
Cybercriminals are leveraging a reliable Home windows device referred to as ‘Superior Installer’ to contaminate the computer systems of graphic designers with cryptocurrency miners.
The attackers promote installers for standard 3D modeling and graphic design software program comparable to Adobe Illustrator, Autodesk 3ds Max, and SketchUp Professional, possible via black hat SEO methods.
Nonetheless, these installers embrace hidden malicious scripts that infect downloaders with distant entry trojans (RATs) and cryptomining payloads.
The menace actors are specializing in these particular targets as graphics designers, animators, and video editors are extra possible to make use of computer systems with highly effective GPUs that help larger mining hash charges, making the cryptojacking operation extra worthwhile.
The marketing campaign was found by Cisco Talos, which in the present day studies it has been underway since a minimum of November 2021.
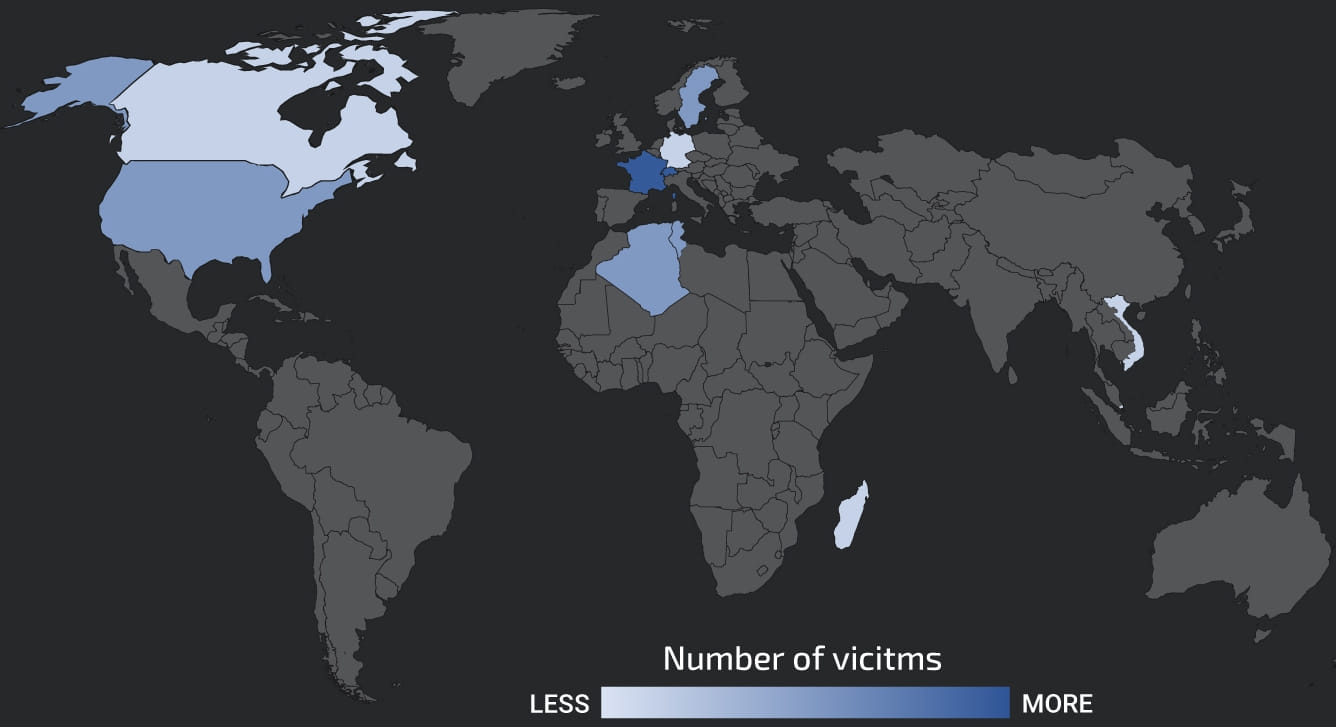
At present, many of the victims are positioned in France and Switzerland, whereas there’s additionally a notable variety of infections in america, Canada, Germany, Algeria, and Singapore.
Two assault strategies
Cisco’s analysts have noticed two distinct assaults used on this marketing campaign.
In each circumstances, the attackers use Superior Installer to create installer recordsdata for Home windows filled with malicious PowerShell and batch scripts which can be executed upon the installer’s launch via the software program’s “Customized Motion” characteristic.
The 2 assault strategies differ within the scripts executed, the complexity of the an infection chain, and the ultimate payloads dropped on the goal gadget.
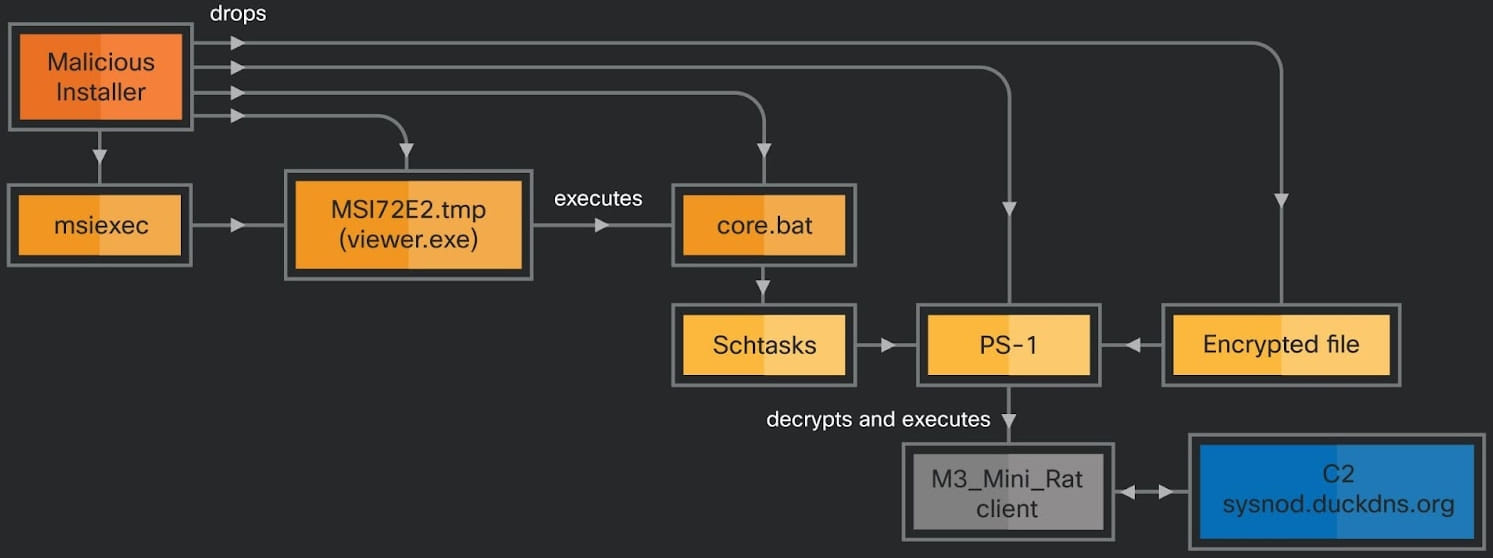
The primary methodology makes use of a batch script (core.bat) to arrange a recurring process operating a PowerShell script that decrypts the ultimate payload (M3_Mini_Rat).
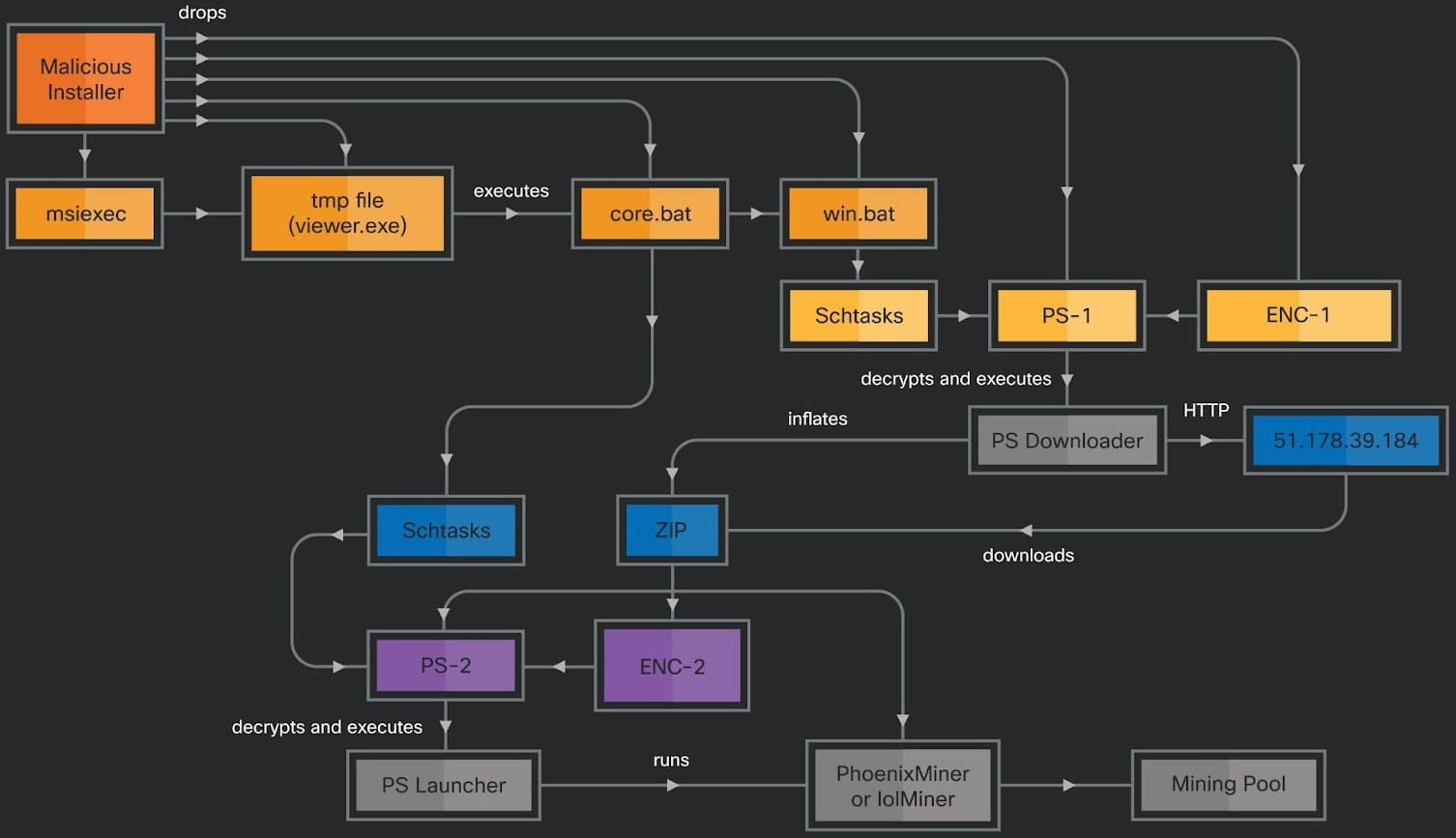
The second assault methodology drops two malicious scripts, core.bat and win.bat, that arrange scheduled duties to run PowerShell scripts.
The PowerShell executed by the win.bat file decrypts a downloader script and fetches a ZIP archive containing a payload (PhoenixMiner or lolMiner), a second PS script (which core.bat schedules for), and one other encrypted file.
The primary methodology, which delivers a backdoor payload, could possibly be chosen by the attackers in circumstances the place sustaining discreet, extended entry to focus on methods is the first purpose.
The second assault methodology, which employs cryptominers, is geared in direction of swift monetary features at a better threat of detection.
Mining and RAT payloads
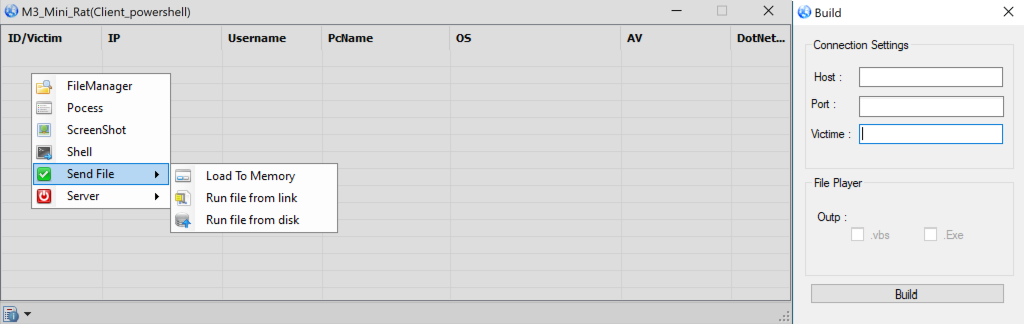
The M3_Mini_Rat payload provides the attackers distant entry capabilities, enabling them to carry out system reconnaissance and set up further payloads on the contaminated system.
The RAT device can carry out the next capabilities:
- System Reconnaissance: Gathers particulars like username, OS model, anti-virus standing, community standing, and {hardware} specs.
- Course of Administration: Lists and manages operating processes, together with termination capabilities.
- File System Exploration: Enumerates logical drives and retrieves particulars of particular folders.
- Command & Management: Makes use of a TCP connection for distant administration duties and command receipt.
- File Administration: Handles downloading, checking, renaming, and deleting recordsdata, and may execute malicious binaries.
- Knowledge Transmission: Sends information, together with reconnaissance particulars, again to the attacker’s server.
- Particular Checks: Identifies particular server processes, just like the Citrix connection middle server.
- Exit: Presents methods to securely exit the consumer and handle its information streams.
The opposite two payloads, PhoenixMiner and lolMiner, mine cryptocurrency by hijacking the computational energy of AMD, Nvidia, and Intel (lolMiner solely) graphics playing cards.
PhoenixMiner is an Ethash (ETH, ETC, Musicoin, EXP, UBQ, and so on.) miner, whereas lolMiner helps a number of protocols together with Etchash, Autolykos2, Beam, Grin, Ae, ALPH, Flux, Equihash, Kaspa, Nexa, Ironfish and others.
The lolMiner model noticed on this marketing campaign is 1.76, which helps simultaneous mining of two totally different cryptocurrencies.
The PhoenixMiner configuration units the GPU energy restrict to 75% and the system enjoyable management max velocity to 65%.
Comparable restrictions are seen within the lolMiner parameters, which makes use of 75% of the GPU energy and pauses mining if the temperature reaches 70 levels Celsius.
This means that the attackers attempt to keep away from being detected by utilizing too many assets.
A full listing of the indications of compromise for this marketing campaign may be discovered on this GitHub repository.
