Iranian nation-state actors have been conducting password spray assaults in opposition to 1000’s of organizations globally between February and July 2023, new findings from Microsoft reveal.
The tech big, which is monitoring the exercise below the title Peach Sandstorm (previously Holmium), stated the adversary pursued organizations within the satellite tv for pc, protection, and pharmaceutical sectors to seemingly facilitate intelligence assortment in help of Iranian state pursuits.
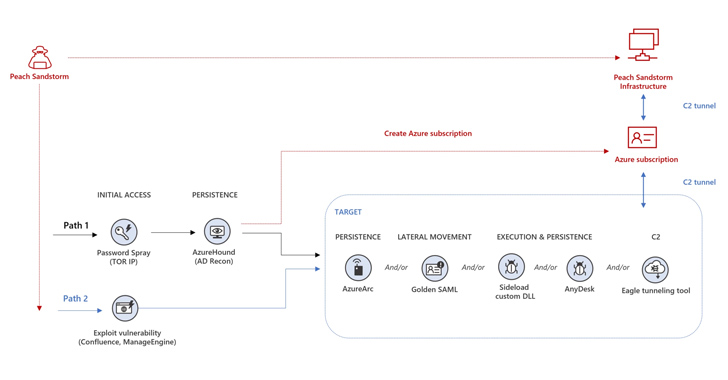
Ought to the authentication to an account achieve success, the menace actor has been noticed utilizing a mixture of publicly obtainable and customized instruments for discovery, persistence, and lateral motion, adopted by information exfiltration in restricted instances.
Peach Sandstorm, additionally recognized by the names APT33, Elfin, and Refined Kitten, has been linked to spear-phishing assaults in opposition to aerospace and power sectors previously, a few of which have entailed the usage of the SHAPESHIFT wiper malware. It is stated to be energetic since at the least 2013.

“Within the preliminary part of this marketing campaign, Peach Sandstorm carried out password spray campaigns in opposition to 1000’s of organizations throughout a number of sectors and geographies,” the Microsoft Risk Intelligence group stated, noting among the exercise is opportunistic.
Password spraying refers to a way whereby a malicious actor makes an attempt to authenticate to many alternative accounts utilizing a single password or an inventory of commonly-used passwords. It is totally different from brute-force assaults by which a single account is focused with many credential combos.
“Exercise noticed on this marketing campaign aligned with an Iranian sample of life, notably in late Might and June, the place exercise occurred virtually solely between 9:00 AM and 5:00 PM Iran Customary Time (IRST),” Microsoft additional added.
Intrusions are characterised by means of open-source crimson group instruments similar to AzureHound, a Golang binary to conduct reconnaissance, and ROADtools to entry information in a goal’s cloud atmosphere. The assaults additional have been noticed utilizing Azure Arc to ascertain persistence by connecting to an Azure subscription managed by the menace actor.
Alternate assault chains mounted by Peach Sandstorm have entailed the exploitation of safety flaws in Atlassian Confluence (CVE-2022-26134) or Zoho ManageEngine (CVE-2022-47966) to realize preliminary entry.
Id is the New Endpoint: Mastering SaaS Safety within the Fashionable Age
Dive deep into the way forward for SaaS safety with Maor Bin, CEO of Adaptive Protect. Uncover why id is the brand new endpoint. Safe your spot now.
Another notable facets of the post-compromise exercise concern the deployment of AnyDesk distant monitoring and administration software to keep up entry, EagleRelay to tunnel visitors again to their infrastructure, and leveraging Golden SAML assault methods for lateral motion.
“Peach Sandstorm additionally created new Azure subscriptions and leveraged the entry these subscriptions offered to conduct extra assaults in different organizations’ environments,” Microsoft stated.
“As Peach Sandstorm more and more develops and makes use of new capabilities, organizations should develop corresponding defenses to harden their assault surfaces and lift prices for these assaults.”