rotating, and remediating compromised secrets and techniques, in response to GitHub.
Whereas earlier than at this time, this function might solely be enabled for personal repositories by organizations with a GitHub Superior Safety license, GitHub has now additionally made it typically accessible on all public repos.
“At the moment, push safety is usually accessible for personal repositories with a GitHub Superior Safety (GHAS) license,” the corporate mentioned.
“As well as, to assist builders and maintainers throughout open supply proactively safe their code, GitHub is making push safety free for all public repositories.”
allow secret scanning push safety
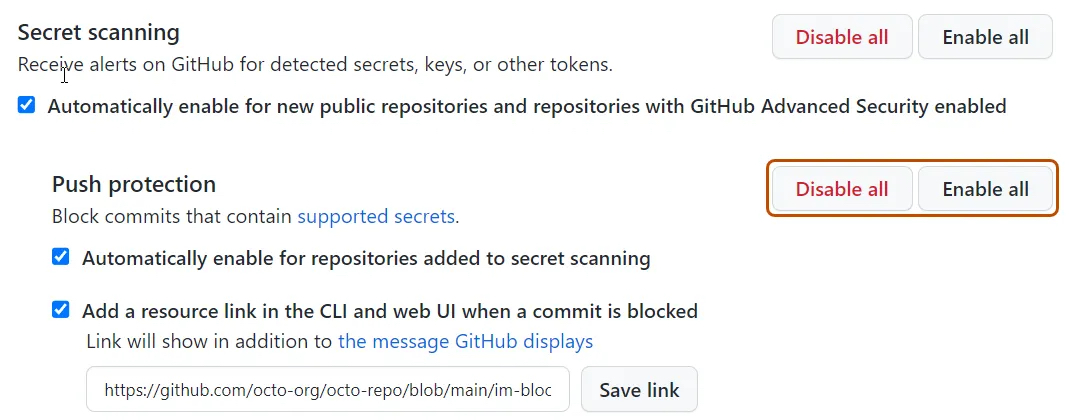
Organizations with GitHub Superior Safety can allow the key scanning push safety function at each repository and group ranges through the API or with only one click on from the consumer interface.
The detailed process for enabling push safety in your group requires you to:
- On GitHub.com, navigate to the principle web page of the group.
- Beneath your group identify, click on Settings.
- Within the “Safety” part of the sidebar, click on Code safety and evaluation.
- Beneath “Configure code safety and evaluation,” discover “GitHub Superior Safety.”
- Beneath “Secret scanning,” click on Allow all subsequent to “Push safety.”
- Optionally, click on “Routinely allow for personal repositories added to secret scanning.”
It can be enabled for single repositories by toggling it from every repo’s Settings > Safety & evaluation > GitHub Superior Safety dialog.
Extra particulars on utilizing push safety from the command line or permitting some secrets and techniques to be pushed can be found on GitHub’s documentation web site.
Uncovered credentials and secrets and techniques have led to high-impact breaches lately, as BleepingComputer has beforehand reported [1, 2, 3].
Due to this fact, enabling push safety for personal repositories or without cost on public repositories to make sure that code pushes are robotically blocked in the event that they include any secrets and techniques is an easy solution to defend towards unintended leaks with doubtlessly large impacts.
