
Hackers are more and more abusing the official Cloudflare Tunnels characteristic to create stealthy HTTPS connections from compromised units, bypass firewalls, and keep long-term persistence.
The approach is not fully new, as Phylum reported in January 2023 that menace actors created malicious PyPI packages that used Cloudflare Tunnels to stealthy steal knowledge or remotely entry units.
Nevertheless, it seems that extra menace actors have began to make use of this tactic, as GuidePoint’s DFIR and GRIT groups reported final week, seeing an uptick in exercise.
Abusing Cloudflare Tunnels
CloudFlare Tunnels is a well-liked characteristic offered by Cloudflare, permitting customers to create safe, outbound-only connections to the Cloudflare community for internet servers or functions.
Customers can deploy a tunnel just by putting in one of many accessible cloudflared purchasers for Linux, Home windows, macOS, and Docker.
From there, the service is uncovered to the web on a user-specified hostname to accommodate official use-case situations similar to useful resource sharing, testing, and so forth.
Cloudflare Tunnels present a spread of entry controls, gateway configurations, group administration, and person analytics, giving customers a excessive diploma of management over the tunnel and the uncovered compromised providers.
In GuidePoint’s report, the researchers say that extra menace actors abuse Cloudflare Tunnels for nefarious functions, similar to gaining stealthy persistent entry to the sufferer’s community, evading detection, and exfiltrating compromised units’ knowledge.
A single command from the sufferer’s gadget, which does not expose something aside from the attacker’s distinctive tunnel token, is sufficient to arrange the discreet communication channel. On the identical time, the menace actor can modify a tunnel’s configuration, disable, and allow it as wanted in real-time.
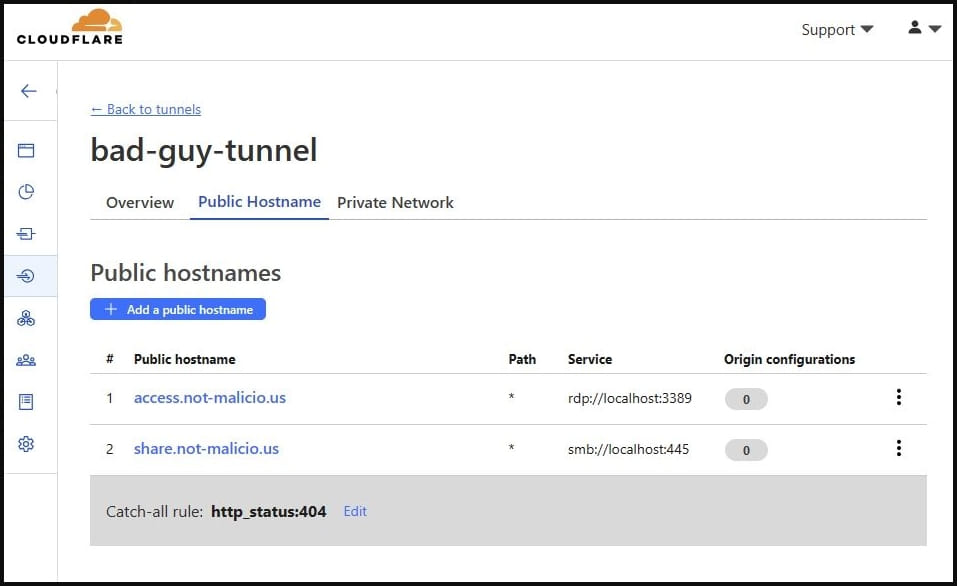
Supply: GuidePoint
“The tunnel updates as quickly because the configuration change is made within the Cloudflare Dashboard, permitting TAs to allow performance solely once they wish to conduct actions on the sufferer machine, then disable performance to forestall publicity of their infrastructure,” explains GuidePoint.
“For instance, the TA may allow RDP connectivity, gather info from the sufferer machine, then disable RDP till the next day, thus reducing the possibility of detection or the flexibility to look at the area utilized to determine the connection.”
As a result of the HTTPS connection and knowledge alternate happens over QUIC on port 7844, it’s unlikely that firewalls or different community safety options will flag this course of until they’re particularly configured to take action.
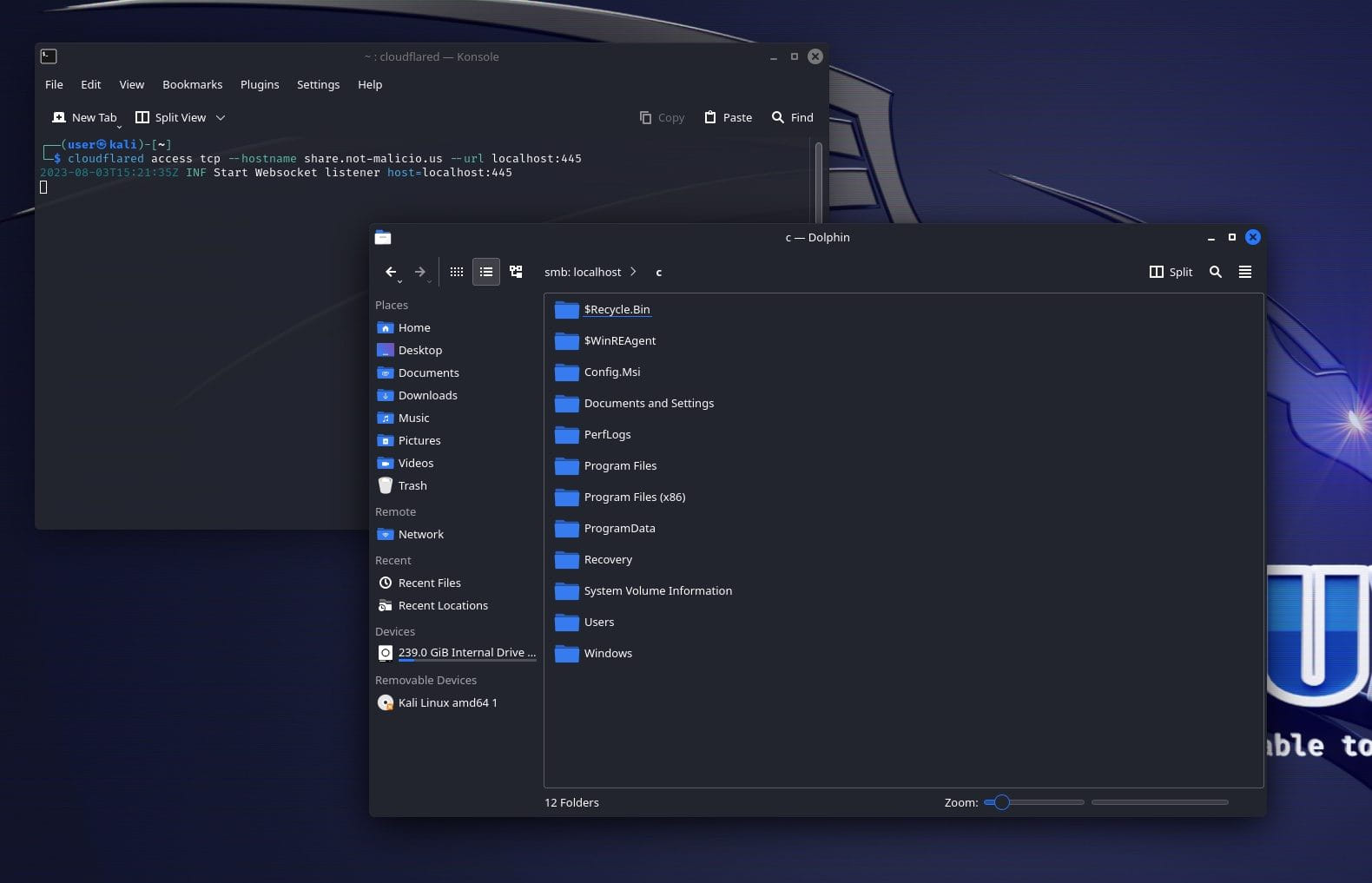
Supply: GuidePoint
Additionally, if the attacker desires to be much more stealthy, they’ll abuse Cloudflare’s ‘TryCloudflare‘ characteristic that lets customers create one-time tunnels with out creating an account.
To make issues worse, GuidePoint says it is also attainable to abuse Cloudflare’s ‘Non-public Networks’ characteristic to permit an attacker who has established a tunnel to a single consumer (sufferer) gadget to entry a whole vary of inner IP addresses remotely.
“Now that the non-public community is configured, I can pivot to units on the native community, accessing providers which can be restricted to native community customers,” warned GuidePoint researcher Nic Finn.
To detect unauthorized use of Cloudflare Tunnels, GuidePoint recommends that organizations monitor for particular DNS queries (shared within the report) and use non-standard ports like 7844.
Moreover, as Cloudflare Tunnel requires the set up of the ‘cloudflared‘ consumer, defenders can detect its use by monitoring file hashes related to consumer releases.
