The Knight ransomware is being distributed in an ongoing spam marketing campaign that pretends to be TripAdvisor complaints.
Knight ransomware is a current rebrand of the Cyclop Ransomware-as-a-Service, which switched its identify on the finish of July 2023.
Who’s Cyclops and Knight ransomware?
The Cyclops ransomware operation launched in Could 2023 when the operators started recruiting associates for the brand new ransomware-as-a-service (RaaS) on the RAMP hacking discussion board.
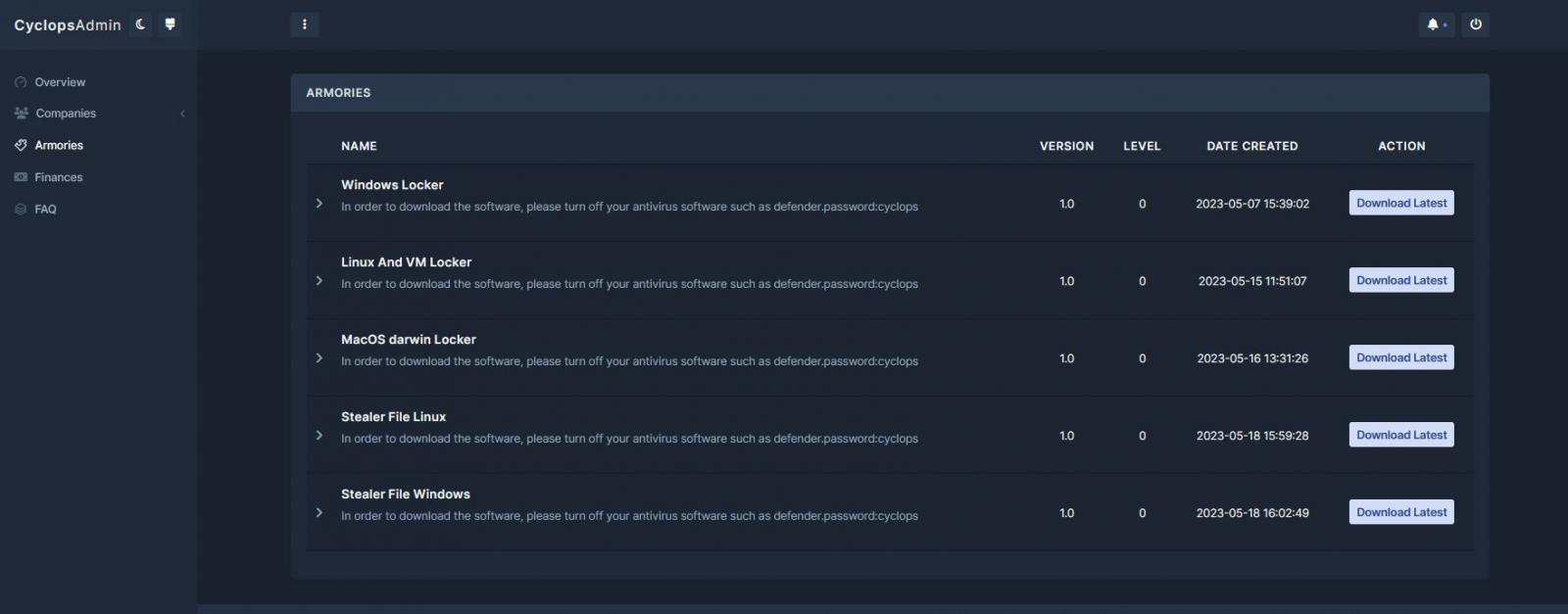
A report by Uptycs explains that the operation launched with encryptors for Home windows, macOS, and Linux/ESXi. The operation additionally presents associates information-stealing malware for Home windows and Linux, which isn’t usually seen in RaaS operations.
Supply: BleepingComputer
Along with their regular encryptors, the operation presents a ‘lite’ model to be used in spam and pray-and-spray mass distribution campaigns focusing on giant numbers of focused customers. This model seems to make the most of a hard and fast ransom quantity fairly than negotiating with victims.
On the finish of July, Cyclops rebranded as Knight, additionally stating they up to date the lite encryptor to assist ‘batch distribution’ and launched a brand new knowledge leak web site.
“We have up to date our new panel and formally modified our identify to Knight.We’re on the lookout for companions (of any sort) that!!!,” reads an announcement on the previous Cyclops and new Knight knowledge leak websites.
“We’ve additionally up to date the lite model to assist batch distribution.”
There are presently no victims or stolen recordsdata leaked on the Knight knowledge leak web site.
The Knight spam marketing campaign
This week, Sophos researcher Felix noticed a brand new spam marketing campaign pretending to be TripAdvisor complaints however distribute the Knight ransomware as an alternative.
Whereas the precise emails weren’t shared, Felix mentioned that the emails embrace ZIP file attachments named ‘TripAdvisorComplaint.zip’ that include an executable named ‘TripAdvisor Criticism – Potential Suspension.exe’ [VirusTotal].
A more recent model of this marketing campaign noticed and analyzed by BleepingComputer now consists of an HTML attachment named ‘TripAdvisor-Criticism-[random].PDF.htm’ [VirusTotal].
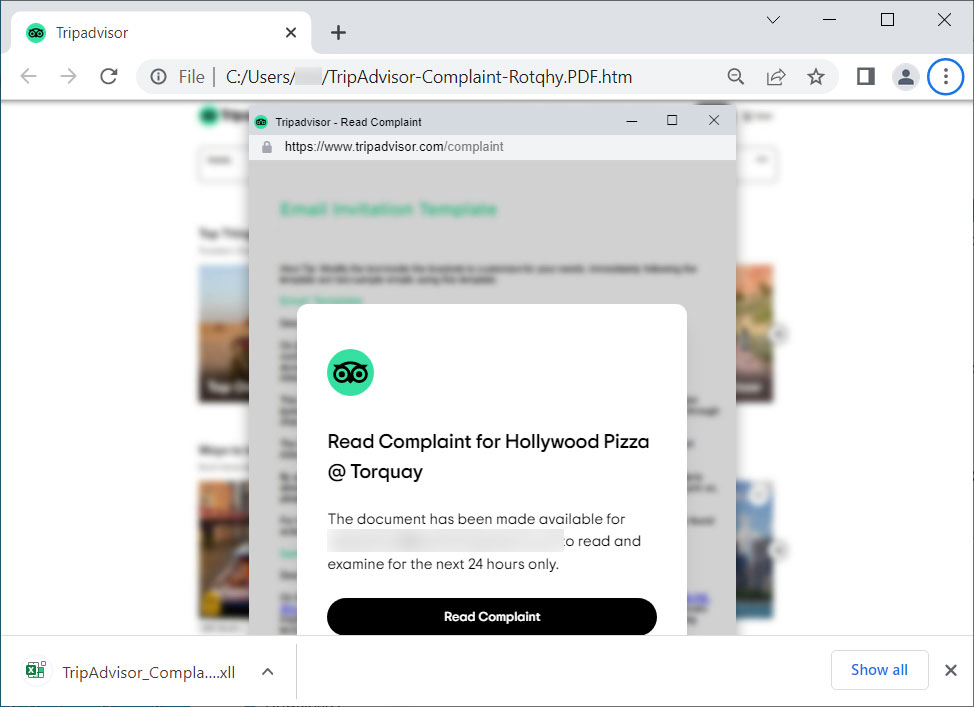
When the HTML file is opened, it can use Mr.D0x’s Browser-in-the-Browser phishing approach to open what seems to be a browser window to TripAdvisor.
This faux browser window pretends to be a criticism submitted to a restaurant, asking the consumer to overview it. Nevertheless, clicking the ‘Learn Criticism’ button will obtain an Excel XLL file named ‘TripAdvisor_Complaint-Potential-Suspension.xll’ [VirusTotal], as proven under.
Supply: BleepingComputer
This XLL file is created utilizing Excel-DNA, which integrates .NET into Microsoft Excel to execute the malware when it’s opened.
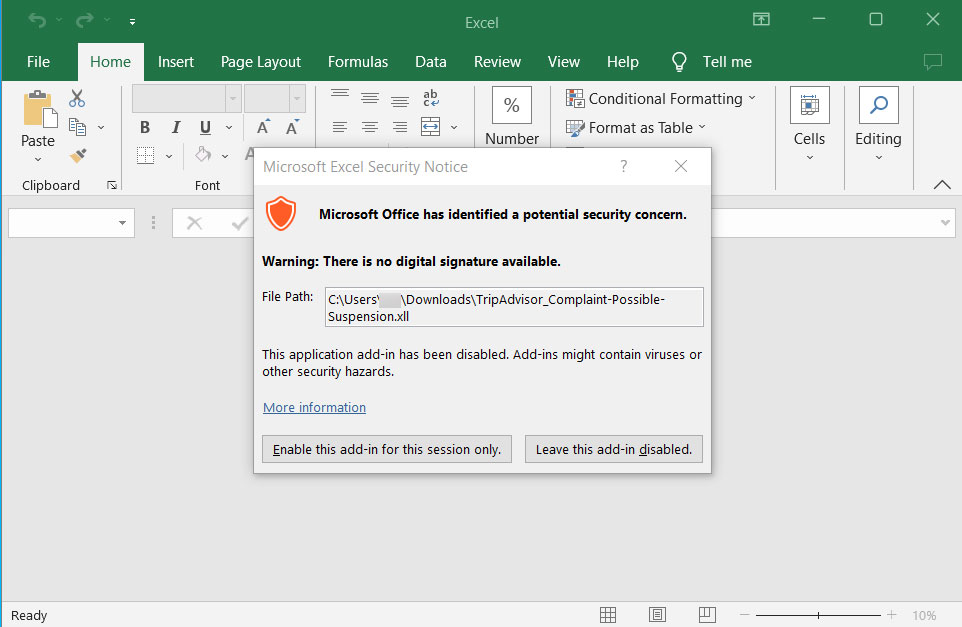
Whenever you open the XLL, Microsoft Excel will detect the Mark of the Internet (MoTW), added to recordsdata downloaded from the Web, together with electronic mail. If it detects the MoTW, it won’t allow the .NET add-in constructed into the Excel doc, nullifying the assault until a consumer unblocks the file.
Nevertheless, if there isn’t a MoTW flag on the file, Excel will immediate the consumer as to whether or not they need to allow the add-in, as proven under.
Supply: BleepingComputer
Enabling the add-in will trigger the Knight Lite ransomware encryptor to be injected into a brand new explorer.exe course of and start to encrypt the recordsdata in your laptop.
When encrypting recordsdata, it can append the .knight_l extension to encrypted recordsdata’ names, the place the ‘l’ portion probably stands for ‘lite.’
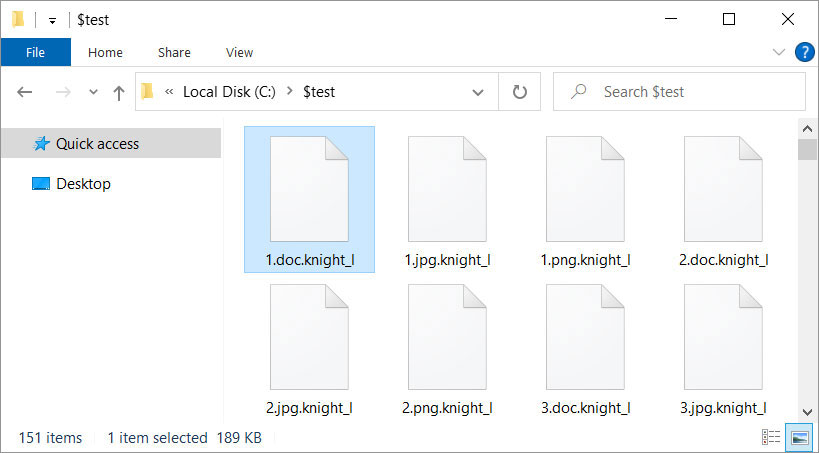
Supply: BleepingComputer
The ransomware may even create a ransom be aware named How To Restore Your Recordsdata.txt in every folder on the pc. The ransom be aware on this marketing campaign calls for $5,000 be despatched to a listed Bitcoin deal with and likewise incorporates a hyperlink to the Knight Tor web site.
Nevertheless, each ransom be aware on this marketing campaign seen by BleepingComputer makes use of the identical Bitcoin deal with of ’14JJfrWQbud8c8KECHyc9jM6dammyjUb3Z,’ which might make it inconceivable for the risk actor to find out which sufferer paid a ransom.
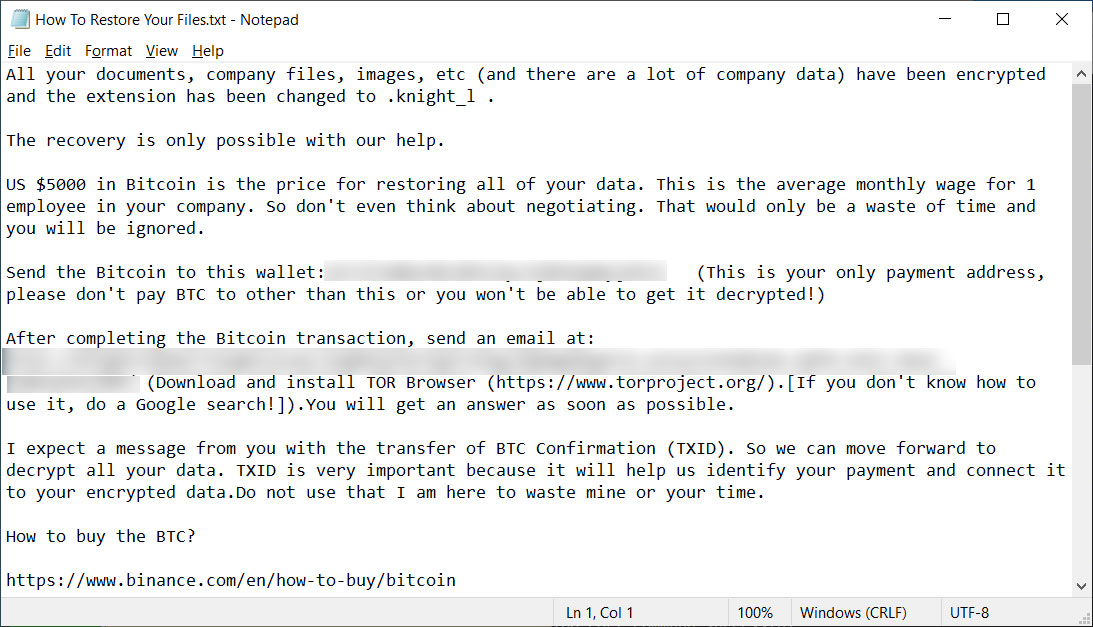
Supply: BleepingComputer
As it is a Knight Lite marketing campaign, visiting the location doesn’t show a negotiation panel. As an alternative, it reveals a message stating that victims ought to have paid the ransom demand already and to contact the affiliate at brahma2023@onionmail.org then.
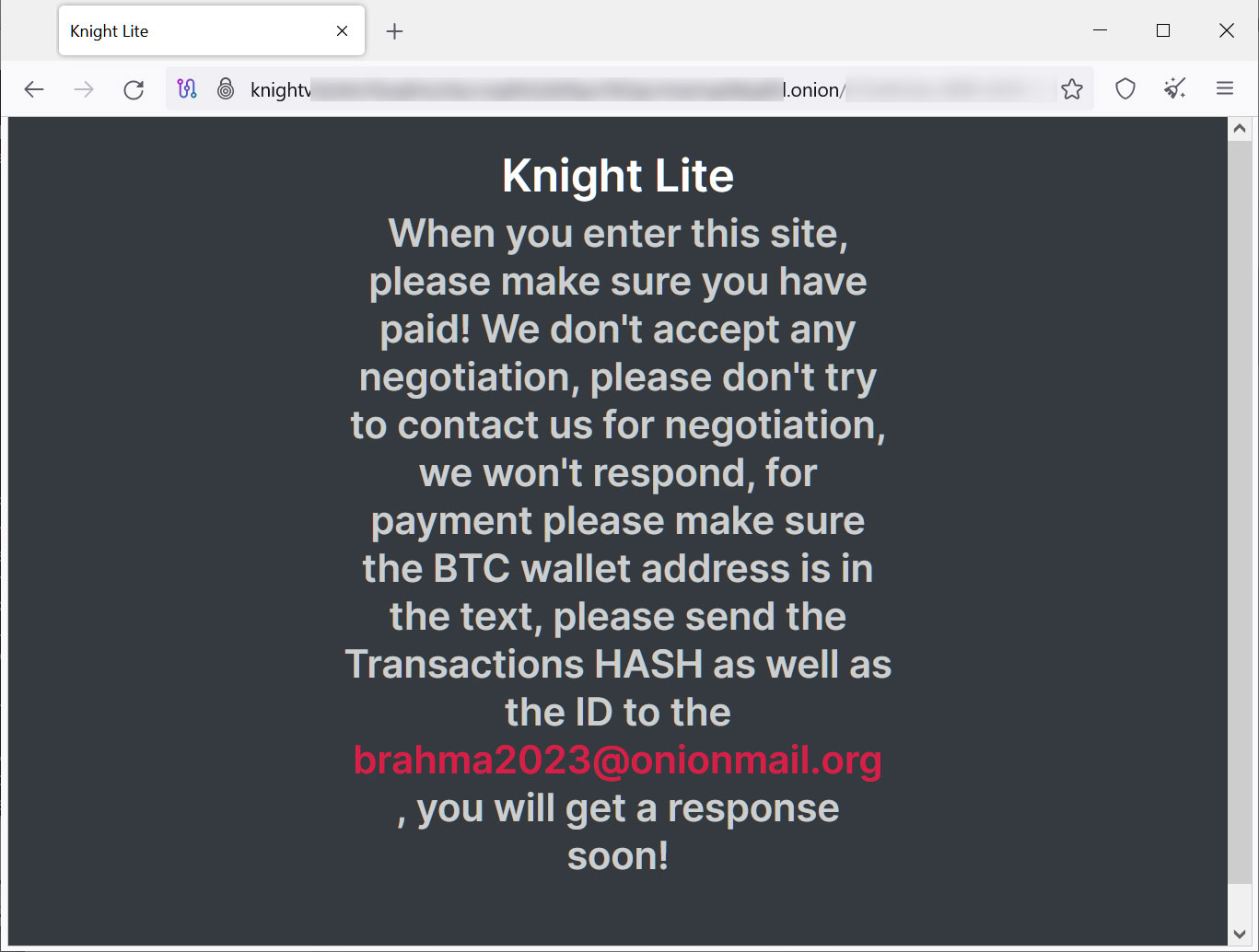
Supply: BleepingComputer
Right now, it isn’t identified if paying a ransom will end in receiving a decryptor from the Knight affiliate.
Moreover, all of the ransom notes seen by BleepingComputer make the most of the identical Bitcoin deal with, making it potential for another person to assert a fee as theirs, basically stealing your fee.
Due to this fact, it’s strongly suggested to chorus from paying a ransom on this marketing campaign, as there’s a good probability you’ll not obtain a decryptor.