
The Abyss Locker operation is the newest to develop a Linux encryptor to focus on VMware’s ESXi digital machines platform in assaults on the enterprise.
Because the enterprise shifts from particular person servers to digital machines for higher useful resource administration, efficiency, and catastrophe restoration, ransomware gangs create encryptors centered on focusing on the platform.
With VMware ESXi being one of the well-liked digital machine platforms, virtually each ransomware gang has begun to launch Linux encryptors to encrypt all digital servers on a tool.
Different ransomware operations that make the most of Linux ransomware encryptors, with most focusing on VMware ESXi, embody Akira, Royal, Black Basta, LockBit, BlackMatter, AvosLocker, REvil, HelloKitty, RansomEXX, and Hive.
The Abyss Locker
Abyss Locker is a comparatively new ransomware operation that’s believed to have launched in March 2023, when it started to focus on corporations in assaults.
Like different ransomware operations, the Abyss Locker risk actors will breach company networks, steal information for double-extortion, and encrypt units on the community.
The stolen information is then used as leverage by threatening to leak information if a ransom will not be paid. To leak the stolen information, the risk actors created a Tor information leak website named ‘Abyss-data’ that at present lists fourteen victims.
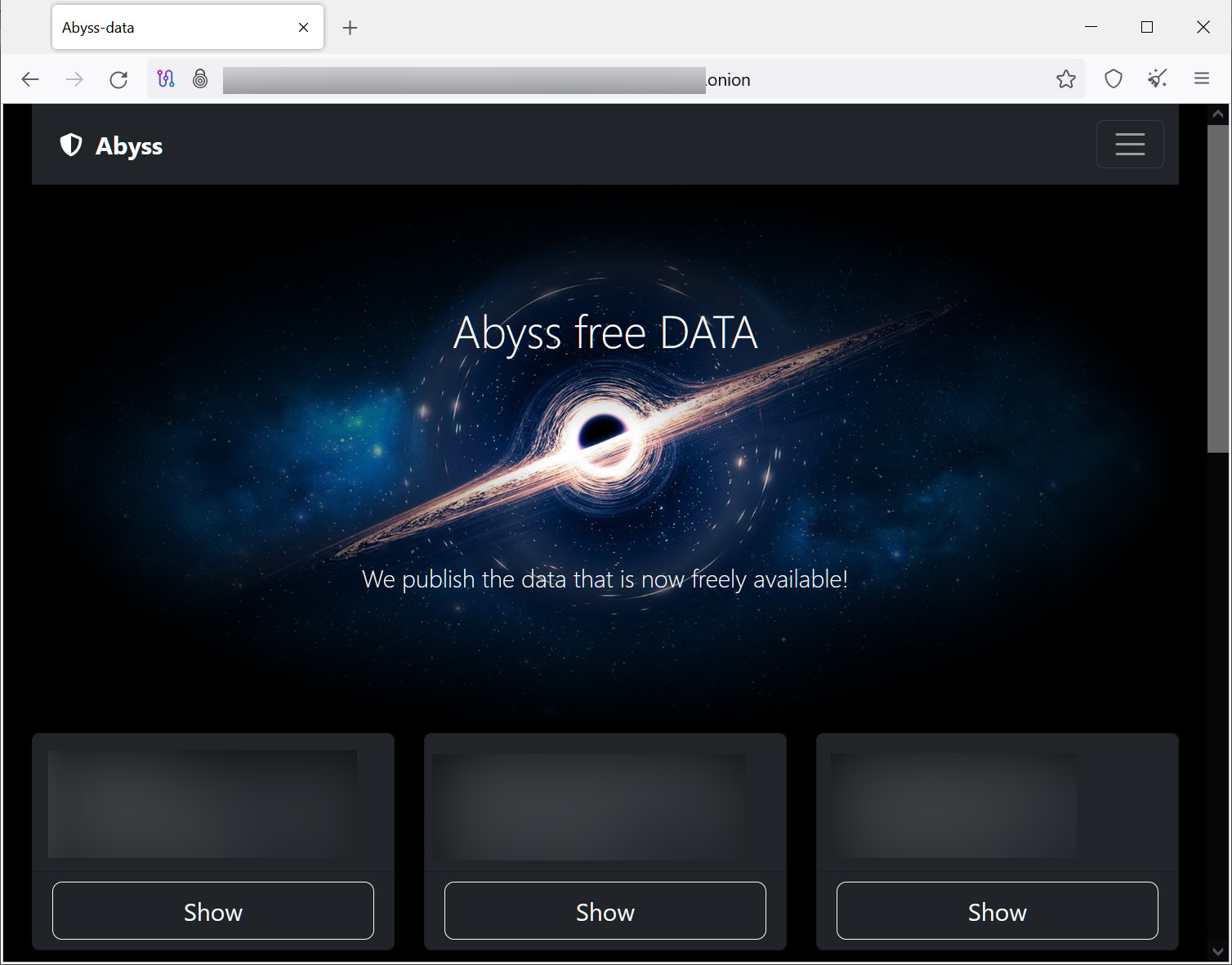
Supply: BleepingComputer
The risk actors declare to have stolen anyplace between 35 GB of knowledge from one firm to as excessive as 700 GB at one other.
Focusing on VMware ESXi servers
This week, safety researcher MalwareHunterTeam discovered a Linux ELF encryptor for the Abyss Locker operation and shared it with BleepingComputer for evaluation.
After wanting on the strings within the executable, it’s clear that the encryptor particularly targets VMware ESXi servers.
As you’ll be able to see from the instructions under, the encryptor makes use of the ‘esxcli’ command-line VMware ESXi administration instrument to first listing all obtainable digital machines after which terminate them.
esxcli vm course of listing
esxcli vm course of kill -t=gentle -w=%d
esxcli vm course of kill -t=exhausting -w=%d
esxcli vm course of kill -t=pressure -w=%dWhen shutting down the digital machines, Abyss Locker will use the ‘vm course of kill’ command and one of many gentle, exhausting, or compelled choices.
The gentle possibility performs a sleek shutdown, the exhausting possibility terminates a VM instantly, and pressure is used as a final resort.
The encryptor terminates all digital machines to permit the related digital disks, snapshots, and metadata to be correctly encrypted by encrypting all information with the next extensions: .vmdk (digital disks), .vmsd (metadata), and .vmsn (snapshots).
Along with focusing on digital machines, the ransomware can even encrypt all different information on the machine and append the .crypt extension to their filenames, as proven under.
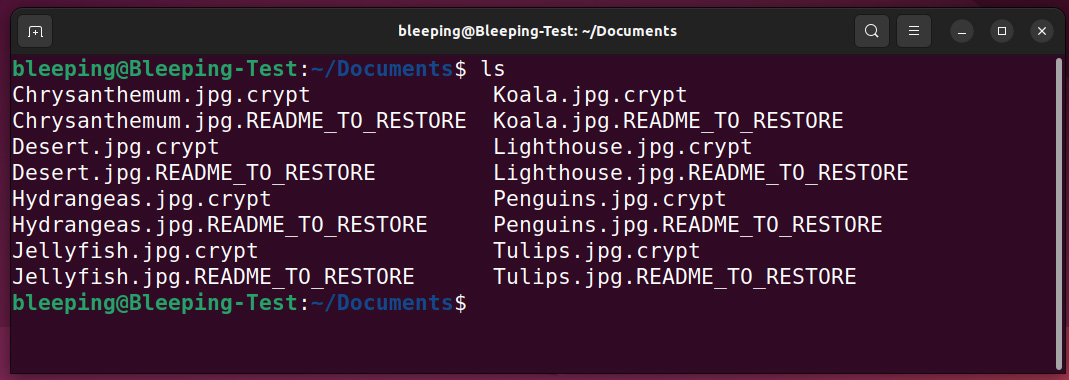
Supply: BleepingComputer
For every file, the encryptor can even create a file with a .README_TO_RESTORE extension, which acts because the ransom observe.
This ransom observe comprises info on what occurred to the information and a novel hyperlink to the risk actor’s Tor negotiation website. This website is barebones, solely having a chat panel that can be utilized to barter with the ransomware gang.
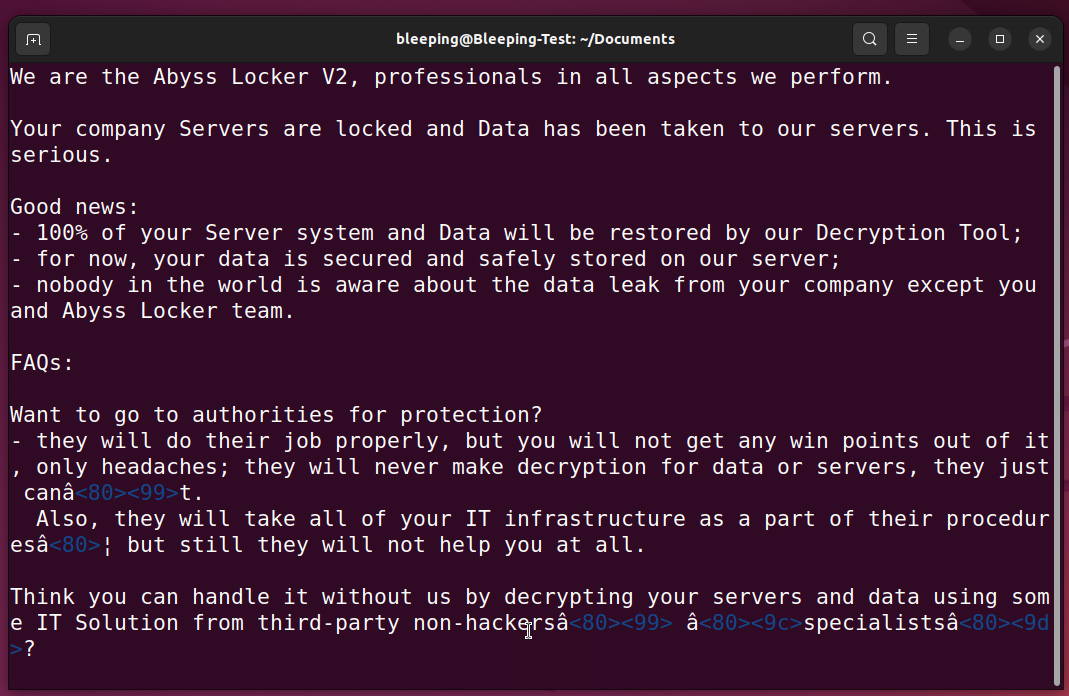
Supply: BleepingComputer
Ransomware knowledgeable Michael Gillespie mentioned that the Abyss Locker Linux encryptor relies on Hey Kitty, utilizing ChaCha encryption as an alternative.
Nonetheless, it’s not identified if it is a rebrand of the HelloKitty operation or if one other ransomware operation gained entry to the encryptor’s supply code, as we noticed with Vice Society.
Sadly, HelloKitty has traditionally been a safe ransomware, stopping the restoration of information at no cost.
