A brand new info stealer malware referred to as MetaStealer has set its sights on Apple macOS, making the most recent in a rising listing of stealer households targeted on the working system after Stealer, Pureland, Atomic Stealer, and Realst.
“Menace actors are proactively focusing on macOS companies by posing as faux shoppers with a view to socially engineer victims into launching malicious payloads,” SentinelOne safety researcher Phil Stokes mentioned in a Monday evaluation.
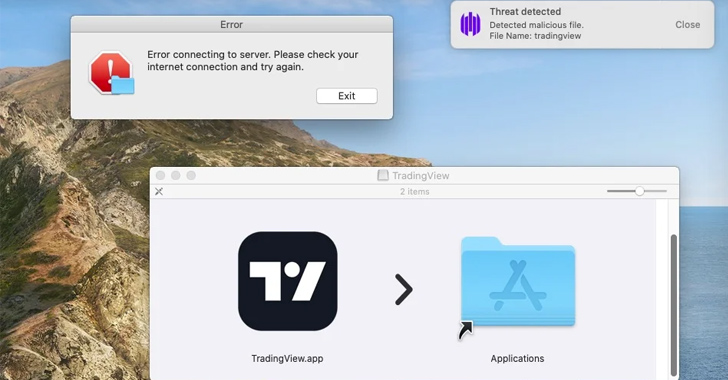
In these assaults, MetaStealer is distributed within the type of rogue utility bundles within the disk picture format (DMG), with targets approached via risk actors posing as potential design shoppers with a view to share a password-protected ZIP archive containing the DMG file.

Different cases have concerned the malware masquerading as Adobe information or installers for Adobe Photoshop. Proof gathered to this point exhibits that MetaStealer artifacts started showing within the wild in March 2023. The newest pattern was uploaded to VirusTotal on August 27, 2023.
“This particular focusing on of enterprise customers is considerably uncommon for macOS malware, which is extra generally discovered being distributed by way of torrent websites or suspicious third-party software program distributors as cracked variations of enterprise, productiveness or different well-liked software program,” Stokes mentioned.
The principle part of the payload is an obfuscated Go-based executable that comes with options to reap information from iCloud Keychain, saved passwords, and information from the compromised host.
Choose variations of the malware have been noticed containing capabilities that doubtless goal Telegram and Meta providers.
SentinelOne mentioned it noticed some MetaStealer variants impersonating TradingView, the identical tactic that has been adopted by Atomic Stealer in current weeks.
Means Too Susceptible: Uncovering the State of the Id Assault Floor
Achieved MFA? PAM? Service account safety? Learn how well-equipped your group really is towards id threats
This raises two prospects: Both the identical malware authors could possibly be behind each the stealer households and have been adopted by completely different risk actors as a consequence of variations within the supply mechanism, or they’re the handiwork of disparate units of actors.
“The looks of one more macOS infostealer this 12 months exhibits the pattern in direction of focusing on Mac customers for his or her information continues to rise in recognition amongst risk actors,” Stokes mentioned.
“What makes MetaStealer notable amongst this crop of current malware is the clear focusing on of enterprise customers and the target of exfiltrating invaluable keychain and different info from these targets. Such high-value information can be utilized to pursue additional cybercriminal exercise or achieve a foothold in a bigger enterprise community.”