This text is just for readers’ consciousness and to maintain them protected in opposition to phishing gadgets which can be getting used to repeat and misuse credit score and debit card information. The potential of hacking has elevated with the current use of contactless playing cards
NFC, which stands for near-field communication, is a short-range wi-fi know-how that enables gadgets to speak with one another when they’re in shut proximity, normally no quite a lot of centimeters aside. It’s a kind of RFID (radio frequency identification) know-how, however it operates at a a lot shorter vary and at the next frequency.
NFC is utilized in quite a few functions, together with contactless funds, entry management, and information switch. Now even our automobiles and toll tax limitations use the NFC. The know-how is broadly utilized in many gadgets, together with smartwatches and rings, to allow a wide range of capabilities, resembling authentication and funds.
NFC-enabled rings will also be used for authentication and fee functions. For instance, an NFC-enabled ring can be utilized to unlock a door or make a fee by merely holding it close to an NFC reader. These kinds of gadgets supply a handy and safe solution to conduct transactions and entry safe areas.
These days, passports additionally use NFC for transmitting information to a system containing delicate details about you. However the day by day involvement and dependency on NFC know-how increase a priority about whether or not this know-how could be problematic for our safety. Earlier than getting deeper into its safety threats, let’s see how this know-how works.
How NFC Works?
NFC makes use of magnetic discipline induction to transmit information between two NFC-enabled gadgets which can be bodily shut to one another. When one gadget, resembling a smartphone, is introduced close to one other NFC-enabled gadget, an electromagnetic discipline is generated between the 2 gadgets. This discipline permits the gadgets to speak with one another and trade information. One gadget has a chip with a coil however no energy provide whereas the opposite is a reader or author having an antenna and energy provide to transmit the information.
NFC communication entails three major steps:
- Initiating communication: One of many gadgets, normally the one which initiates the communication, turns into an NFC reader. The opposite gadget turns into an NFC tag, which is learn by the reader.
- Establishing a connection: The reader and the tag set up a connection by exchanging a collection of alerts. The reader sends a request to the tag, and the tag responds by sending again its ID and different info.
- Transferring information: As soon as the connection is established, the gadgets can trade information. The reader can request particular information from the tag, or the tag can ship information to the reader with out a request.
How Safe NFC Debit Playing cards Are?
NFC is commonly utilized in credit score and debit playing cards as a solution to allow contactless funds. While you use an NFC-enabled credit score or debit card to make a fee, the cardboard communicates with the fee terminal utilizing RF waves. This lets you make a fee just by tapping your card on the terminal, with out the necessity to insert it right into a card reader and enter a private identification quantity (PIN).

(Credit score: https://flipperzero.one)
NFC relies on the ISO/IEC 14443 normal, which defines the technical necessities for contactless sensible playing cards and the communication between them and the reader.
Various kinds of NFC applied sciences are utilized in credit score and debit playing cards, together with:
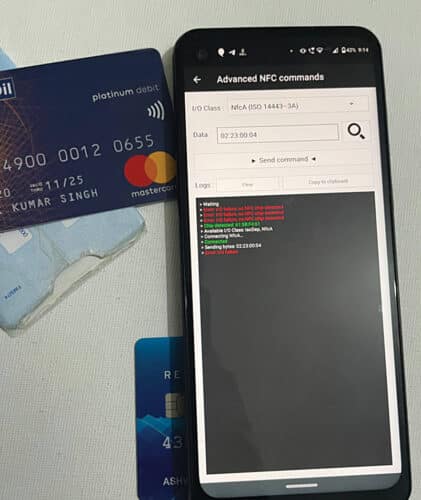
Sort A: That is probably the most broadly used kind of NFC know-how in credit score and debit playing cards. It operates at a frequency of 13.56MHz and makes use of a protocol often called ISO/IEC 14443-3A.
Sort B: This sort of NFC know-how is much like Sort A, however it makes use of a unique protocol often called ISO/IEC 14443-3B. It’s much less widespread than Sort A, however it’s nonetheless utilized in some credit score and debit playing cards.
FeliCa: It is a proprietary NFC know-how developed by Sony and used primarily in Japan. It additionally operates at a frequency of 13.56MHz however makes use of a protocol often called JIS X 6319-4.
Total, the kind of NFC know-how utilized in a credit score or debit card will rely upon the precise card and the fee system it’s designed to work with. No matter the kind of NFC know-how used, the safety measures constructed into NFC know-how and the extra security measures of credit score and debit playing cards, resembling chip-and-pin or chip-and-signature safety, assist to make sure the protection and safety of contactless funds.
That being stated, no know-how is totally foolproof, and there’s at all times a danger {that a} hacker might discover a solution to bypass the safety measures in place. To assist defend your self from potential NFC-related fraud, you will need to take steps to safe your credit score and debit playing cards, resembling preserving them in a protected location, monitoring your accounts for any suspicious exercise, and reporting any misplaced or stolen playing cards as quickly as attainable.
Hacking NFC
There are other ways a hacker may try and hack NFC, resembling:
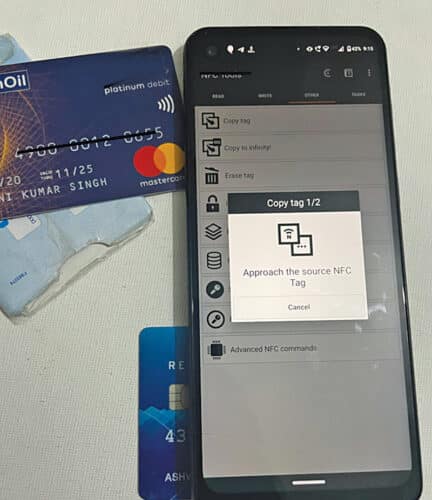
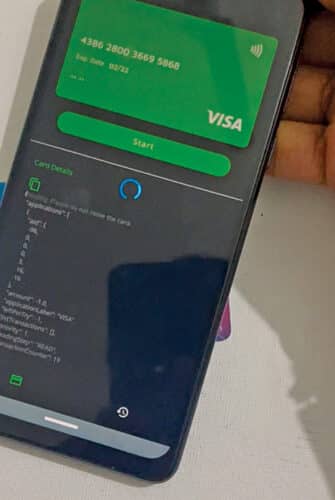
Skimming: This entails utilizing a reader and author gadget to seize the information transmitted between an NFC-enabled credit score or debit card and a fee terminal. The info is then used to create a duplicate of the cardboard. Or hackers can use the high-range NFC reader and author and go by you to learn the cardboard particulars and make a duplicate of your NFC card to make fraudulent purchases.

There are numerous instruments and apps like Flipper utilizing which the hackers can learn your card information, retailer it, and even clone it. The info saved in NFC will also be copied simply by a telephone or a reader gadget. The hackers can then use your card quantity and different particulars to make use of it for fraudulent purchases. In worst instances, hackers may even inject their very own code or just erase your bank card by utilizing NFC author instruments. Nonetheless, no such complaints have arisen but.
It’s nonetheless exhausting these days to do fraudulent transactions utilizing hacked credit score or debit card particulars because it requires an OTP or PIN whereas spending past a certain quantity (usually, ₹5,000). A few methods a hacker might copy your card’s particulars are talked about under.
Man-in-the-middle Assault: This entails a hacker intercepting the communication between an NFC-enabled card and a fee terminal, and both altering the information being transmitted or injecting their very own information into the communication.
Bodily Tampering: This entails bodily modifying an NFC-enabled card or fee terminal so as to bypass safety measures or to achieve entry to delicate information.
The principle characteristic of NFC is it really works solely over a really brief distance. So, hackers can fetch information out of your NFC-enabled card solely when they’re close to the cardboard. It’s attainable to design an NFC reader with an extended vary by utilizing a number of coils.
NFC operates at a high-frequency 13.56MHz and requires shut proximity between the 2 gadgets so as to set up a connection. Rising the vary of an NFC reader past a number of centimeters would require using a decrease frequency, which might end in a slower information switch price.
In the event you analyze the underlying bodily equations within the case of a round loop coil antenna, the close to discipline vary (appropriate for NFC communications) is about 1.414 instances the radius of the round coil. To realize a sensible 60cm vary, chances are you’ll attempt to create a close to discipline with a theoretical vary a number of instances larger, as an illustration, 180-240cm, for which you want a round coil of about 2.5-3.4 meters in diameter. However you may change the form and check out the sq. form for that.
The best way to Shield Your self?
The potential of your debit or bank card being cloned will increase tremendously in public locations and crowded metro, bus, prepare, and many others, whereas touring. Anybody with an NFC reader or telephone can get your card information by coming near your pockets in your pocket or elsewhere.
One of many measures that may be taken to guard your self is by utilizing the Faraday purse or pockets. These wallets have layers of Faraday cage that block the sign and defend in opposition to your playing cards’ information being learn or cloned in such crowded locations. There are some small metallic enclosures additionally out there, which could be simply saved in a pocket like a pockets, to maintain the playing cards protected.

Setting limits to NFC transactions may also defend you from heavy losses. You may ask your financial institution or card supplier to set transaction limits for contactless funds by your playing cards. Utilizing, multi-factor authentication or a digital PIN setting for an NFC card is one other solution to defend your self from fraud.
Ashwini Kumar Sinha is an IoT and AI fanatic tech journalist at EFY

