
Nearly 90% of enterprises use multiple public cloud supplier, in keeping with Flexera’s 2023 State of the Cloud survey. For enterprise cloud customers, managing their multicloud workloads is the second greatest problem after managing cloud prices. Microsoft Defender for Cloud goals to assist with that.
Companies can already use Microsoft Defender for Cloud to monitor safety settings on AWS and Google Cloud Platform in addition to Azure. Starting August 15, 2023, companies may even have the ability to establish safety dangers and assault paths, scan for secrets and techniques and uncover delicate information saved in Google Cloud. These cloud safety posture administration options had been beforehand solely out there for AWS and Azure and now will apply to all three predominant clouds. Microsoft Defender for Cloud may even activate finest practices from a number of key requirements for AWS, Azure and now GCP robotically.
Leap to:
Get a baseline utilizing the Microsoft cloud safety benchmark
“Quite a lot of our clients aren’t single cloud – it’s actually uncommon,” Microsoft VP of technique for SIEM and XDR Raviv Tamir informed TechRepublic. “Most clients go multicloud as a result of they wish to divide the danger. However then the issue is making use of coverage throughout (these clouds) in a constant approach.”
To assist with that, Microsoft turned its Azure Safety Benchmark right into a cross-platform software, renaming it the Microsoft cloud safety benchmark. The MCSB combines related suggestions from the Middle for Web Safety, the Nationwide Institute of Requirements and Expertise and the Fee Card Business Knowledge Safety Customary or PCI-DSS, Tamir defined.
“It’s a baseline that tries to align throughout these three requirements and take all of the technical elements of it after which let you know form of: How do you measure up vs Azure, and the way do you measure up vs AWS? With the brand new GCP connector, we are able to align that additionally to GCP so you may get all of your three hyperscale clouds in a single go.”
Whereas GCP benchmark protection is in public preview, you possibly can add your GCP surroundings to Microsoft Defender for Cloud and get free useful resource monitoring with these finest practices robotically enabled.
“We do the central baseline, as a result of you possibly can have a coverage, however even translating that into these controls is advanced, as a result of what does it imply (for every cloud)? So we attempt to take that load off you, and we’re doing the coverage centrally.”
Discover vulnerabilities and predict assaults with a graph database
Microsoft has lengthy maintained that defenders suppose when it comes to the lists of their property, whereas attackers suppose in graphs of how techniques are linked to allow them to leap from the preliminary breach into extra useful companies.
With the GCP connector, Microsoft Defender for Cloud can construct a graph database of the whole lot you will have within the cloud throughout AWS, Azure and Google Cloud. Then, you possibly can discover that to know what information you will have and the place you might be attacked. Tamir calls this a “information conscious safety posture” that may discover and defend delicate information.
He added, “We’re taking all the information that we are able to scrape off your GCP buckets, and aligning them onto the property within the graph. All of your property, stock, vulnerabilities and configurations are actually hooked on the property within the graph and linked.”
The information is scanned for delicate information (e.g., bank card particulars, social safety numbers and any customized data varieties you’ve outlined in Microsoft Purview) that you just wouldn’t wish to see misplaced in an information breach. “We’re utilizing the information tagging that comes from the DLP (information loss prevention) facet of the home so you possibly can tag utilizing the identical insurance policies,” he defined. “As we undergo this information, we additionally scan and tag the whole lot we see. And but once more, that’s one other nice layer that will get added to the graph.”
Your cloud servers and Defender Vulnerability Administration containers, if in case you have them, (Determine A) are additionally scanned for secrets and techniques (i.e., credentials corresponding to SSH non-public keys, entry keys and SQL connection strings) that you just shouldn’t retailer within the cloud, in addition to identified vulnerabilities. That gained’t have an effect on the efficiency of these workloads. “To make that graph full, we additionally do agentless scanning as a result of we have to analyze all of the logs and all the information that is available in to counterpoint the graph,” Tamir defined.
Determine A
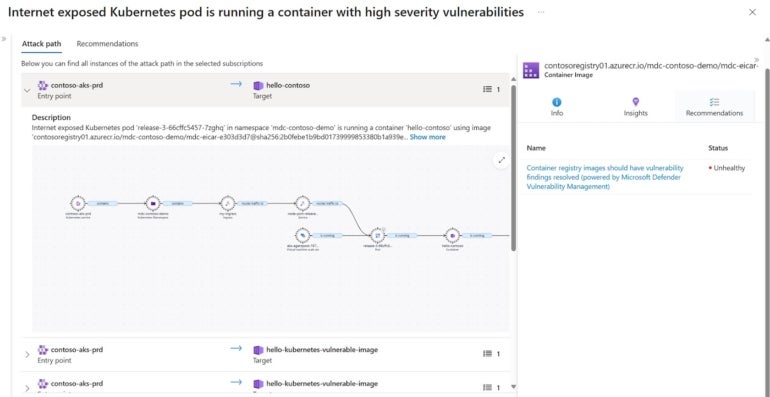
He added, “That each one goes right into a database, and you’ll question that database. We’re providing you with the great interconnected view of the whole lot that you’ve got.”
Placing the completely different items of data collectively like this helps you assess how severe an issue is. When you’ve got a vulnerability in a digital machine that has entry to a service like Azure Key Vault, you’ll wish to prioritize fixing that. Equally, if the vulnerability is in a system that doesn’t have entry to credentials however does have delicate information, you must also care about it.
Assault path evaluation
Exploring the graph as a defender permits you to see all of your sources the way in which an attacker would, however not everybody is aware of what to search for, so Microsoft is constructing instruments to assist safety groups prioritize what wants fixing — the primary is assault path evaluation (Determine B).
Determine B
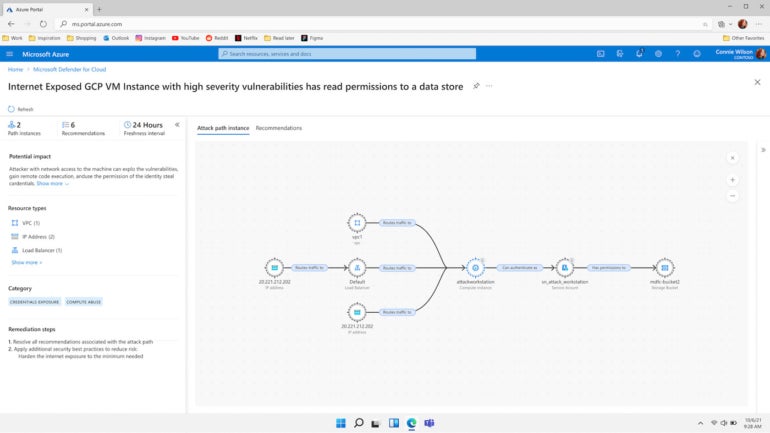
“With out doing any probing and simply based mostly on all the information that we accumulate within the graph, that is telling you the units of attainable assaults, after which we present you what could be the impression of this assault as a result of you will have a susceptible set of VMs which have entry to, say, key storage. “We are able to let you know what the potential consequence is, which helps you deal with the extra vital issues,” Tamir identified. “And sooner or later, this will probably be a foundation for us having the ability to inform the place the assault goes, not simply the place it’s proper now.”
Defend cloud storage with new malware scanning
You don’t simply wish to cease attackers stepping into your cloud storage — you additionally wish to cease them from sneaking malware into your storage.
Historically, storage at relaxation doesn’t get scanned for malware as a result of the idea is the malware can’t execute when it’s sitting in a storage bucket – and if it does find yourself on an endpoint the place it may be run, the defenses there’ll catch it. Microsoft Defender for Cloud can defend a variety of units, however that’s not sufficient to maintain you secure, Tamir warned.
One buyer permits their customers to add data for assist brokers to take a look at to assist them. Tamir famous: “That data is straight away seen by an agent, so the time that spends within the bucket storage earlier than it truly will get consumed is absolutely brief, and the malware authors use it as a approach of distributing malware. And on this case, it was ransomware.”
Different organizations have compliance guidelines like NIST and SWIFT for his or her information governance that imply they should scan all information, however they don’t do it in actual time. Tamir stated, “They’ve been lazy scanning, and so they should arrange all types of their very own infrastructure and pull the information into like a VM after which scan it after which attempt to put it again. We are able to try this for them: We are able to do it faster, we are able to do it with out the hit of efficiency, and we are able to truly do it on add.”
The brand new Malware Scanning in Defender for Storage is for Azure Blob storage solely and will probably be out there from September 1 as an non-compulsory additional for Defender for Storage, costing $0.15 per GB of knowledge scanned.
Tamir stated, “It’s not simply file scanning, it’s not simply hash, it’s not simply IOCs (Indicators of Compromises); we’re truly doing polymorphic scanning.” And whereas the malware scanning is automated and delivered as a service reasonably than infrastructure it’s a must to handle, you possibly can nonetheless select what occurs when malware is detected. He added, “You’ll be able to determine whether or not you simply need us to let you know that it’s unhealthy, otherwise you need us to truly take an motion, otherwise you wish to take the motion elsewhere.”
The place Microsoft Defender for Cloud goes subsequent
Defender for Storage
The following step for malware scanning in Defender for Storage will probably be scanning information extra continuously, not simply after they’re uploaded, to search for malware recognized since then. Tamir recommended, “There are extra polymorphic chains of malware that we uncover on daily basis.” The dimensions of cloud storage makes {that a} problem. “These are actually large buckets; (should you’re) scanning them periodically, you’ll by no means get to the tip, so we have to discover a sensible approach of scanning them, whether or not it’s on entry or another set off.”
How AI and automation might assist
There are additionally much more alternatives to make use of the knowledge within the graph that Defender for Cloud builds to guard clients, making it simpler to keep away from errors within the safety and configuration settings that defend you, and do extra.
“Typically, in Microsoft (merchandise) we’ve quite a lot of locations the place you set insurance policies and never sufficient coordination between them,” Tamir famous. “If I set DLP insurance policies, I wish to set them centrally in a single place – possibly it’s Microsoft Purview. After which I need that to maneuver throughout all of my property, and each enforcement level that I’ve ought to yield to that coverage reasonably than me having to go and set these insurance policies individually.”
Not solely does he need making use of these insurance policies to take rather a lot much less work, however as an alternative of manually checking and making use of the best safety baseline, automation and AI might do extra of the work of setting the best insurance policies within the first place, he recommended.
Tamir added, “With cloud, folks began the best approach, saying as an alternative of coping with issues submit breach, let’s set the configurations proper to start with – after which we discovered that the configuration drawback is simply as huge!”
“This entire notion of shift left that everyone’s speaking about; we nonetheless have quite a lot of handbook steps in it – quite a lot of reasoning folks have to do,” Tamir stated. “I believe there’s a revolution that should are available in two elements. One, there must be extra automation managed stuff than human managed stuff; automation will probably be actually crucial right here as a result of the knowledge density is unimaginable.” The second step will probably be so as to add AI to automation. Tamir acknowledged, “I believe it is going to be a very good problem for issues like generative AI, for reasoning over issues which are advanced within the sense that they appear the identical, however they’re not essentially the identical.”
Tamir concluded, “When folks ask me, can I take my units of compliance which are overlapping, after which inform me what the widespread denominator is for all of them, and what ought to I do to do this? I believe that’s an issue that’s primed nicely for instruments like generative AI.”

