
Hackers are utilizing a important exploit chain to focus on Juniper EX switches and SRX firewalls through their Web-exposed J-Internet configuration interface.
Profitable exploitation permits unauthenticated attackers to remotely execute code on unpatched units.
“With a particular request that does not require authentication an attacker is ready to add arbitrary recordsdata through J-Internet, resulting in a lack of integrity for a sure a part of the file system, which can enable chaining to different vulnerabilities,” Juniper says.
One week after Juniper disclosed and launched safety updates to patch the 4 flaws that may be chained to realize distant code execution, watchTowr Labs safety researchers launched a proof-of-concept (PoC) exploit focusing on the SRX firewall bugs (tracked as CVE-2023-36846 and CVE-2023-36845).
Whereas Juniper stated there was no proof of energetic exploitation, watchTowr Labs stated they imagine attackers would quickly begin focusing on unpatched Juniper units in widescale assaults.
“Given the simplicity of exploitation, and the privileged place that JunOS units maintain in a community, we’d not be stunned to see large-scale exploitation,” the researchers warned.
As anticipated, safety researchers on the nonprofit web safety group Shadowserver Basis revealed at present that they’d detected exploitation makes an attempt beginning the identical day watchTowr Labs’ PoC exploit was launched.
“Since twenty fifth August we’re seeing exploitation makes an attempt from a number of IPs for Juniper J-Internet CVE-2023-36844 (& mates) focusing on /webauth_operation.php endpoint,” Shadowserver Basis tweeted on Tuesday.
“Identical day an exploit POC was printed. This entails combining decrease severity CVEs to realize pre-auth RCE.”
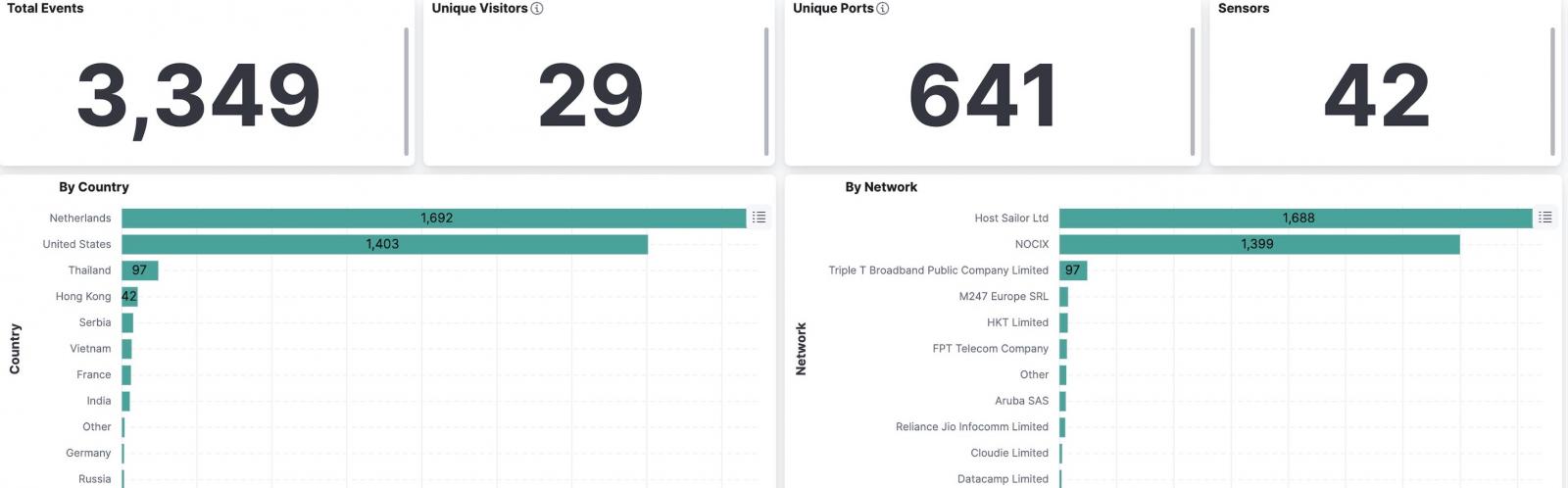
Shadowserver CEO Piotr Kijewski confirmed to BleepingComputer that the attackers are utilizing exploits constructed utilizing watchTowr Labs’ PoC as inspiration.
“The exploitation makes an attempt look like primarily based on this exploit POC, with some variations, which makes an attempt to add a PHP file after which execute it. So I assume we could count on webshells,” Kijewski stated.
“Primarily based on our honeypot observations, I might say all Juniper cases with J-Internet uncovered have already been hit. 29 IPs at the moment making an attempt these assaults, [..] probably a number of menace actors.”
Presently, over 8,200 Juniper units have their J-Internet interfaces uncovered on-line, in accordance with Shadowserver knowledge, most of them from South Korea.
Admins are suggested to use patches or improve JunOS to the newest launch instantly or, at the least, disable Web entry to the J-Internet interface to take away the assault vector.
