New findings present that malicious actors may leverage a sneaky malware detection evasion approach and bypass endpoint safety options by manipulating the Home windows Container Isolation Framework.
The findings have been offered by Deep Intuition safety researcher Daniel Avinoam on the DEF CON safety convention held earlier this month.
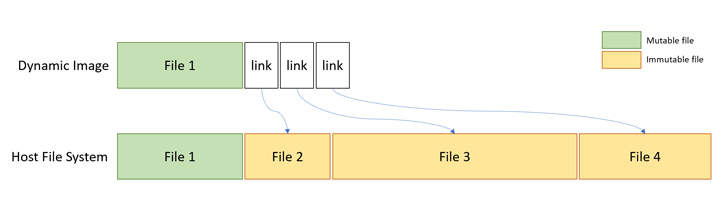
Microsoft’s container structure (and by extension, Home windows Sandbox) makes use of what’s known as a dynamically generated picture to separate the file system from every container to the host and on the identical time keep away from duplication of system information.
It is nothing however an “working system picture that has clear copies of information that may change, however hyperlinks to information that can’t change which might be within the Home windows picture that already exists on the host,” thereby bringing down the general measurement for a full OS.

“The result’s pictures that include ‘ghost information,’ which retailer no precise information however level to a unique quantity on the system,” Avinoam mentioned in a report shared with The Hacker Information. “It was at this level that the thought struck me — what if we will use this redirection mechanism to obfuscate our file system operations and confuse safety merchandise?”
That is the place the Home windows Container Isolation FS (wcifs.sys) minifilter driver comes into play. The driving force’s most important function is to handle the file system separation between Home windows containers and their host.
In different phrases, the thought is to have the present course of operating inside a fabricated container and leverage the minifilter driver to deal with I/O requests such that it will possibly create, learn, write, and delete information on the file system with out alerting safety software program.
 |
| Supply: Microsoft |
It is value stating at this stage {that a} minifilter attaches to the file system stack not directly, by registering with the filter supervisor for the I/O operations that it chooses to filter. Every minifilter is allotted a Microsoft-assigned “integer” altitude worth primarily based on filter necessities and cargo order group.
The wcifs driver has an altitude vary of 180000-189999 (particularly 189900), whereas antivirus filters, together with these from third-parties, perform at an altitude vary of 320000-329999. Consequently, varied file operations might be carried out with out getting their callbacks triggered.

“As a result of we will override information utilizing the IO_REPARSE_TAG_WCI_1 reparse tag with out the detection of antivirus drivers, their detection algorithm won’t obtain the entire image and thus won’t set off,” Avinoam defined.
That having mentioned, pulling off the assault requires administrative permissions to speak with the wcifs driver and it can’t be used to override information on the host system.
The disclosure comes because the cybersecurity firm demonstrated a stealthy approach known as NoFilter that abuses the Home windows Filtering Platform (WFP) to raise a consumer’s privileges to that of SYSTEM and probably execute malicious code.
The assaults permit using WFP to duplicate entry tokens for an additional course of, set off an IPSec connection and leverage the Print Spooler service to insert a SYSTEM token into the desk, and make it attainable to acquire the token of one other consumer logged into the compromised system for lateral motion.

