
Hackers working for the Foremost Directorate of the Common Workers of the Armed Forces of the Russian Federation, extra generally often called the GRU, have been concentrating on Android gadgets in Ukraine with a brand new malicious framework named ‘Notorious Chisel.
The toolkit offers hackers backdoor entry by means of a service hidden in The Onion Router (Tor) anonymity community, lets them scan native information, intercept community visitors, and exfiltrate knowledge.
The malware was first highlighted in a warning from the Ukrainian Safety Service (SSU) earlier this month about efforts from the Sandworm hacking group to penetrate army command techniques.
Experiences as we speak from the UK Nationwide Cyber Safety Heart (NCSC) and the US Cybersecurity and Infrastructure Safety Company (CISA) dive deeper into the technical particulars of Notorious Chisel, displaying its capabilities and sharing info that may assist defend in opposition to it.
Notorious Chisel particulars
The NCSC describes Notorious Chisel as “a set of parts which allow persistent entry to an contaminated Android system over the Tor community, and which periodically collates and exfiltrates sufferer info from compromised gadgets.”
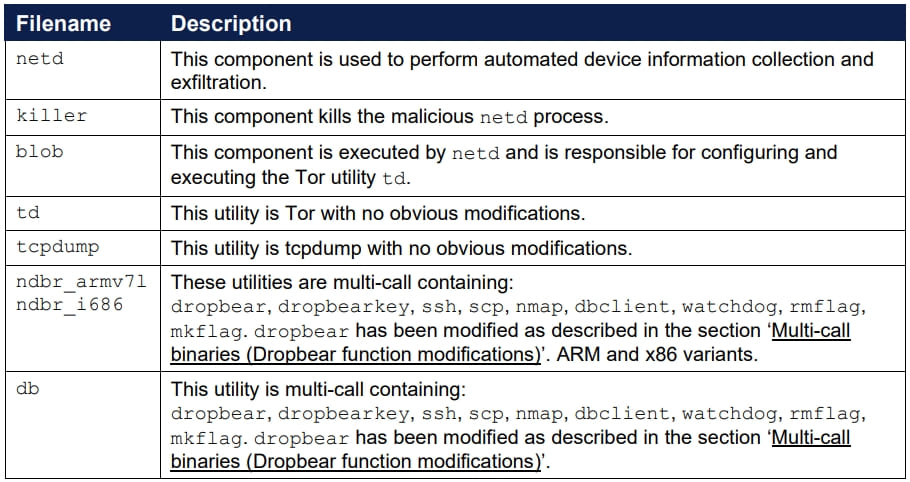
As soon as it infects a tool, the first element, ‘netd,’ which controls a set of instructions and shell scripts, replaces the legit netd Android system binary to realize persistence.
The malware targets Android gadgets and scans them to find info and purposes associated to the Ukrainian army to ship it to the attacker’s servers.
A hidden file (“.google.index”) retains monitor of the information despatched to the hackers utilizing MD5 hashes to stop duplicate knowledge. The system’s restrict is 16,384 information, although, so duplicates are despatched past that time.
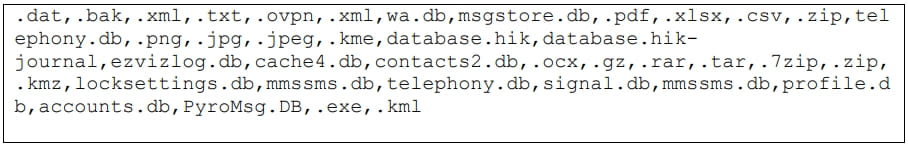
Notorious Chisel targets the file extensions within the picture beneath and the directories it scans embody the system’s inside reminiscence and any SD playing cards obtainable.
Android’s /knowledge/ listing is scanned for purposes like Google Authenticator, OpenVPN Join, PayPal, Viber, WhatsApp, Sign, Telegram, Gmail, Chrome, Firefox, Courageous, Microsft One Cloud, Android Contacts, and lots of extra.
The malware also can collect {hardware} info, probe the native space community for open ports and lively hosts, and provides attackers distant entry by way of SOCKS and an SSH connection handed by means of a randomly generated .ONION area.
File and system knowledge exfiltration takes place each 86,000 seconds, which is sooner or later, LAN scanning takes place each two days, and essentially the most essential army knowledge are siphoned way more ceaselessly, each 600 seconds, which interprets to 10 minutes.
Configuration and execution of Tor providers that facilitate distant entry occurs each 6,000 seconds, and a community connectivity verify onto the “geodatatoo[.]com” area happens each 3 minutes.
The NCSC notes that Notorious Chisel isn’t notably stealthy and seems to goal at fast knowledge exfiltration and pivoting to extra precious army networks.
The company says that the toolkit’s parts will not be notably subtle (low to medium complexity) they usually appear to have been developed “developed with little regard to defence evasion or concealment of malicious exercise.”
NCSC’s report features a set of indicators of compromise, guidelines and signatures for detection
